Comprehensive Threat Exposure Management Platform
You already know that running vulnerability scans is a fundamental part of cybersecurity. But what happens after the scan is finished? A long list of potential weaknesses without context is more overwhelming than helpful. A modern vulnerability management system goes far beyond simple scanning. It integrates real-time threat intelligence to show you which vulnerabilities are being actively exploited in the wild. It helps you validate your security controls to ensure they’re actually working as intended. This is about moving from a theoretical checklist to an evidence-based strategy that focuses your team’s efforts on the risks that truly matter to your business.
Think of a vulnerability management system (VMS) as your command center for cybersecurity. It’s a platform designed to continuously find, evaluate, and fix security weaknesses across your entire digital landscape—from your servers and laptops to your cloud applications and network devices. Instead of manually tracking every potential threat, a VMS automates the process, giving you a clear, organized view of your security posture.
This isn’t just about running occasional scans. It’s a cyclical, ongoing process. A solid vulnerability management program helps your team move from putting out fires to proactively strengthening your defenses before an attack ever happens. It provides the structure and tools needed to manage risk systematically, ensuring you’re always aware of where your most critical weaknesses lie and what you need to do about them.
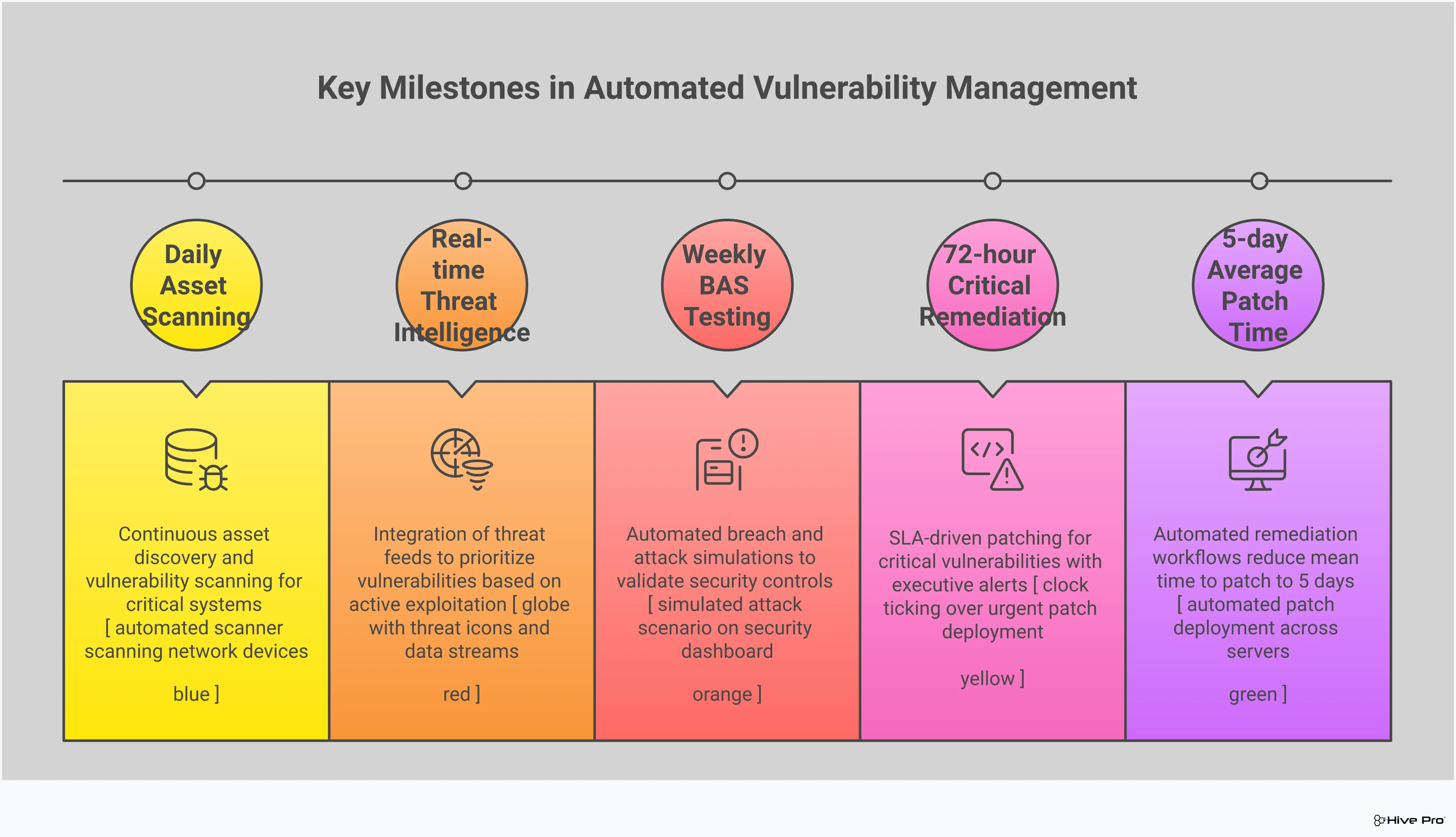
At its heart, a vulnerability management system brings together several key functions to create a unified workflow. It starts with asset discovery, which continuously maps your entire IT environment to ensure you know exactly what you need to protect. From there, vulnerability scanners probe these assets for known weaknesses. Once vulnerabilities are found, the system uses tools like patch management and configuration management to help you apply fixes. Many systems also integrate threat intelligence feeds to add real-world context, helping you understand which vulnerabilities are being actively targeted by attackers. This combination of tools gives you a complete picture, from discovery to remediation.
Implementing a vulnerability management system is about shifting from a reactive to a proactive security stance. By systematically identifying and addressing weaknesses, you drastically reduce your attack surface and lower the risk of a data breach. This proactive approach does more than just protect data; it minimizes system downtime, which saves money and maintains productivity. A strong vulnerability management program also builds trust with your customers and stakeholders by demonstrating a serious commitment to security. It’s the foundation for a resilient security posture, allowing your team to focus on the threats that pose a genuine risk to your organization instead of getting lost in a sea of low-priority alerts.
Think of a vulnerability management system as the central hub for your security posture. It’s not just a tool you run once; it’s a continuous, cyclical process designed to keep your organization safe. The entire workflow is built around a simple but powerful idea: systematically find, evaluate, fix, and report on security weaknesses across your entire digital environment. This proactive loop helps you move from a reactive, fire-fighting mode to a more strategic approach where you’re consistently reducing your threat exposure.
A solid vulnerability management program follows a clear, four-step lifecycle. It starts with knowing what you have, then checking it for weaknesses, deciding which ones to fix first, and finally, making sure the fix actually worked. Each step builds on the last, creating a comprehensive system that gives you a clear view of your security risks and a plan to manage them effectively. This process transforms vulnerability management from a daunting checklist into a manageable and repeatable strategy.
You can’t protect what you don’t know you have. This is the foundational step of any vulnerability management program. Before you can find vulnerabilities, you need a complete and accurate inventory of every asset connected to your network. This includes everything from servers, laptops, and mobile devices to cloud instances, applications, and IoT hardware. A good system automates this discovery process, continuously scanning your environment to create a detailed catalog. This gives you a total attack surface view, ensuring no device is left unmonitored and providing the baseline for all subsequent security activities. Without a comprehensive asset inventory, you’re essentially flying blind.
Once you have a clear picture of your assets, the next step is to scan them for known weaknesses. Vulnerability management systems use powerful scanners to automatically inspect your systems, applications, and networks. These tools check for thousands of potential security flaws, such as missing patches, outdated software versions, weak configurations, and other common vulnerabilities that attackers love to exploit. The system then compiles a detailed report of its findings, listing every vulnerability discovered on each asset. This assessment phase gives you the raw data you need to understand where your security gaps are and what specific threats you’re facing.
After a scan, you might be looking at a list of thousands of vulnerabilities. Trying to fix everything at once is impossible and inefficient. This is where prioritization comes in. A vulnerability management system helps you sort through the noise by scoring each weakness based on its potential impact. While traditional systems rely on the Common Vulnerability Scoring System (CVSS), modern platforms provide a more nuanced, risk-based prioritization. They enrich the data with threat intelligence to highlight which vulnerabilities are actively being exploited in the wild, helping you focus your team’s efforts on the threats that pose a genuine and immediate danger to your organization.
Finding and prioritizing vulnerabilities is only half the battle; you also have to fix them. The final stage in the cycle is remediation and validation. The system helps you manage the fixing process by creating tickets, assigning tasks to the right teams, and tracking their progress. Once a patch or fix has been applied, it’s crucial to verify that it worked. The system performs follow-up scans to confirm that the vulnerability has been successfully resolved and is no longer detectable. This validation step closes the loop, confirms your defenses are stronger, and ensures the cycle can begin again to find any new weaknesses.
Choosing the right vulnerability management system is a big decision. It’s not just about buying a tool; it’s about adopting a platform that becomes a core part of your security strategy. You need a system that does more than just scan for problems—it should give you a clear, actionable path to reducing your risk. A great VMS helps you find your weaknesses, understand which ones truly matter, and fix them efficiently. As you evaluate your options, focus on solutions that provide comprehensive visibility and integrate smoothly into your existing workflows. Look for these key features to make sure you’re getting a system that will actually make your job easier and your organization safer.
You can’t protect what you don’t know you have. That’s why the first thing to look for in any vulnerability management system is its ability to perform complete asset discovery. Your system needs to find and catalog every single device, application, and cloud instance connected to your network. This includes everything from servers and laptops to IoT devices and containerized environments. A comprehensive inventory is the foundation of effective vulnerability management. Without a full picture of your attack surface, you’ll have blind spots where threats can hide. Your chosen platform should continuously map your entire environment, ensuring new assets are discovered as soon as they come online.
Once you know what’s on your network, you need to understand its weaknesses. This is where advanced scanning engines come in. A top-tier VMS uses powerful scanners to automatically check your systems for known vulnerabilities. But it’s not just about running a simple check. Look for a system that offers different types of scans—authenticated and unauthenticated, internal and external—to get a full view of your security posture. The best tools are constantly updated with the latest vulnerability information, ensuring you can detect even newly discovered threats. This capability allows you to move from a reactive stance to a more proactive approach to security.
A typical scan can uncover thousands of vulnerabilities, and trying to fix them all is impossible. This is why risk-based prioritization is non-negotiable. Instead of relying solely on generic CVSS scores, a modern VMS should use real-time threat intelligence to highlight which vulnerabilities are actively being exploited by attackers. This context is crucial. It helps your team focus its limited time and resources on the threats that pose a genuine danger to your organization. By concentrating on the most critical issues first, you can significantly reduce your exposure without getting bogged down by low-risk findings.
Your vulnerability management system shouldn’t operate in a silo. To be truly effective, it needs to integrate seamlessly with the other security tools in your stack. Look for a platform that offers pre-built integrations with your SIEM, ticketing systems, patch management tools, and other key components of your security infrastructure. This connectivity creates a more cohesive and automated security ecosystem. When your tools can share information and trigger actions in one another, you streamline workflows, reduce manual effort for your team, and ensure that critical vulnerability data gets to the right people quickly.
Finding vulnerabilities is only half the battle; fixing them is what truly matters. A great VMS helps you close the loop with automated remediation workflows. The system should not only identify a problem but also provide clear guidance on how to fix it. Look for features that connect vulnerabilities to the correct patches, create remediation tickets automatically, and assign them to the right teams. This automation accelerates your response time and ensures that vulnerabilities are remediated in a consistent, trackable way, which is a core principle of continuous threat exposure management (CTEM).
Finally, you need to be able to communicate your security posture to others. A VMS should provide clear, customizable reporting and intuitive dashboards. Your technical teams need detailed reports to guide their remediation efforts, while executives and board members need high-level summaries that show risk trends and the overall health of the security program. Look for a system that can generate reports tailored to different audiences. These dashboards should provide an at-a-glance view of your most critical vulnerabilities, remediation progress, and compliance status, making it easy to demonstrate the value of your security investments and track your progress over time.
A vulnerability management system on its own is like having a detailed map of your city. It shows you every street and building, but it doesn’t tell you where the traffic jams, accidents, or road closures are happening right now. Adding threat intelligence is like switching to a real-time GPS. Suddenly, you see the live traffic, get alerts about hazards, and can choose the fastest, safest route.
Integrating cyber threat intelligence (CTI) transforms your vulnerability management from a static, compliance-focused checklist into a dynamic, proactive defense strategy. Instead of treating every vulnerability as equally urgent, you can focus your team’s limited time and resources on the threats that pose a genuine, immediate risk to your organization. This context allows you to see which vulnerabilities are being actively exploited in the wild, which ones are part of a trending attack campaign, and which ones are targeting your specific industry. It’s the difference between guessing what an attacker might do and knowing what they are doing.
The core of effective threat intelligence is fresh, relevant data. By integrating real-time threat context into your vulnerability management lifecycle, you can make decisions that meaningfully reduce risk. This isn’t just about getting a list of new CVEs; it’s about understanding the story behind them. High-quality intelligence from sources like HiveForce Labs provides crucial details on threat actor tactics, techniques, and procedures (TTPs), malware signatures, and indicators of compromise (IOCs). This information feeds directly into your VM system, enriching the raw vulnerability data and giving you a clear picture of which issues need your immediate attention versus which can be scheduled for a later patch cycle.
Let’s be honest: you can’t patch everything. The sheer volume of vulnerabilities discovered daily makes a “patch-it-all” approach impossible. This is where threat intelligence helps you cut through the noise. It allows you to focus on the vulnerabilities that truly pose a risk based on real-world exploitation activity. Instead of relying solely on a CVSS score, you can see which vulnerabilities are included in popular exploit kits or are being used by known ransomware groups. This approach, often called risk-based vulnerability prioritization, ensures your team is always working on the fixes that will have the biggest impact on your security posture.
Threat intelligence helps you think like an attacker. It provides clear, up-to-date reports on your security status, showing your team what threats exist in real-time and which of your assets are most likely to be in the crosshairs. For example, a medium-severity vulnerability on a non-critical internal server is a low priority. But if threat intelligence shows that same vulnerability is being used to gain initial access in your industry, and it exists on your internet-facing payment server, it instantly becomes your top priority. Reviewing regular threat advisories helps you understand these attacker trends and pinpoint the specific targets they are likely to focus on within your environment.
Think of your vulnerability management program as building a fortress. You’ve identified weak spots, patched the walls, and set up guards (your security controls). But how do you know if those guards are actually effective against a real attack? That’s where Breach and Attack Simulation (BAS) comes in. Instead of just assuming your defenses will work, BAS lets you safely pressure-test them.
BAS platforms run automated, simulated attacks that mimic the techniques real-world adversaries use. This isn’t about finding more vulnerabilities; it’s about validating that the security measures you already have in place are configured correctly and can stop an attack in its tracks. By adding BAS to your strategy, you shift from a passive, theoretical view of your security posture to an active, evidence-based one. It helps you answer the critical question: “If an attacker tried to exploit this vulnerability right now, would our defenses stop them?” This proactive approach is a core part of modern Threat Exposure Management.
You’ve invested heavily in firewalls, endpoint detection and response (EDR), and other security tools. But are they doing their job? A simple misconfiguration could leave a massive gap in your defenses. BAS tools help you continuously validate your security controls by running simulations of known attack scenarios.
These simulations test whether your tools can detect, alert, and block malicious activity as expected. For example, a BAS platform might simulate a ransomware attack’s lateral movement phase. If your EDR fails to flag the activity, you know you have a critical gap to address. This gives you concrete proof that your security stack is performing as intended, turning your assumptions into certainties.
After your team spends hours patching a critical vulnerability, the final step should be confirming the fix actually worked. A follow-up scan can tell you if the patch was applied, but it can’t always confirm that the underlying risk has been eliminated. This is where BAS provides a clear advantage.
By integrating BAS into your workflow, you can run a targeted simulation that mimics the exact attack path the vulnerability would have enabled. If the simulated attack fails, you have definitive proof that your remediation was successful. This creates a powerful feedback loop, ensuring that your team’s hard work translates directly into a stronger, more resilient security posture. It closes the gap between patching a vulnerability and truly neutralizing the threat.
The threat landscape and your IT environment are constantly in flux. New attack techniques emerge daily, and configuration drift can weaken your defenses over time. A one-and-done penetration test can’t keep up. BAS provides a way to continuously verify that your security posture remains strong against the latest threats.
By running automated simulations on a regular basis, you can ensure your defenses are always optimized. This ongoing validation process helps you catch security gaps caused by system changes or new adversary tactics before an attacker can exploit them. It’s a fundamental practice for maintaining a robust security framework and moving from periodic assessments to a state of continuous assurance, which is a key goal of any CTEM program.
Choosing the right vulnerability management system can feel overwhelming with so many strong options on the market. The best fit for your organization will depend on your specific needs, team size, budget, and existing security stack. To help you get a clearer picture of what’s available, let’s walk through some of the leading platforms. Each one brings a unique approach to the table, from comprehensive exposure management to endpoint-focused protection. Think of this as a starting point to help you identify which solutions might be worth a closer look for your team.
Hive Pro takes a broader view than traditional vulnerability management, positioning its Uni5 Xposure platform as a complete threat exposure management solution. The goal here is to simplify a complex process by giving you a single, clear view of your entire risk landscape. Instead of just listing vulnerabilities, Hive Pro focuses on helping you identify, prioritize, and fix the issues that attackers are most likely to exploit. This proactive approach is designed to help your team stay ahead of threats and move from a reactive to a preventative security posture, ensuring you’re always focused on what matters most.
Tenable is a well-known name in the cybersecurity space, and its Tenable Vulnerability Management platform is built on a simple but powerful principle: know your environment, expose your weaknesses, and close the gaps. The system is designed to continuously scan and identify all your assets—from on-prem devices to cloud resources and web apps—to find hidden vulnerabilities. It’s a comprehensive tool that helps you maintain visibility across your entire attack surface, making sure that even new or temporary assets are accounted for in your security program.
Qualys combines several functions into one with its VMDR (Vulnerability Management, Detection, and Response) platform. This integrated approach means you aren’t just identifying vulnerabilities; you’re also getting the tools to detect threats and respond to them, all within a single solution. It’s built to help teams continuously discover, assess, prioritize, and patch critical vulnerabilities across the entire IT environment. For organizations looking to consolidate their toolset and create a more unified workflow from discovery to remediation, Qualys VMDR offers a compelling, all-in-one package.
If your team thrives on immediate, actionable data, Rapid7 InsightVM is a solution to consider. It provides real-time visibility into the risks across your environment, using live dashboards to present information in a clear and accessible way. The platform goes beyond just scanning by offering features like automated remediation workflows and tight integrations with other security tools. This focus on speed and automation helps security teams cut through the noise, prioritize effectively, and streamline the entire process of fixing vulnerabilities to strengthen their overall security posture.
CrowdStrike takes a different angle by integrating vulnerability management directly into its cloud-native endpoint protection platform, CrowdStrike Falcon. This is an excellent option for organizations that have an endpoint-centric security strategy or are already using other CrowdStrike products. The platform provides deep visibility into vulnerabilities across all your endpoints, from laptops to servers, and helps you prioritize fixes based on risk. By combining endpoint protection with vulnerability management, CrowdStrike offers a unified agent and console to reduce complexity and help teams manage security more efficiently.
Putting a vulnerability management system in place is a huge step forward, but it’s not always a simple plug-and-play solution. Many teams run into similar roadblocks along the way. Knowing what these challenges are ahead of time can help you plan for them and build a more resilient security strategy from day one. The goal isn’t just to install a tool, but to integrate a process that genuinely reduces your threat exposure without burning out your team.
From budget constraints to the sheer complexity of modern IT environments, these hurdles are common. But with the right approach and tools, they are entirely manageable. Let’s walk through some of the most frequent challenges you might face and how to think about them.
Let’s be honest: most security teams are stretched thin. You likely don’t have an army of analysts or an unlimited budget to tackle every single vulnerability your scanner finds. This is one of the biggest reasons vulnerability management programs stall. When you’re faced with a report listing thousands of issues, it’s easy to feel like you’re falling behind. The key isn’t to hire more people to fix everything, but to work smarter. A system that helps you prioritize vulnerabilities based on real-world risk allows your team to focus their limited time and energy on the threats that actually matter to your organization.
Your company’s infrastructure probably isn’t confined to a single, on-premise data center anymore. Today’s environments are a mix of on-premise servers, multiple cloud providers, containers, and serverless functions. This complexity creates a constantly shifting attack surface that’s difficult to track. Traditional scanning tools often struggle to keep up, leaving you with significant blind spots. You need a solution that can provide a unified view of your entire attack surface, no matter where your assets live. This visibility is the foundation for managing vulnerabilities effectively across dynamic and distributed systems.
When your security tools generate a constant stream of alerts, it’s easy for your team to become desensitized. This “alert fatigue” is a serious problem. When analysts are overwhelmed by low-priority notifications, they’re more likely to miss the critical alerts that signal a genuine threat. Your vulnerability management system shouldn’t just add to the noise. Instead, it should help you cut through it by correlating data and highlighting the most urgent risks. This prevents your team from chasing down every minor issue and allows them to concentrate on responding to credible threats that could impact the business.
Your vulnerability management system can’t operate in a silo. To be truly effective, it needs to connect with the other security tools you already use, like your SIEM, ticketing systems, and patch management solutions. Without proper integration, you end up with disconnected data and inefficient, manual workflows. A system with a robust API and pre-built integrations creates a more cohesive security ecosystem. This allows you to automate tasks, share intelligence between tools, and create a single, reliable source of truth for your security posture, making everyone’s job easier.
Even seasoned security pros can get tripped up by a few persistent myths about vulnerability management. These misunderstandings often lead to misaligned strategies, wasted effort, and a false sense of security that can leave your organization exposed. It’s easy to see how they take hold; on the surface, they sound logical. But in practice, they can pull your entire program off course, causing teams to chase the wrong metrics and ignore the real dangers. Let’s clear the air and get everyone on the same page. Moving past these myths is the first step toward building a truly effective program that focuses on what actually matters: reducing your real-world risk. By understanding what vulnerability management isn’t, you can better focus your team’s energy on what it is—a continuous, strategic process for protecting your organization from genuine threats. It’s about working smarter, not just harder, to make a measurable impact on your security posture.
One of the most common mix-ups is treating vulnerability management and patch management as the same thing. While they’re related, they are far from interchangeable. Think of patch management as one tool in your toolbox—a critical one, for sure, but still just one tool. It’s the act of applying updates to fix known flaws. Vulnerability management is the entire strategic process: discovering your assets, identifying all kinds of weaknesses (not just ones with patches), assessing the risk they pose to your specific environment, and then deciding on the best way to handle them. Sometimes that’s patching, but it could also involve configuration changes or network segmentation. Confusing the two is a dangerous oversimplification that leaves you blind to a whole class of risks.
The idea of fixing every single vulnerability sounds great in a perfect world, but in reality, it’s an impossible goal that can burn out your team. Chasing a “clean” scan report with zero vulnerabilities is a recipe for frustration. Not all vulnerabilities are created equal. Many have a low or theoretical risk and may not even be exploitable in your environment. A successful program isn’t about eliminating every flaw; it’s about managing risk intelligently. The real goal is to focus your limited time and resources on the vulnerabilities that pose a genuine threat to your business. This means prioritizing fixes that deliver the biggest impact on your overall security posture, rather than spinning your wheels on low-risk issues.
Relying solely on the Common Vulnerability Scoring System (CVSS) for prioritization is another trap many teams fall into. While CVSS scores provide a standardized, high-level look at a vulnerability’s potential severity, they lack critical context. A CVSS score doesn’t know how important an asset is to your business, whether you have other security controls in place, or—most importantly—if attackers are actively exploiting that vulnerability in the wild. A “critical” vulnerability on a non-essential, isolated server might be less of a priority than a “medium” one on your primary customer database. To truly understand your risk, you need to enrich CVSS data with real-time threat intelligence and business context. This helps you see which vulnerabilities are not just theoretically bad, but are a clear and present danger to your organization.
Choosing the right vulnerability management system is a balancing act. You need a platform that delivers powerful performance without overstretching your budget. It’s not just about the initial price tag; it’s about finding a solution that provides long-term value by fitting your team’s workflow, integrating with your existing tools, and accurately identifying the risks that matter most. Let’s break down the key factors to weigh when comparing your options.
Vulnerability management platforms come with a variety of pricing structures, so it’s important to find one that aligns with your organization’s scale and budget. Many modern solutions have moved away from outdated IP-based pricing. Instead, you’ll often find models based on the number of assets you need to cover, which can include everything from employee laptops and servers to cloud resources and web applications. As you evaluate costs, think about how they will scale as your company grows. Ask about potential hidden fees for implementation, training, or premium support to get a complete picture of the total investment required.
A powerful tool is only effective if your team can actually use it. A complicated interface or clunky workflow can lead to frustration and slow down response times. Look for a system with a clean, intuitive dashboard that gives you a clear view of your security posture at a glance. The platform should be simple to set up and manage, allowing your team to focus on fixing vulnerabilities, not fighting with the software. A great user experience means less time spent on training and more time dedicated to reducing risk and securing your environment.
Your vulnerability management system shouldn’t be an island. To be truly effective, it needs to connect easily with the tools you already use every day. Strong integration capabilities are essential for creating a smooth, automated workflow. Check if the platform can connect to your ticketing systems, like JIRA, to automatically assign remediation tasks to the right teams. It should also work with your SIEM and other security tools to share data and provide a more unified view of your security landscape. A robust API is a great sign that a system is built to be a team player in your security stack.
The core function of any VM system is to find weaknesses, and its performance here is non-negotiable. This comes down to two key elements: coverage and accuracy. Your system needs to provide total attack surface management to ensure no asset is left unscanned, whether it’s on-premises, in the cloud, or part of your web applications. At the same time, accuracy is critical. A scanner that produces too many false positives will waste your team’s valuable time, while one that misses real threats leaves you dangerously exposed. Look for a solution with a constantly updated vulnerability database to ensure it can spot the latest threats.
Choosing the right vulnerability management system is a huge step, but the real work begins with implementation. A successful rollout isn’t just about flipping a switch; it’s about weaving the system into the fabric of your security operations. It requires a thoughtful strategy that combines clear workflows, smart automation, and a well-prepared team. When you get this part right, you move beyond simply owning a tool and start building a resilient, proactive security program. The goal is to create a sustainable cycle of discovery, prioritization, and remediation that strengthens your defenses over time. Without a solid implementation plan, even the most advanced platform can become another source of alert fatigue, creating more noise than signal. A successful implementation ensures the system integrates smoothly with your existing tools, your teams know how to collaborate within the platform, and you have clear metrics to measure success. It’s the difference between having a list of vulnerabilities and having a clear, actionable plan to reduce your overall risk. Let’s walk through the key steps to make sure your VM system delivers on its promise from day one.
Before you even run your first scan, map out your entire vulnerability management lifecycle. This isn’t a one-time project; it’s a continuous process that needs a clear, repeatable workflow. Define who is responsible for each step, from identifying new assets and initiating scans to validating patches. Establish service-level agreements (SLAs) for remediation so everyone understands the timelines for fixing critical, high, medium, and low-risk vulnerabilities. Documenting these processes ensures consistency, creates accountability, and makes it easier to onboard new team members. A well-defined workflow turns reactive firefighting into a structured, predictable security function.
Your security team’s time is too valuable to be spent on manual, repetitive work. A modern VM system should handle the heavy lifting for you. Lean on automation to schedule regular asset discovery scans, assign remediation tickets to the right teams, and generate reports for stakeholders. Many platforms can automate fixes or integrate with patching tools to streamline the remediation process. By automating these routine tasks, you free up your analysts to focus on more complex challenges, like investigating novel threats and improving your overall security posture. This not only improves efficiency but also reduces the risk of human error.
Your vulnerability management system is your first line of defense, so it needs to be in top shape. This means keeping the platform itself, along with its scanning engines and vulnerability databases, constantly updated. New vulnerabilities are discovered daily, and your system needs the latest information to detect them accurately. This also includes your approach to patch management, which is a critical component of your VM program. Regularly applying security patches to your operating systems, applications, and network devices is one of the most effective ways to close security gaps before they can be exploited by attackers.
A powerful tool is only effective in the hands of a skilled user. Vulnerability management is a team effort that often involves collaboration between security analysts, IT operations, and developers. Invest in training to ensure everyone understands their role in the process and knows how to use the VM system effectively. Provide ongoing education on emerging threats and new platform features. When your team is confident and knowledgeable, they can get the most value out of your investment, respond to threats faster, and work together more seamlessly to protect your organization.
My team is overwhelmed with alerts. How does a vulnerability management system help with that instead of just adding more noise? That’s a great question because it gets to the heart of what a modern system should do. A good platform isn’t just another alert cannon. Its main job is to cut through the noise by giving you context. Instead of just showing you a list of 10,000 potential issues, it uses threat intelligence to highlight the handful of vulnerabilities that are actively being exploited by attackers right now. This allows your team to stop chasing down low-risk problems and focus their limited time on the threats that pose a genuine danger to your business.
Is the goal of vulnerability management to fix every single vulnerability we find? Not at all. In fact, trying to fix everything is a common mistake that leads to burnout and inefficiency. The real goal is to manage and reduce risk in an intelligent way. Many vulnerabilities have a low or even theoretical risk and may not be exploitable in your specific environment. A successful program focuses on prioritizing the weaknesses that are most likely to be targeted and would cause the most damage. It’s about making the biggest impact on your security posture with the resources you have.
We already have a firewall and EDR. Why do we also need Breach and Attack Simulation (BAS)? Think of it this way: your firewall and EDR are your security guards. You’ve hired them and put them in place, but how do you know they’re awake and doing their job correctly? Breach and Attack Simulation is like running a safe, controlled drill to test them. It doesn’t look for new vulnerabilities; it checks if your existing security tools can actually detect and block the techniques attackers use. BAS helps you find gaps in your defenses caused by misconfigurations, ensuring your security investments are actually working as expected.
How is a vulnerability management program different from just running regular vulnerability scans? Running a scan is just one step in the process, like taking an inventory of ingredients. A full vulnerability management program is the entire recipe. It’s a continuous cycle that includes discovering all your assets, scanning them for weaknesses, prioritizing the results based on real-world risk, managing the remediation process to ensure fixes are applied, and then validating that the fix worked. A scan gives you data; a program turns that data into a structured plan that measurably reduces your exposure.
Why can’t we just rely on CVSS scores to prioritize what to fix? CVSS scores are a useful starting point, but they don’t tell the whole story. A CVSS score is a static, theoretical rating of a vulnerability’s potential severity. It doesn’t know if that vulnerability exists on your most critical server or a non-essential test machine. More importantly, it doesn’t tell you if attackers are actively using that vulnerability in the wild. A “medium” severity flaw on an internet-facing system that is part of a known ransomware campaign is far more urgent than a “critical” one that is difficult to exploit and has no known attacks associated with it.