Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Every unpatched vulnerability is more than just a technical flaw; it’s a direct business risk. These security gaps are the entry points for breaches that lead to devastating financial losses, operational downtime, and long-term damage to your brand’s reputation. When viewed through this lens, vulnerability management transforms from a simple IT chore into a critical business function. To get the resources and buy-in you need from leadership, you must demonstrate how your efforts protect the bottom line. This guide will show you how. We’ll cover the key vulnerability management best practices that help you align security work with business objectives, enabling you to clearly communicate risk and prove the value of your program.
At its core, vulnerability management is the continuous process of finding, evaluating, and fixing security weaknesses across your organization’s digital landscape. Think of it as the essential, ongoing maintenance that keeps your systems secure. These weaknesses, or vulnerabilities, can pop up anywhere—from a server running outdated software to a misconfigured cloud application. Without a solid plan to manage them, you’re essentially leaving doors and windows open for attackers to walk right in.
A strong vulnerability management program helps you shift from a reactive, “firefighting” mode to a proactive security posture. Instead of scrambling to patch a vulnerability after it’s been exploited, you can systematically identify and address risks before they become major incidents. This isn’t just about running occasional scans; it’s a cyclical process that involves discovering your assets, identifying their flaws, prioritizing what to fix first, and confirming that the fixes actually worked. By making this a core part of your security strategy, you build a more resilient defense and can confidently answer the question, “Are we secure?”
Leaving vulnerabilities unmanaged is one of the biggest gambles a company can take. These security gaps are a primary cause of cyberattacks and data breaches, serving as the most common entry points for threat actors. The consequences go far beyond a technical headache for your IT team. A successful breach can lead to devastating financial losses, operational downtime that grinds your business to a halt, and long-term damage to your brand’s reputation.
The financial impact alone is staggering. The global cost of cybercrime is projected to climb from $9.22 trillion in 2024 to $13.82 trillion by 2028. Each unpatched vulnerability is a potential contributor to that statistic. For your organization, this translates into the high costs of incident response, regulatory fines, and potential legal action. More importantly, it can erode the trust you’ve built with your customers, which is often the hardest thing to win back.
A successful vulnerability management program is built on more than just technology—it requires a clear strategy and process. The typical lifecycle follows five key steps: discovering all your assets, prioritizing vulnerabilities based on risk, remediating the issues, validating the fixes, and reporting on your progress. This framework ensures you’re not just randomly patching but are methodically reducing your overall risk exposure.
To make this cycle work, you need a few key components in place. First, you need clear policies that define roles, responsibilities, and timelines for remediation. Second, you need the right tools, like a platform that provides continuous scanning and a unified view of cyber risks in a single place. Finally, and perhaps most importantly, you need strong support from company leadership to ensure the program gets the resources and authority it needs to be effective.
A strong vulnerability management program isn’t a one-off project; it’s a continuous cycle. Think of it as a loop that constantly refines your security posture, helping your team stay ahead of threats instead of just reacting to them. This lifecycle provides a structured approach to systematically find, assess, and fix weaknesses across your entire environment. By breaking the process down into five distinct steps, you can create a repeatable, manageable workflow that turns a mountain of security data into a clear, actionable plan. Following this lifecycle is the key to moving from a reactive state of putting out fires to a proactive strategy of preventing them in the first place. It ensures that your efforts are focused, efficient, and genuinely reducing your organization’s risk over time.
You can’t protect what you don’t know you have. That’s why the first step is always discovery. This means creating and maintaining a complete, up-to-date inventory of every single asset connected to your network. We’re talking servers, laptops, mobile devices, cloud instances, applications, and IoT devices—everything. This process is crucial for uncovering “shadow IT” or forgotten legacy systems that could be exposing you to risk without your knowledge. A comprehensive asset inventory is the foundation of your entire program, giving you a clear picture of your total attack surface and ensuring no potential entry point is left unchecked. Without this complete visibility, you’re essentially flying blind.
Once you have a handle on all your assets, it’s time to find out where the cracks are. This step involves using automated scanners and other tools to systematically check each asset for known vulnerabilities. These scans compare the configurations and software versions on your systems against a massive database of documented weaknesses. To be effective, scanning can’t be a once-a-quarter activity. New vulnerabilities are discovered daily, so you need a continuous scanning schedule to catch them as they appear. This gives your team a real-time view of the security flaws in your environment, providing the raw data needed for the next, crucial step in the cycle.
A vulnerability scan can easily return thousands of findings, and trying to fix everything at once is a recipe for burnout. That’s why prioritization is so important. Not all vulnerabilities pose the same level of threat to your organization. Instead of just relying on a generic CVSS score, effective vulnerability and threat prioritization considers real-world context. Is this vulnerability being actively exploited in the wild? Does it exist on a critical, customer-facing server? Answering these questions helps you filter out the noise and focus your team’s limited time and resources on the handful of issues that represent a genuine, immediate danger to your business.
With a prioritized list in hand, you can create a targeted plan of attack. This step involves deciding how to handle each critical vulnerability. While applying a patch is the most common solution, it’s not the only one. Remediation can also involve changing a system configuration, implementing a compensating control (like a firewall rule), or, in some cases, formally accepting a low-level risk. The key is to define the specific actions needed, assign ownership to the right team members, and set clear deadlines for getting the fix in place. This creates accountability and turns your prioritized list into a concrete work plan.
The job isn’t done until you’ve confirmed the fix actually worked. The final step in the lifecycle is to validate your remediation efforts. This means re-scanning the asset to ensure the vulnerability is truly gone and that the patch or configuration change didn’t accidentally introduce a new problem. For critical systems, you might even perform adversarial exposure validation to simulate an attack and confirm the weakness can no longer be exploited. This step closes the loop, providing proof that your team’s work has successfully reduced risk and strengthened your defenses. It’s the final quality check that ensures your program is delivering real results.
When your vulnerability scans return thousands of results, figuring out what to fix first can feel impossible. The secret isn’t to work faster; it’s to work smarter. Effective prioritization means cutting through the noise to focus on the handful of threats that pose a genuine risk to your organization. It’s about shifting from a reactive, “patch everything” mindset to a proactive, risk-based strategy.
A risk-based approach moves beyond just the technical severity of a flaw. Instead, it helps you focus on the vulnerabilities that pose the greatest danger to your business. This method considers multiple factors: How likely is an exploit? What’s the business impact if this system is compromised? How critical is the affected asset? By answering these questions, you can create a priority list that reflects actual business risk, ensuring your team spends its limited time and resources on the fixes that truly matter for vulnerability and threat prioritization.
The Common Vulnerability Scoring System (CVSS) is a great starting point, but it shouldn’t be your only one. A CVSS score of 9.8 looks scary, but it lacks context. If that vulnerability exists on an isolated, internal development server, it’s likely less of a priority than a flaw with a score of 7.5 on your primary, customer-facing application. Relying solely on CVSS scores can lead you to waste time on low-impact issues while more significant threats fly under the radar. Always view scores as one piece of a much larger puzzle.
Every organization is unique, and your prioritization strategy should be, too. What are your most critical assets—the “crown jewels” of your business? Is it customer data, intellectual property, or the e-commerce platform that drives all your revenue? Understanding your specific total attack surface and what’s most valuable to your operations is key. By mapping vulnerabilities to your critical assets, you can clearly see which threats could cause the most damage, allowing you to align your security efforts directly with your business objectives.
A vulnerability is only a theoretical problem until an attacker decides to exploit it. That’s where real-time threat intelligence becomes a game-changer. By integrating data on which vulnerabilities are being actively exploited in the wild, you can instantly elevate the priority of those threats. This intelligence, often curated by research teams like HiveForce Labs, gives you a direct line of sight into attacker trends. It helps you focus on the clear and present dangers, rather than getting distracted by vulnerabilities that aren’t currently being weaponized.
Knowing the theory behind vulnerability management is one thing, but putting it into practice is where the real work begins. Building a strong program means creating repeatable, scalable processes that fit into your team’s daily operations. It’s about moving from a reactive state of putting out fires to a proactive stance where you can anticipate and neutralize threats before they cause damage. These best practices are designed to be practical and straightforward, giving you a clear path to strengthen your security posture. They aren’t just abstract ideas; they are the building blocks of a mature security strategy that can adapt to an ever-changing threat landscape. By focusing on these core areas—from gaining full asset visibility to embedding security into your development pipeline—you can create a more resilient, efficient, and effective vulnerability management program that protects your organization from the inside out. This is how you transform cybersecurity from a series of urgent responses into a confident, proactive discipline that adds real value to the business by safeguarding its most critical assets and operations.
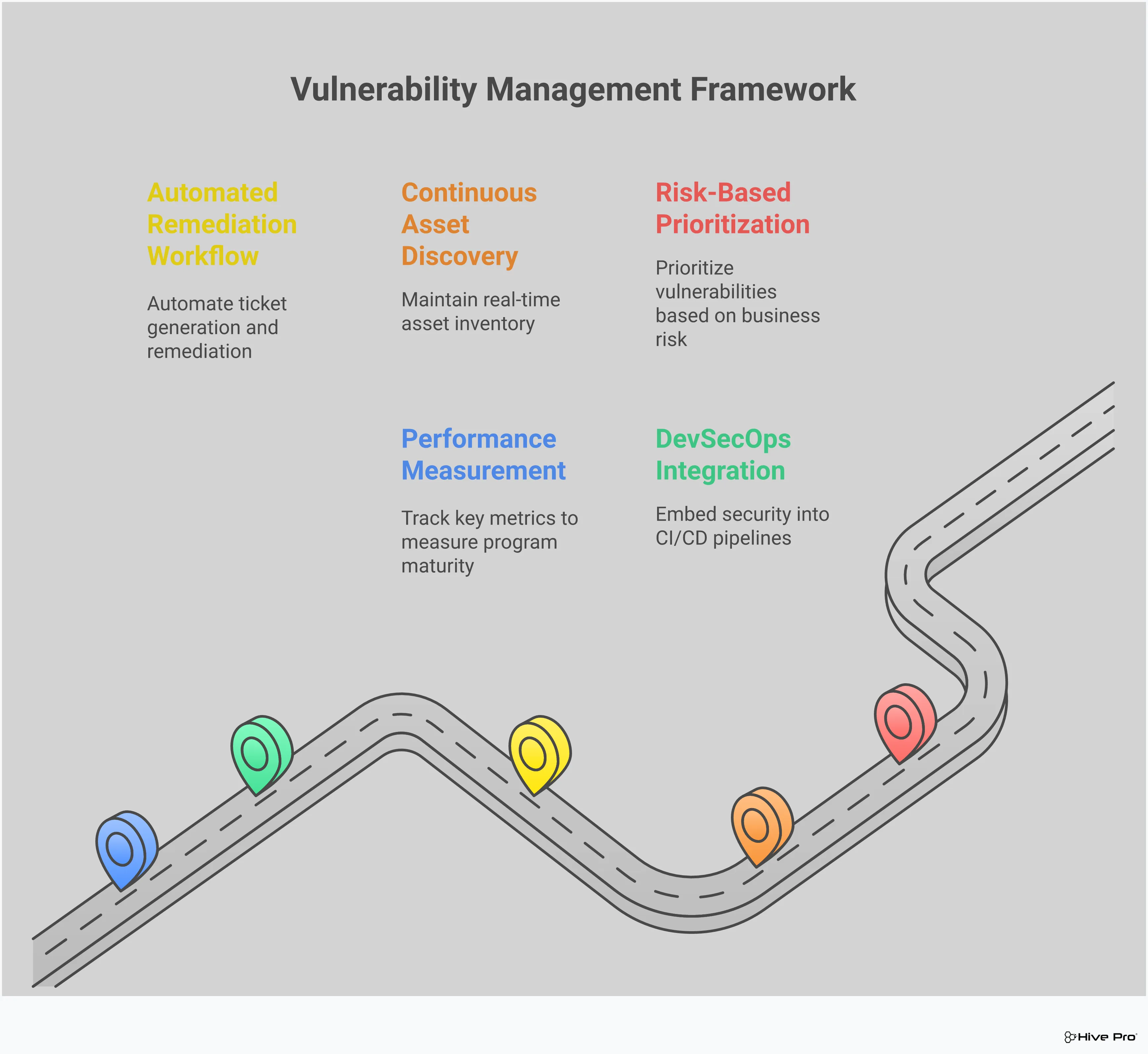
You can’t protect what you don’t know you have. This might sound like a cliché, but it’s the absolute foundation of any solid security program. Many organizations operate with an incomplete picture of their assets, leaving blind spots that attackers are quick to find. Shadow IT, forgotten legacy systems, and misconfigured cloud instances all contribute to an expanding and often invisible attack surface. Achieving total attack surface management is the first step to closing these gaps. By implementing continuous asset discovery and maintaining a comprehensive inventory, you create a single source of truth. This complete visibility allows you to apply security policies consistently and ensures no vulnerability goes unnoticed simply because the asset wasn’t on the books.
In a dynamic IT environment where new assets are spun up and code is deployed daily, annual or quarterly scans are no longer enough. A vulnerability that appears the day after a scan could leave you exposed for months. Continuous scanning shifts your program from taking periodic snapshots to creating a real-time video stream of your security posture. This approach allows you to identify new weaknesses almost as soon as they appear. As noted by security experts, continuous scanning helps organizations allocate resources effectively, focusing on the most current and relevant threats. It ensures your team is always working with the latest data, making your entire vulnerability management process more agile and responsive.
When a critical vulnerability is found, the last thing you need is confusion about who does what. Without a clear plan, remediation can devolve into a chaotic scramble, wasting valuable time while your organization remains at risk. Standardizing your remediation workflows brings order to this process. Create a clear, step-by-step plan that outlines who is responsible for each task, sets realistic deadlines, and defines how fixes will be verified. This documented process ensures everyone understands their role and establishes accountability. It transforms remediation from a reactive fire drill into a predictable, measurable, and efficient operation, which is essential for reducing your overall risk consistently.
Your vulnerability database should be the central nervous system of your security program, but its value depends entirely on the quality of the data it holds. It’s not enough to just pull in a list of CVEs. To make smart decisions, you need context. This means enriching your vulnerability data with real-time threat intelligence, information on active exploits, and the business criticality of the affected assets. By using a platform that provides up-to-date threat advisories, you can better assess the severity and likelihood of a vulnerability being exploited. This allows you to prioritize remediation efforts effectively, ensuring your team focuses on the threats that pose a genuine risk to your organization first.
Vulnerability management is a team sport. The security team can identify weaknesses, but it’s often the IT operations and development teams who need to implement the fixes. When these teams operate in silos, friction and delays are inevitable. Fostering a culture of collaboration is key to a successful program. As security leaders at Wiz point out, developers, engineers, and security teams must work closely together to understand risks, prioritize tasks, and remediate vulnerabilities faster. You can encourage this by creating shared dashboards, integrating communication tools, and holding regular cross-functional meetings to review progress and remove roadblocks. When everyone shares ownership of security, the entire process becomes smoother and more effective.
Finding a vulnerability in a production system is expensive and disruptive to fix. The most efficient way to handle software vulnerabilities is to catch them before they ever make it to production. This is the core idea behind “shifting left”—integrating security into the earliest stages of the development lifecycle. By making vulnerability scanning a standard part of your CI/CD pipeline, you empower developers to find and fix issues in their code immediately. This approach not only reduces your attack surface but also builds a stronger security culture within your development teams. Integrating security into DevOps makes it a core part of the software creation process, leading to more secure applications from the start.
Trying to manage vulnerabilities manually is like trying to empty the ocean with a bucket. The sheer volume of assets, alerts, and patches makes it impossible to keep up. This is where automation becomes your most valuable player. By automating the repetitive, time-consuming parts of your vulnerability management program, you free up your team to focus on the strategic work that truly reduces risk. Instead of drowning in data, you can make informed, proactive decisions. A modern threat exposure management platform uses automation not just to speed things up, but to make your entire security process smarter and more effective. It’s about working more efficiently, not just harder.
You can’t secure what you don’t know you have. The first step in any solid automation strategy is to get a complete and continuous picture of your environment. Manual asset inventories and periodic scans are relics of the past; they leave you with blind spots that attackers are quick to find. Automated discovery tools continuously scan your entire network—from on-prem servers to cloud instances and IoT devices—to maintain a real-time asset inventory. This gives you the total attack surface management needed to see your organization as an attacker would. By implementing continuous scanning, you can allocate resources more effectively and ensure no asset is left unprotected.
Once you have visibility, the next challenge is figuring out what to fix first. Drowning in a sea of “critical” vulnerabilities without context leads to alert fatigue and inaction. This is where AI-powered prioritization changes the game. Instead of relying solely on static CVSS scores, AI can analyze dozens of factors in real-time. It considers whether a vulnerability is actively being exploited in the wild, which business-critical assets are affected, and what other security controls you have in place. This intelligent vulnerability and threat prioritization helps you focus on the handful of risks that pose a genuine, immediate threat to your organization, ensuring your team’s efforts have the greatest impact.
Finding a vulnerability is one thing; getting it fixed is another. Automation can bridge the gap between your security and IT teams by streamlining the entire remediation process. You can set up workflows that automatically create and assign tickets in systems like Jira or ServiceNow, complete with all the context and remediation guidance the IT team needs. This establishes clear ownership and accountability, drastically reducing your mean time to remediate (MTTR). Automating these handoffs eliminates manual back-and-forth, ensures nothing falls through the cracks, and creates a consistent, repeatable process for patching and validation.
Your digital environment is constantly changing, and so is the threat landscape. A vulnerability management program isn’t a one-time project; it’s a continuous cycle. Automation enables the constant monitoring required to maintain a strong security posture over time. It ensures that as new assets come online or new threats emerge, they are identified and assessed immediately. This provides a real-time, accurate view of your organization’s risk level. With continuous adversarial exposure validation, you can also automatically test your security controls against emerging threats, ensuring your defenses work as expected and giving you confidence in your ability to respond quickly.
Even with a solid plan, you’re bound to run into a few challenges. It’s a normal part of strengthening any security program. The key is to anticipate these hurdles so you can move past them without losing momentum. From tight budgets to information overload, security teams face similar issues when trying to get their vulnerability management programs off the ground. Let’s walk through some of the most common roadblocks and, more importantly, how you can get around them.
It often feels like you’re asked to protect a fortress with a skeleton crew and a shoestring budget. You’re not alone—one report found that 56% of organizations see budget constraints as a major barrier. To get past this, you need to frame vulnerability management as a business investment, not just a technical cost. Show leadership the direct line between proactive remediation and reduced financial risk from breaches. Use a platform that automates manual tasks, allowing your team to do more with less. By focusing on the most critical threats, you can direct your limited budget and resources where they’ll have the greatest impact, demonstrating clear ROI.
Finding and retaining cybersecurity talent is tough, and a skills shortage can leave your team feeling stretched thin. Instead of searching for a unicorn candidate who knows everything, focus on empowering the team you have. The right tools can act as a force multiplier, providing clear, guided remediation steps and automating complex analysis. This frees up your experts to focus on strategic initiatives instead of getting bogged down in repetitive tasks. You can also supplement your team’s expertise with external threat intelligence from research teams like HiveForce Labs, which provides the context you need to understand and act on emerging threats without requiring an in-house research division.
Your security tools should work together, not create more silos. If your vulnerability scanner, ticketing system, and asset inventory don’t talk to each other, your team is stuck manually piecing together data, which is slow and prone to error. The solution is to build your program around a central platform that integrates with your entire ecosystem. A threat exposure management platform like Uni5 Xposure can pull data from your existing tools, creating a single, unified view of your risk. This breaks down silos and ensures everyone is working from the same playbook, streamlining communication and remediation efforts.
Modern environments generate a staggering amount of vulnerability data. Without a way to filter out the noise, your team can quickly become overwhelmed, leading to alert fatigue where critical issues get missed. The answer isn’t less data; it’s better intelligence. Stop focusing on the sheer number of vulnerabilities and start focusing on actual risk. A smart vulnerability and threat prioritization engine can automatically analyze factors like asset criticality, real-world exploitation, and threat actor activity. This helps you pinpoint the handful of vulnerabilities that pose a genuine threat to your organization so you can fix what matters first.
You can’t protect what you don’t know you have. With cloud services, remote work, and IoT devices, the modern attack surface is constantly changing, making it easy for shadow IT and unmanaged assets to slip through the cracks. A foundational step is to implement a continuous total attack surface management process. This goes beyond scheduled scans to provide an always-on, comprehensive view of all your assets—from on-prem servers to cloud containers. By gaining complete visibility, you can ensure your vulnerability management program covers your entire environment, not just the parts that are easy to see.
You can’t improve what you don’t measure. Running a vulnerability management program without tracking its performance is like driving without a destination—you’re busy, but you aren’t making real progress. To show the value of your work and make smart decisions about where to focus your efforts, you need to define what success looks like and track your progress toward it. This isn’t just about generating reports; it’s about understanding your security posture and proving to leadership that your investments are paying off by reducing tangible risk.
Measuring your program’s effectiveness helps you answer critical questions: Are we getting faster at fixing critical issues? Is our overall risk level actually going down? Are our tools and processes working as they should? By establishing a baseline and consistently tracking key metrics, you can move from a reactive cycle of firefighting to a proactive strategy that strengthens your defenses over time. It transforms vulnerability management from a technical chore into a strategic business function. The following metrics will give you a clear picture of how your program is performing and where you can make meaningful improvements.
First things first, you need to decide what you’re going to measure. Vulnerability management metrics are the specific Key Performance Indicators (KPIs) that show how well your program is running. Think of them as your program’s vital signs. Instead of tracking everything, focus on a handful of metrics that align with your organization’s security goals. Good starting points include scan coverage (are you scanning all your assets?), vulnerability age (how long do vulnerabilities linger?), and the number of open critical vulnerabilities. These KPIs provide a clear, data-driven view of your program’s health and help you pinpoint areas that need more attention.
The ultimate goal of any vulnerability management program is to reduce the organization’s overall risk exposure. This means looking beyond the sheer number of patched vulnerabilities and focusing on their impact. Are you closing the security gaps that attackers are most likely to exploit? By assessing the severity and potential business impact of each vulnerability, you can prioritize remediation efforts to tackle the most critical threats first. Tracking your risk score over time provides a powerful visual of your program’s success. Seeing that score consistently trend downward is a clear sign that your strategy is working and your organization is becoming more secure.
Time-to-remediate, often called Mean Time to Remediate (MTTR), measures the average time it takes your team to fix a vulnerability after it’s been discovered. This is a critical indicator of your program’s efficiency. A long remediation time leaves a wider window of opportunity for attackers to strike. By tracking this metric, especially for high-severity vulnerabilities, you can identify bottlenecks in your workflow. Maybe your patching process is too slow, or perhaps teams aren’t communicating effectively. Improving your remediation framework and shortening this timeline directly reduces your exposure and strengthens your security posture.
It’s important to be honest about where your vulnerability management program currently stands. Is it a basic, compliance-focused exercise, or is it a mature, proactive part of your overall security strategy? Many organizations start by focusing on meeting compliance requirements for standards like PCI DSS or HIPAA. While that’s a necessary step, a mature program goes further. It integrates with business objectives, uses real-time threat intelligence, and fosters a culture of security across the entire organization. Regularly assessing your program’s maturity helps you identify gaps and create a roadmap for continuous improvement.
Even the most well-intentioned vulnerability management programs can stumble. Knowing the common pitfalls is the first step to avoiding them, helping you build a more resilient and effective security posture. Many teams struggle with the same challenges, from over-relying on outdated metrics to letting communication breakdowns derail their efforts. Let’s walk through some of the most frequent mistakes security teams make and discuss how you can steer clear of them to keep your program on track and focused on what truly matters: reducing exposure.
It’s easy to fall into the trap of chasing a high CVSS score, but this number rarely tells the whole story. The Common Vulnerability Scoring System (CVSS) is a standardized framework, but it lacks critical context. It doesn’t know which assets are crown jewels for your business, nor does it account for whether a vulnerability is actively being exploited in the wild. This can lead to a dangerous disconnect where your team spends valuable time patching a “critical” vulnerability on a non-essential development server while a lower-scored, but easily exploitable, flaw on a production database goes unnoticed. True vulnerability and threat prioritization requires layering CVSS data with real-world threat intelligence and business impact to see the actual risk.
Your security is only as strong as your visibility. In complex environments, it’s common for legacy systems, forgotten servers, and unsanctioned cloud instances (shadow IT) to fall off the radar. These assets are rarely patched or monitored, making them low-hanging fruit for attackers. An attacker doesn’t care if a server is officially part of your inventory; if it’s connected to your network, it’s a potential entry point. This is why achieving total attack surface management is so crucial. You can’t protect what you don’t know you have, so continuous asset discovery is a foundational step that prevents these hidden risks from turning into major breaches.
In the race to remediate, the temptation to deploy a patch immediately can be strong. However, skipping a thorough testing process can cause more problems than it solves. A hastily deployed patch can break critical applications, disrupt business operations, or even introduce new, unforeseen vulnerabilities. The best practice is to always test patches in a controlled, sandboxed environment that mirrors your production setup before rolling them out across the organization. This ensures the fix works as intended without causing collateral damage. A structured patch management process confirms that your solution is both effective and stable, protecting your systems from the vulnerability and from the fix itself.
Vulnerability management is a team sport, not a solo mission for the security department. One of the most common failure points is a breakdown in communication between security, IT operations, and development teams. When security identifies a vulnerability, they need a clear and efficient way to hand it off to the team responsible for remediation. Without shared goals, agreed-upon service-level agreements (SLAs), and integrated workflows, tickets get lost, remediation stalls, and risk lingers. Fostering a culture of collaboration where everyone understands their role and feels a shared sense of ownership is essential for closing vulnerabilities quickly and effectively.
If it isn’t documented, you can’t prove it happened. Inconsistent or incomplete record-keeping undermines your entire vulnerability management program. Without a detailed audit trail, you can’t effectively track your progress, measure your program’s effectiveness over time, or demonstrate compliance to auditors and leadership. Every vulnerability should have a record that documents when it was discovered, how it was prioritized, what remediation steps were taken, and when the fix was validated. This meticulous documentation not only provides a clear history but also generates valuable data you can use to identify bottlenecks and continuously refine your processes for better performance.
My team is small and we’re just getting started. What’s the most important first step? The absolute best place to start is with visibility. Before you can worry about scanning or patching, you need a complete and accurate inventory of every single asset connected to your network. You can’t protect what you don’t know you have. Focus on discovering all your servers, laptops, cloud instances, and devices to get a true picture of your attack surface. This foundational step ensures you aren’t leaving any doors open simply because you didn’t know they were there.
You mentioned not relying only on CVSS scores. So what should I use instead? Think of a CVSS score as just one ingredient in the recipe, not the whole meal. It tells you the technical severity of a flaw but lacks real-world context. To truly prioritize, you need to layer that score with other critical information. Ask yourself: Is this vulnerability being actively exploited by attackers right now? Is it located on a business-critical system, like your customer database? Combining the CVSS score with threat intelligence and business context is how you find the handful of vulnerabilities that pose a genuine danger to your organization.
Isn’t vulnerability management just a fancy term for patch management? That’s a common misconception, but they are quite different. Patching is a crucial part of the process, but it’s just one action you can take. Vulnerability management is the entire strategic cycle that surrounds it. It includes discovering your assets, continuously scanning for weaknesses, prioritizing which ones to fix first based on risk, planning the remediation (which might be a patch or a configuration change), and finally, validating that the fix worked. Patching is a reactive task, while vulnerability management is a proactive strategy.
How can I get other teams, like IT and developers, to care about fixing vulnerabilities? The key is to stop just throwing lists of problems over the wall. Instead, make security a shared goal. Provide these teams with clear, contextualized information that explains why a particular vulnerability is a priority in business terms, not just a high score. Streamline the process for them by integrating with their existing ticketing systems and providing clear remediation guidance. When you make it easier for them to do the right thing and help them see how their work protects the company, they become partners in the process rather than roadblocks.
How often is “continuous scanning” in the real world? Daily? Weekly? “Continuous” doesn’t necessarily mean every second of every day. The goal is to shrink the time between when a vulnerability appears and when you discover it. For your most critical, internet-facing assets, you should aim for a daily scanning schedule. For less critical internal systems, a weekly scan might be perfectly fine. The right frequency depends on the asset’s importance and how quickly your environment changes. The idea is to move away from infrequent snapshots and toward a much more current, real-time view of your security posture.