Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Your security team isn’t just fixing technical flaws; they’re protecting the business from tangible risks. The problem is, a list of thousands of CVEs doesn’t communicate business impact very well. It’s just noise until you can connect a vulnerability to a potential outcome. Threat intelligence provides that crucial link. It helps you answer the question, how does threat intelligence improve vulnerability management? by translating technical data into business context. You can finally see which vulnerabilities threaten your most critical assets and are being actively exploited by threat actors targeting your industry. This allows you to align your remediation efforts with business priorities and communicate risk in a way everyone understands.
Let’s be honest: your vulnerability scanner probably gives you a list of issues so long it feels impossible to tackle. You have thousands of vulnerabilities, limited time, and a team that’s already stretched thin. So, how do you decide what to fix first? This is where threat intelligence comes in. It’s not just another data feed; it’s the context that turns a massive, overwhelming list of vulnerabilities into a focused, actionable plan. Think of it as the difference between knowing a window is unlocked and knowing a burglar is actively checking windows on your street. Both are problems, but one requires your immediate attention.
Threat intelligence provides crucial information about active cyberthreats, attacker techniques, and emerging exploits. When you integrate this intelligence into your vulnerability management program, you stop guessing and start making data-driven decisions. It helps you see which vulnerabilities are just theoretical risks and which ones are being actively used by attackers in the wild. This shift allows your team to focus its energy on patching the flaws that pose a genuine, imminent threat to your organization, making your entire security posture stronger and more efficient through vulnerability and threat prioritization.
Threat intelligence isn’t a one-size-fits-all solution. It comes in a few different flavors, each serving a unique purpose. At a high level, you have strategic intelligence, which gives executives insight into the threat landscape and potential business risks. Then there’s tactical intelligence, which details the tactics, techniques, and procedures (TTPs) attackers use—essentially their playbook. Operational intelligence focuses on specific, ongoing attack campaigns, while technical intelligence provides the granular details like malicious IP addresses and file hashes.
For vulnerability management, the operational and technical types are your bread and butter. This is the information that tells you a specific CVE is being exploited in a new malware campaign or that a certain threat actor is targeting your industry. This is the kind of actionable insight our HiveForce Labs team focuses on, helping you connect the dots between a vulnerability on your network and a real-world threat.
Integrating threat intelligence fundamentally changes your security approach from reactive to proactive. Instead of just reacting to scan results based on generic severity scores, you can anticipate an attacker’s next move. For example, threat intelligence can alert you when a long-forgotten vulnerability suddenly becomes popular again with attackers. This allows you to prioritize patching that old flaw before it becomes a new problem, preventing attackers from taking advantage of a gap you might have otherwise overlooked.
This proactive stance is even more critical when dealing with zero-day vulnerabilities. Before a patch is even released, threat intelligence can provide early indicators of exploitation, giving your team a head start on mitigation. You can implement temporary workarounds, adjust firewall rules, or increase monitoring on potentially affected systems. By leveraging up-to-date threat advisories, you can build a more resilient defense that adapts to the threat landscape as it evolves.
Vulnerability management is a core pillar of any security program. At its heart, it’s the continuous process of identifying, evaluating, treating, and reporting on security vulnerabilities across your systems and software. But as your attack surface expands, the traditional way of doing things starts to show its cracks. Simply running scans and generating reports isn’t enough to keep you safe from determined attackers. Let’s look at why the old-school approach is no longer cutting it.
If you’ve ever felt like you’re drowning in a sea of vulnerability alerts, you’re not alone. Traditional vulnerability management often creates massive, unmanageable lists of potential issues that security teams can’t possibly keep up with. The real challenge isn’t just the volume; it’s the lack of context. You have a list of problems, but you don’t know which ones are truly dangerous. This uncertainty leads to a state of paralysis, where critical fixes get lost in the noise. It’s a frustrating cycle, and it’s why so many cyberattacks succeed by exploiting known, unpatched vulnerabilities. Your team is working hard, but they’re chasing a never-ending list without a clear path to reducing actual risk.
A reactive security posture is a direct result of these traditional challenges. When your vulnerability management and threat intelligence operate in separate silos, your team is forced to play defense without knowing where the attack will come from. You might be patching vulnerabilities with high CVSS scores, but that’s not the whole story. Just scanning for issues or relying on a static risk score isn’t enough. You need to know which vulnerabilities are actually being used by attackers right now. Without this crucial insight, your team might spend weeks fixing a low-risk flaw while a weaponized vulnerability sits unpatched on a critical server, simply because its CVSS score was lower.
The core issue boils down to volume and prioritization. Traditional vulnerability management metrics often focus on things like scan coverage, patch deployment rates, and the time it takes to close a ticket. While these are useful, they don’t measure what matters most: risk reduction. A modern approach focuses on business impact, exploitability, and context-driven prioritization. Instead of asking, “How many vulnerabilities did we patch?” the better question is, “Did we patch the vulnerabilities that attackers are actively exploiting to target our industry?” Shifting your focus to threat and vulnerability prioritization based on real-world threat intelligence is how you move from being busy to being effective.
Threat intelligence does more than just help you sort through a mountain of vulnerabilities—it fundamentally changes how you find them in the first place. By shifting from a simple checklist approach to an intelligence-led one, you can uncover the risks that truly matter to your organization with greater speed and precision. It’s about working smarter, not just harder, to see your attack surface through the eyes of an attacker. This approach moves vulnerability identification from a routine task to a strategic defense mechanism, ensuring your team’s efforts are always focused on the most relevant threats.
Traditional vulnerability scanners are great at telling you what CVEs exist in your environment, but they often lack the context of which ones are being actively exploited in the wild. Integrating real-time threat data makes your scanners smarter. Instead of just matching signatures, they can surface threats based on current exploit data and known attack patterns. This allows your team to spot the early indicators of a zero-day exploit and begin mitigation even before an official patch is available. By focusing on proven risks instead of theoretical ones, you can direct your resources where they’ll have the most impact on your vulnerability and threat prioritization efforts.
Attackers are creatures of habit and opportunity. They often reuse successful tactics or target older, forgotten vulnerabilities that teams have neglected. Threat intelligence acts as an early warning system, helping you identify these renewed exploitation patterns before they become a full-blown incident. When your security tools are informed by up-to-the-minute threat advisories, you can quickly detect emerging campaigns targeting your industry or technology stack. This proactive stance allows you to patch or implement compensating controls, effectively shutting the door on attackers before they can gain a foothold in your network and cause real damage.
A vulnerability is more than just a number on a report; it’s a potential story of a breach waiting to be written. Threat intelligence provides the narrative. It gives you crucial context about the threats facing your organization, answering questions like: Who is exploiting this vulnerability? What techniques are they using? What assets are they targeting? This insight, often curated by research teams like HiveForce Labs, transforms a flat list of findings into a rich, three-dimensional view of your risk landscape. With this added context, you can better understand the potential impact of a vulnerability and build more resilient defenses against specific adversaries.
Knowing you have thousands of vulnerabilities is one thing; knowing which ones to fix before your coffee gets cold is another entirely. This is where threat intelligence changes the game. It shifts your vulnerability management program from a numbers game of patching everything with a high CVSS score to a strategic operation focused on defusing the most immediate threats to your business. By layering real-world data over your scan results, you can finally answer the most important question: “What are attackers likely to target next?”
This transformation is critical because traditional vulnerability management often feels like trying to drink from a firehose. Security teams are inundated with alerts, and without proper context, they’re forced to rely on generic severity scores that don’t account for how threats behave in the real world. A vulnerability might have a high score but be incredibly difficult to exploit, while another with a lower score could be the main ingredient in a new ransomware campaign.
Threat intelligence provides that crucial layer of context. It’s the difference between knowing a door is unlocked and knowing a burglar is actively checking the doors on your street. By integrating data on active exploits, attacker tactics, techniques, and procedures (TTPs), and emerging campaigns, you can see your vulnerabilities through the eyes of an adversary. This allows you to prioritize vulnerabilities not just by their theoretical severity, but by their actual, demonstrated risk to your organization. It’s about working smarter, not just harder, and focusing your finite resources where they will have the greatest impact on your security posture.
The Common Vulnerability Scoring System (CVSS) gives you a standardized severity score, which is a great starting point. But it doesn’t tell the whole story. A vulnerability with a “critical” 9.8 score might be difficult to exploit and largely ignored by threat actors, while a “medium” 6.5 could be part of an active, widespread campaign. Threat intelligence provides the missing context. Instead of just relying on static scores, a threat-informed approach helps you focus your team’s limited time and resources on the flaws that represent a clear and present danger to your organization, not just a theoretical risk.
Are attackers actively using an exploit for a vulnerability found in your environment? That’s the kind of question threat intelligence helps you answer instantly. It provides early warnings about emerging threats, including zero-day exploits, by monitoring chatter on the dark web, tracking malware campaigns, and analyzing attacker tactics. Integrating this data into your vulnerability management process allows you to detect indicators of exploitation and coordinate a response before an official patch might even be available. This transforms your security posture from reactive to proactive, allowing you to address the vulnerabilities that are actively being weaponized by adversaries instead of just chasing down every high-severity alert.
Ultimately, threat intelligence allows you to create a more accurate, evidence-based risk score for each vulnerability. By combining data on exploitability with the business criticality of an asset, you can build a true picture of your exposure. This helps you schedule and prioritize patches more effectively, focusing on the intersection of high business impact and high likelihood of exploitation. Instead of treating all critical vulnerabilities as equally urgent, you can direct your remediation efforts toward the ones that pose an imminent threat. This data-driven approach ensures you’re always working on the right fixes at the right time, significantly reducing your overall risk profile.
Think of Breach and Attack Simulation (BAS) as a sparring partner for your security infrastructure. While vulnerability scans tell you where the theoretical weaknesses are, BAS tools actively try to exploit them, showing you what an attacker could actually do. Instead of just listing open doors, BAS walks through them to see where they lead. This proactive approach moves your vulnerability management program from a passive, list-checking exercise to an active, evidence-based defense strategy.
By simulating real-world attack techniques and tactics, BAS provides a constant feedback loop on how well your security controls perform. It helps answer critical questions like, “Would our EDR solution actually stop that new ransomware strain?” or “Can an attacker move from a compromised web server to our critical data?” Integrating BAS means you’re not just managing a list of vulnerabilities; you’re actively testing your resilience against the threats that matter most. This process gives you concrete data to prioritize fixes, justify security investments, and prove that your defenses are working as intended.
You have firewalls, endpoint protection, and email gateways in place, but how do you know they’re configured correctly and will stand up to a real attack? BAS gives you the answer by running automated, safe attack simulations that mimic the latest adversary behaviors. This process provides practical, continuous insight into the effectiveness of your security controls. It’s one thing to have a tool; it’s another to know it will block a specific command-and-control technique used by a known threat group. By constantly testing your defenses against up-to-date threat intelligence, you can find and fix gaps before an attacker discovers them. This is where adversarial exposure validation becomes a critical part of your strategy.
Vulnerabilities rarely exist in isolation. Attackers often chain together multiple, seemingly low-risk weaknesses to create a path to their objective. BAS is designed to think like an attacker, identifying and testing these potential attack paths across your network. By simulating realistic scenarios, BAS helps you understand your exposure in context. It might show how a vulnerability on a public-facing server, combined with weak internal permissions, could allow an attacker to access sensitive databases. This helps your team see the bigger picture and prioritize the vulnerabilities that serve as critical stepping stones in a potential breach, rather than just focusing on individual CVSS scores.
Your environment is constantly changing—new assets are added, software is updated, and configurations are modified. A security assessment from six months ago is already out of date. BAS platforms address this by providing a way to continuously assess your security posture. These tools can run simulations automatically and regularly, giving you a near real-time view of your defensive readiness. This continuous validation ensures that a misconfiguration or a newly discovered threat doesn’t create a blind spot in your defenses. By proactively detecting risks as they emerge, you can maintain a consistently strong security posture and prevent minor issues from turning into costly incidents.
Making the switch from a reactive to a proactive security posture starts with weaving threat intelligence into your daily operations. It’s not about adding another tool to your stack; it’s about fundamentally changing how you see and act on risk. Instead of just patching what a scanner finds, you’ll be using real-world data to guide your efforts toward the threats that pose a genuine danger to your organization. This approach transforms vulnerability management from a compliance-driven chore into a strategic defense mechanism.
Putting threat intelligence into practice means creating a clear, repeatable process that your team can follow. It involves connecting the right data sources to your existing tools, automating workflows to handle the volume, and fostering collaboration across teams to ensure everyone is working from the same playbook. By focusing on these key areas, you can build a system that not only identifies vulnerabilities but also provides the context needed for effective vulnerability and threat prioritization. The goal is to make your security program more efficient, targeted, and capable of stopping attacks before they happen.
The first practical step is to enrich your vulnerability scanners with high-quality threat intelligence feeds. Your scanners are great at finding potential weaknesses, but on their own, they lack the context to know which ones are being actively exploited in the wild. By integrating threat feeds, you give your tools a direct line to what attackers are doing right now. This allows your scanner to become much smarter, surfacing threats based on real-time exploit data and known attack patterns. As a result, you can spot the early indicators of a zero-day exploit or prioritize a vulnerability that just became a popular target, all while safely deprioritizing theoretical risks that aren’t an immediate concern.
Once your scanners are armed with threat intelligence, the next challenge is managing the data. Manually sifting through thousands of alerts isn’t just inefficient—it’s impossible. This is where automation comes in. You can use AI and machine learning to create workflows that automatically identify, assess, and prioritize vulnerabilities based on the intelligence you’re feeding into the system. For example, you can set up rules that automatically create a high-priority ticket for your IT team whenever a vulnerability is detected on a critical asset and is associated with an active threat campaign. This frees up your security analysts to focus on strategic investigation and response rather than getting bogged down in manual triage.
Threat intelligence is most effective when it’s shared. A critical vulnerability doesn’t just impact the security team; it affects IT, DevOps, and the business as a whole. To get everyone on the same page, you need to develop strategies that promote cross-team collaboration. This often means shifting your metrics away from traditional counts like patch rates and toward KPIs that reflect business impact and exploitability. When you can clearly communicate why a specific vulnerability is a top priority—because it affects a revenue-generating application and is being actively exploited—you create a shared sense of urgency. This context-driven approach ensures that remediation efforts are aligned with business goals and that everyone understands their role in reducing risk.
Integrating a new data source into your security program will inevitably come with a few hurdles. You might face challenges with data overload, tool incompatibility, or simply proving the value of your investment. The key to overcoming these obstacles is to set clear goals and measure your progress. By establishing a core set of KPIs, you can track the maturity of your program and demonstrate its effectiveness over time. For instance, you can monitor improvements in your mean-time-to-remediate (MTTR) for critical threats or track the reduction in successful attacks. These metrics help you identify gaps in controls and fine-tune your processes, ensuring your threat intelligence program delivers real, measurable results.
Integrating threat intelligence into your vulnerability management program feels like a win, but how do you prove it’s actually working? You can’t just rely on a gut feeling. Measuring the impact of your threat intelligence is crucial for demonstrating its value, securing budget, and fine-tuning your strategy over time. By tracking the right key performance indicators (KPIs), you can move from simply collecting data to making data-driven decisions that strengthen your security posture.
The goal is to see clear, quantifiable improvements in how your team identifies, prioritizes, and remediates threats. When you infuse your vulnerability management with real-world threat context, you should see your team become faster, more focused, and more efficient. This isn’t about adding more work; it’s about making the work you’re already doing more effective. A platform that provides a unified view of cyber risks can help you consolidate these metrics, making it easier to monitor progress and spot trends before they become major problems. Let’s look at a few key areas where you can measure the impact.
One of the most direct ways to see the value of threat intelligence is by tracking how quickly your team can fix critical vulnerabilities. When you know which threats are being actively exploited in the wild, you can cut through the noise and direct your resources to the most urgent issues. This is where you’ll want to monitor your Mean Time to Remediate (MTTR).
A falling MTTR for high-risk vulnerabilities is a strong signal that your intelligence is working. You can also measure remediation coverage, which shows the percentage of detected vulnerabilities that your team has successfully patched. By focusing on the threats that matter most, your team can guide remediation efforts more effectively, closing critical security gaps before attackers can exploit them.
Are your security teams still spending most of their time chasing vulnerabilities with high CVSS scores? Threat intelligence helps you move beyond static scores to a more dynamic, risk-based approach. By layering in data on exploitability, threat actor activity, and business impact, you can prioritize the threats that pose a genuine danger to your organization.
The key metric here is a reduction in the number of open, exploitable vulnerabilities on your critical assets. If your threat intelligence is accurate, your team will be focused on the most dangerous threats, not just the ones that look scary on paper. This shift ensures you’re addressing the vulnerabilities most likely to be used in an attack, which is a far more accurate measure of risk reduction than just burning down a list based on severity scores.
Nothing drains a security team’s resources faster than chasing down false positives. Every alert that turns out to be a non-issue is time and energy that could have been spent on real threats. High-quality threat intelligence provides the necessary context to validate findings, helping you distinguish between a theoretical vulnerability and a practical, exploitable threat.
When you integrate threat intelligence, you should see a noticeable drop in the number of alerts your team dismisses as false positives. This is a clear indicator of improved efficiency. Instead of getting bogged down by noise, your team can trust the alerts they receive and focus on meaningful investigation and response. This helps you build a more proactive security posture by focusing on adversarial exposure validation rather than just asset coverage.
Ultimately, better prioritization, faster remediation, and fewer false positives all lead to one thing: a more efficient security program. When your team isn’t wasting cycles on low-risk vulnerabilities or false alarms, they can allocate their time and budget to more strategic initiatives. This is where you can see the true ROI of your threat intelligence investment.
Track metrics like the number of vulnerabilities remediated per analyst or the overall cost per remediation. As your program matures, you should see these costs decrease as efficiency increases. A well-designed dashboard that consolidates all your KPIs in one place helps your team monitor progress and take timely action. This holistic view allows you to see how threat intelligence is not just a security tool but a business enabler that optimizes your most valuable resource: your people.
Putting threat intelligence into practice isn’t just about having access to data; it’s about having the right systems to interpret and act on it. The goal is to create a seamless flow of information from intelligence sources directly into your security workflows. When you choose the right tools, you can automate much of this process, freeing up your team to focus on strategic remediation instead of manual data correlation. The right technology stack ensures that threat intelligence isn’t just another dataset but a core driver of your security operations, from initial scanning to final patching. This integration is what turns a reactive vulnerability management program into a proactive threat exposure management strategy.
Modern vulnerability scanners are much more than simple discovery tools. The best ones come with integrated threat intelligence feeds that add a crucial layer of context to every scan. Instead of just giving you a long list of CVEs, these scanners can highlight which vulnerabilities are being actively exploited in the wild. This allows you to prioritize your response efforts based on real-world risk, not just theoretical severity scores. When your scanner is powered by real-time exploit data, it becomes smarter, helping you surface the most urgent threats while filtering out the noise of low-risk findings. This early intelligence can even help you detect indicators of zero-day exploitation before a patch is even available.
Your Security Information and Event Management (SIEM) system is the central nervous system of your security operations, collecting logs and event data from across your network. By integrating a threat intelligence platform (TIP), you enrich that data with external context about current threats, malicious actors, and indicators of compromise. This combination gives your security team a much clearer picture of what’s happening. An alert that might seem minor on its own can become a high-priority incident when correlated with intelligence about an active attack campaign. This integration helps you connect the dots between internal events and external threats, making your threat exposure management platform the single source of truth for your security posture.
Finding and prioritizing vulnerabilities is only half the battle; you still have to fix them. Automated patch management solutions are essential for closing the loop quickly and efficiently. When guided by threat intelligence, these tools can automatically deploy patches for the most critical vulnerabilities first, drastically reducing your window of exposure. This approach ensures your patching activities are directly aligned with your vulnerability management goals. Instead of tackling patches in a disorganized way, you can create automated workflows that address the most imminent threats first. This not only improves your security posture but also demonstrates a measurable return on your threat intelligence investment.
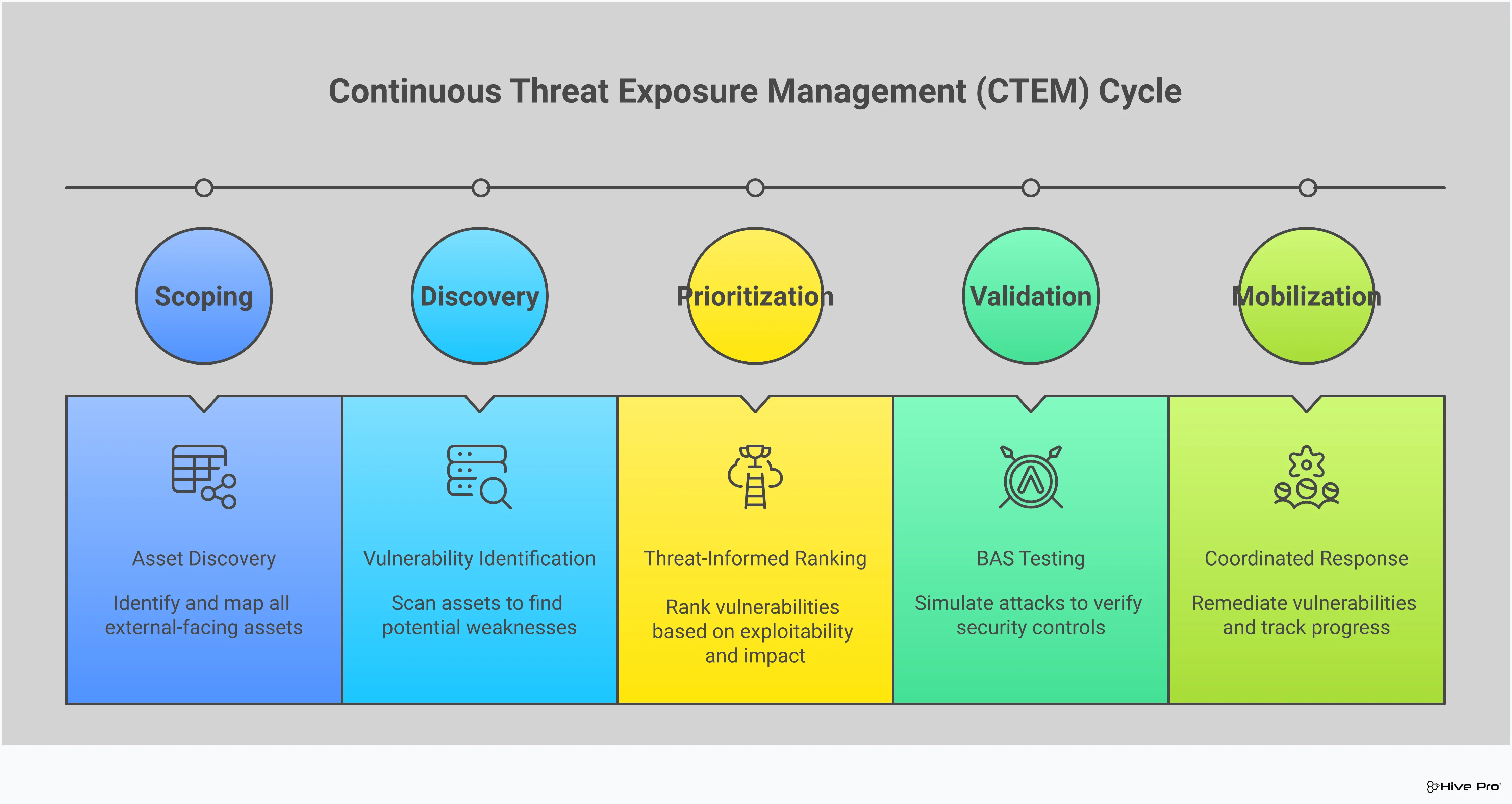
Shifting from traditional vulnerability management to a proactive Continuous Threat Exposure Management (CTEM) program isn’t just about adopting new tools; it’s about embracing a new mindset. It means moving away from a cycle of scanning and patching in a vacuum and toward a continuous loop of discovery, prioritization, validation, and mobilization. This approach helps you see your organization through an attacker’s eyes, focusing your efforts on the exposures that pose a genuine threat.
Building a CTEM program involves creating a sustainable framework that aligns your security efforts with real-world threat intelligence. It’s about understanding your entire attack surface, prioritizing vulnerabilities based on active exploitation, and validating that your security controls are actually working. This process transforms your security posture from reactive to resilient, allowing you to confidently answer the question, “Are we secure?” instead of just, “Are we patched?” By following a structured approach, you can create a program that not only identifies weaknesses but also helps you fix the ones that matter most before they can be exploited.
You can’t protect what you can’t see. The first step in any effective CTEM program is to gain a complete and continuous view of your entire digital footprint. This goes beyond traditional network scans to include cloud assets, web applications, mobile devices, and IoT. A comprehensive Total Attack Surface Management strategy gives you a unified inventory of all your assets and their associated vulnerabilities. By integrating threat intelligence into this discovery process, you gain early awareness of emerging threats that could impact your specific environment. A well-designed dashboard that consolidates key metrics is essential for monitoring your progress, spotting trends, and taking action quickly.
An adaptive security posture means your defenses can evolve in response to the changing threat landscape. Instead of relying on static rules and annual penetration tests, you continuously validate your security controls against the latest attack techniques. Threat intelligence is the fuel for this engine. It provides the evidence-based risk data needed to schedule and prioritize patches effectively, focusing on vulnerabilities with high exploitability and real business impact. When threat actors revisit old vulnerabilities, your intelligence-driven approach allows you to spot these patterns early and reinforce your defenses. This is the core of proactive vulnerability and threat prioritization—fixing what attackers are actively targeting right now.
Not all threat intelligence is created equal. A successful CTEM program relies on high-fidelity, relevant, and timely data from multiple sources. This can include open-source intelligence (OSINT), commercial threat feeds, and information from industry-sharing groups (ISACs). The real power comes from specialized research teams, like HiveForce Labs, that provide curated intelligence with deep context. Modern platforms also use AI to automate the identification and assessment of vulnerabilities based on this real-time data. By combining quality intelligence sources with smart technology, you can cut through the noise and focus your team’s valuable time on mitigating the most critical exposures.
My team is already overwhelmed with alerts. Won’t adding threat intelligence just create more noise? That’s a fair question, but it’s actually the opposite. Threat intelligence is designed to cut through the noise, not add to it. Instead of giving you more alerts, it gives your existing alerts context. It helps you instantly see which of the thousands of vulnerabilities on your list are just theoretical problems and which ones are being actively used by attackers right now. This allows your team to ignore the low-risk distractions and focus their limited time and energy on the issues that pose a genuine, immediate threat.
So, should I just ignore CVSS scores now? Not at all. Think of the CVSS score as a starting point—it tells you the potential severity of a vulnerability in a perfect vacuum. Threat intelligence adds the real-world context. A vulnerability might have a critical CVSS score, but if it’s incredibly difficult to exploit and no one is actually using it, it’s less of a priority. On the other hand, a flaw with a medium score that’s being used in a widespread ransomware campaign needs your immediate attention. You use both together to get a true picture of your risk.
How is Breach and Attack Simulation (BAS) different from a penetration test? While both test your defenses, they serve different purposes. A penetration test is typically a manual, point-in-time engagement that happens periodically, like once or twice a year. It gives you a deep snapshot of your security at that moment. Breach and Attack Simulation, however, is an automated and continuous process. It constantly runs safe, simulated attacks against your security controls to validate that they are working as expected against the latest threats, giving you a real-time view of your defensive readiness.
What’s the most important first step to integrate threat intelligence into our current process? The most practical place to start is by connecting a high-quality threat intelligence feed directly to your existing vulnerability scanner. This is often a simple integration that provides an immediate return. Your scan results will instantly become more meaningful because they’ll be enriched with data on which vulnerabilities are actively being exploited. This allows you to begin prioritizing more effectively right away, without having to overhaul your entire workflow from day one.
What does success look like? How do I know this approach is actually working? Success is measured by a clear reduction in your organization’s risk. You’ll know it’s working when you see your team spending less time debating what to fix and more time fixing what matters. Key indicators include a significant drop in the time it takes to remediate critical, exploitable vulnerabilities (your Mean Time to Remediate). Ultimately, the goal is to see a decrease in security incidents caused by known, unpatched flaws, proving you’re effectively staying ahead of attackers.