Comprehensive Threat Exposure Management Platform
Trying to secure your organization without understanding an attacker’s perspective is like trying to defend a castle without knowing where the enemy will strike. You can patch walls all day, but you might miss the one weak spot they’re planning to exploit. Threat exposure management gives you that attacker’s-eye view. It’s a continuous process of identifying the paths an adversary could take to compromise your systems and closing those gaps before they can be used against you. By focusing on actively exploited vulnerabilities and validating your defenses, you can move beyond theoretical risk. This guide will explain the core components of a successful TEM program, from asset discovery to remediation.
If your security team feels like they’re constantly playing catch-up, you’re not alone. The traditional approach of chasing down every single vulnerability is a losing battle. Your attack surface is growing by the day, and attackers are getting faster and more sophisticated. This is where Threat Exposure Management (TEM) comes in. It’s a strategic shift that moves you from a reactive, patch-everything mindset to a proactive, risk-based one. Instead of asking, “How many vulnerabilities do we have?” you start asking, “Which exposures are most likely to be exploited and cause real damage to our business?”
TEM is a continuous cycle that helps you see your organization through an attacker’s eyes. It’s about understanding your entire digital footprint, identifying the paths an adversary could take, and closing those gaps before they can be used against you. By focusing on the threats that pose a genuine, measurable risk, you can direct your team’s limited time and resources to where they’ll have the greatest impact. This approach helps you make smarter, more confident security decisions and transforms your security program from a cost center into a strategic business enabler. A solid Threat Exposure Management platform provides a unified view of these risks, helping you focus on what matters most.
At its core, Threat Exposure Management is the practice of continuously identifying, prioritizing, and managing potential threats across your company’s entire digital attack surface. Think of it as a system for cutting through the noise of thousands of alerts to find the handful of issues that truly demand your immediate attention. The primary goal isn’t to achieve a perfect score on a vulnerability scan; it’s to stay ahead of cybercriminals by understanding which weaknesses they are most likely to target. This allows you to spend your security budget and your team’s effort wisely, focusing on fixes that directly reduce business risk and strengthen your overall security posture.
So, how does TEM work in practice? It’s built on a few foundational principles that create a continuous, proactive security loop. First is the constant discovery and monitoring of your total attack surface. You can’t protect assets you don’t know exist, so maintaining a complete inventory of all your internet-facing hardware, software, and cloud services is step one. Next comes intelligent vulnerability and threat prioritization. Instead of relying solely on generic severity scores, TEM uses real-world threat intelligence to pinpoint which vulnerabilities are actively being exploited in the wild. Finally, the process drives mobilization and remediation, creating clear plans to fix the most critical risks first and validate that the fixes are working as intended.
Let’s be honest: the old ways of managing vulnerabilities aren’t cutting it anymore. The sheer volume of alerts, the expanding digital footprint, and the speed of modern threats mean that a reactive, checklist-based approach leaves you constantly playing catch-up. It’s a cycle of scanning, patching, and hoping you got the right things, all while the backlog of vulnerabilities grows. This isn’t just inefficient; it’s a significant business risk.
Shifting to a threat exposure management (TEM) model is the way out of this reactive loop. It isn’t just about adopting new tools; it’s about fundamentally changing how you view and manage risk across your entire organization. Instead of chasing an endless list of CVEs, TEM helps you see your organization through an attacker’s eyes. It’s about getting ahead of threats by understanding where you’re truly exposed, which assets are most critical, and which vulnerabilities are actively being exploited in the wild. This intelligence-led approach allows you to focus your team’s valuable time on the fixes that will actually make a difference to your security posture and protect the business.
Your organization’s attack surface is bigger than ever. Every new cloud server, IoT device, and remote employee connection adds another potential entry point for attackers. Trying to manually track all these assets is an impossible task, and you can’t protect what you don’t know you have. Threat exposure management gives you a continuous, comprehensive view of your entire environment. This isn’t just about scanning for known vulnerabilities; it’s about discovering and mapping every single asset. With a complete picture of your total attack surface, you can finally move from guessing where your risks are to knowing exactly where to focus your defenses.
Waiting for an attack to happen before you act is a recipe for disaster. A reactive security stance means your team is always in firefighting mode, dealing with the consequences of a breach rather than preventing it. This approach is not only stressful but also incredibly expensive, factoring in downtime, data loss, regulatory fines, and reputational damage. A proactive strategy, on the other hand, is designed to continuously identify and mitigate risks before they can be exploited. By focusing on vulnerability and threat prioritization, you can address the most critical exposures first, systematically reducing your risk and building a more resilient organization.
For years, security teams have struggled to explain cyber risk in a way that resonates with the C-suite. Talking about CVE scores and patch levels often doesn’t translate into business terms. Threat exposure management changes that conversation by linking security gaps directly to potential business impact. Instead of just saying “we have 50 critical vulnerabilities,” you can say “this vulnerability in our payment processing system could lead to a significant financial loss and damage customer trust.” This context-driven approach helps executives understand the real-world consequences of cyber threats, making it easier to justify security investments and align your program with overarching business goals.
A solid Threat Exposure Management (TEM) program isn’t built overnight. It’s a strategic cycle with four key phases that work together to turn security data into decisive action. Think of these as the essential pillars that support your entire security posture. Each step builds on the last, creating a continuous loop of discovery, analysis, prioritization, and action that helps you stay ahead of threats. By breaking the process down into these manageable blocks, you can build a program that effectively reduces your organization’s real-world risk.
You can’t protect what you don’t know you have. The first step is to get a complete and continuously updated inventory of every asset across your organization. This means mapping out your entire attack surface—from on-premise servers and employee laptops to cloud instances and IoT devices. This isn’t a one-and-done task; it requires continuous monitoring to find new weak spots as your digital footprint inevitably grows. A comprehensive Total Attack Surface Management approach is foundational because it gives you the visibility needed to understand where you might be exposed.
Once you have a clear picture of your assets, the next step is to identify the vulnerabilities associated with them. But simply running a scan and getting a list of CVEs isn’t enough. True assessment involves analyzing these weaknesses in the context of your business. A critical vulnerability on a public-facing server that holds customer data is a much bigger problem than the same vulnerability on an isolated development machine. This is where TEM starts to change the way executives perceive cyber risk by connecting technical flaws to potential business impact.
With thousands of potential vulnerabilities, trying to fix everything at once is a recipe for burnout and inefficiency. Prioritization is where you separate the signal from the noise. A modern TEM program moves beyond basic CVSS scores and incorporates threat intelligence to focus on what attackers are actively exploiting in the wild. By ranking threats based on their likelihood of exploitation and the potential damage they could cause, you can create a focused, manageable list of the risks that truly matter. This risk-based approach to vulnerability and threat prioritization ensures your team’s valuable time and resources are spent on fixing the problems that pose the greatest threat to your organization.
Discovery and prioritization are meaningless without action. The final step is to create and execute a clear remediation plan. This involves more than just deploying patches. It means coordinating with IT and DevOps teams, communicating timelines, and validating that the fixes have been successfully applied. Sometimes, remediation might involve configuration changes, applying compensating controls, or even running simulated attacks to test your defenses. The goal is to put your plan into action efficiently, ensuring that key stakeholders know their roles and that your security posture is measurably improved.
Vulnerability scanners can give you a massive list of potential weaknesses, but they can’t tell you which ones attackers are actually using. This is where threat intelligence comes in. It’s the crucial layer of context that turns a noisy, overwhelming list of vulnerabilities into a clear, prioritized action plan. By integrating real-world data on active threats, you can see your organization through an attacker’s eyes and understand which of your exposures are most likely to be targeted.
This intelligence-led approach is the heart of modern exposure management. Instead of trying to fix everything at once, you can focus your team’s time and resources on the threats that pose a genuine, immediate risk to your business. It’s about working smarter, not just harder. With a constant stream of information on attacker tactics, techniques, and procedures (TTPs), you can move from a reactive posture to a proactive one, anticipating and neutralizing threats before they can cause damage. This is how you transform your security program from a cost center into a strategic business enabler.
Without context, a vulnerability is just a number. Threat intelligence changes that by connecting a specific CVE to what’s happening in the wild. It tells you if a vulnerability has a publicly available exploit, if it’s being used by a known ransomware group, or if it’s part of a widespread campaign targeting your industry. This information transforms raw vulnerability data into business-focused insights. Instead of reporting thousands of open vulnerabilities, you can pinpoint the handful that are actively being exploited and directly threaten your critical assets. This allows you to have more meaningful conversations with leadership, framing security risks in terms of potential business impact rather than just technical details. This is the core of effective vulnerability and threat prioritization.
Knowing what attackers are doing right now is a massive advantage. Threat intelligence provides that real-time visibility. It helps you spot the early warning signs of an attack by flagging vulnerabilities that are currently being exploited in the wild. For example, if a new exploit for a common software is released, threat intelligence feeds will pick it up immediately, allowing you to act before it becomes a problem for your organization. This proactive stance is critical for preventing attacks. By monitoring the threat landscape, you can quickly identify potential threats and get ahead of them. You can find this kind of actionable information in detailed threat advisories that break down emerging threats and how to defend against them.
Your team has limited time and resources, so every action needs to count. Threat intelligence helps you zero in on the vulnerabilities that matter most. By understanding which weaknesses are being actively targeted by threat actors, you can focus your remediation efforts where they will have the greatest impact. This intelligence-driven approach, powered by research teams like HiveForce Labs, allows you to cut through the noise of low-risk vulnerabilities and concentrate on the critical few that pose a clear and present danger. It fundamentally changes how you manage risk, making business impact the central criterion for prioritization and ensuring your security team is always working on the most important tasks first.
Think of vulnerability management as finding all the unlocked doors and windows in your house. That’s a critical first step, but it doesn’t tell you if an intruder can actually get past your security system or how much damage they could do once inside. That’s where Breach and Attack Simulation (BAS) comes in. It’s the security equivalent of running a fire drill—you get to see how your defenses perform under pressure without the danger of a real fire.
BAS platforms automate the process of simulating real-world cyberattacks against your systems. Instead of just guessing how an attacker might exploit a weakness, you can safely test those attack paths. This proactive approach gives you a clear, evidence-based picture of your security posture. It moves you from a theoretical understanding of your risks to a practical one, showing you exactly where your defenses are strong and where they need reinforcement. This continuous testing is a core part of adversarial exposure validation and a game-changer for any security program.
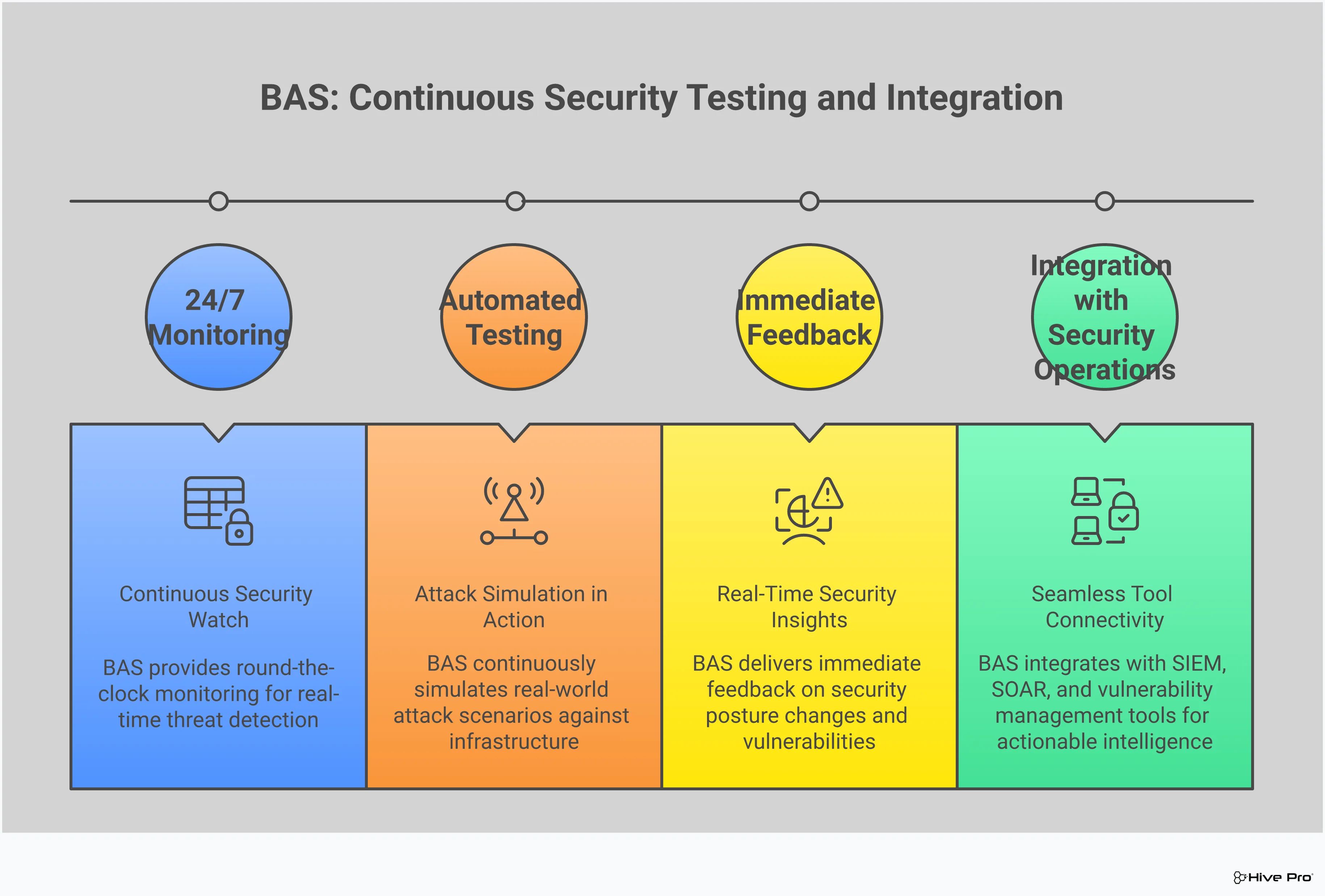
Your security stack is made up of layers of controls—firewalls, endpoint detection, email gateways, and more. But are they all configured correctly and working together? BAS allows you to continuously test your security controls against the latest attack scenarios. By simulating different attack vectors, from phishing attempts to malware execution, you can see if your tools actually detect and block threats as intended. This helps you assess the real-world effectiveness of your security measures, find misconfigurations, and identify gaps before an attacker does. It’s about making sure the investments you’ve made in security technology are actually paying off.
Patching vulnerabilities is a huge part of any security team’s workload. But after all that effort, how do you know the fix was effective? Simply re-scanning for the vulnerability isn’t always enough. BAS provides a concrete way to validate your remediation efforts. After your team applies a patch or changes a configuration, you can run the same attack simulation that previously succeeded. If the attack is now blocked, you have definitive proof that the vulnerability is closed and the risk has been reduced. This creates a feedback loop that confirms your security measures are working, helping you demonstrate progress and ensure that your team’s hard work is truly making the organization safer.
Not all vulnerabilities carry the same level of risk. A long list of CVEs can be overwhelming, making it hard to know where to start. BAS helps you cut through the noise by showing you which vulnerabilities are not just present, but actively exploitable in your environment. By simulating the potential impact of an attack, you can prioritize your vulnerabilities based on real-world risk. This helps you identify the most critical gaps in your security posture, allowing your team to focus its time and resources on the issues that pose the greatest threat to your business. It shifts the focus from patching everything to strategically fixing what matters most.
Putting a Threat Exposure Management (TEM) program into practice isn’t about flipping a switch; it’s a methodical process of gaining visibility, focusing your efforts, and taking decisive action. Think of it as building a strong foundation for a more proactive security posture. By breaking it down into clear, manageable steps, you can move from a reactive state of constant firefighting to a more strategic approach that aligns security with business goals. This process ensures you’re not just finding vulnerabilities but are actively reducing your organization’s real-world exposure to threats.
You can’t protect what you don’t know you have. The first step is to define the boundaries of your program. What parts of the business are you responsible for securing? This includes everything from on-premise servers and employee laptops to cloud instances and IoT devices. Once you’ve set your scope, the real work of discovery begins. You need a complete and continuously updated inventory of every asset within that scope. This process of total attack surface management is foundational. It’s about creating a single source of truth for all your digital and physical assets, ensuring no potential entry point for an attacker is left in the shadows.
Once you have a full asset inventory, you’ll likely uncover a mountain of vulnerabilities. Trying to fix everything at once is a recipe for burnout and inefficiency. The key is smart prioritization. Instead of just relying on CVSS scores, you need to rank vulnerabilities based on factors that matter to your business. Which assets are most critical? Which vulnerabilities are actively being exploited in the wild? Answering these questions requires a vulnerability and threat prioritization strategy that combines asset context with real-time threat intelligence. This helps you cut through the noise and focus your team’s limited resources on the handful of issues that pose a genuine, immediate threat.
Finding a critical vulnerability is one thing; confirming it’s exploitable in your specific environment is another. Validation is the reality check for your security program. This step involves safely simulating attacks to see if your existing security controls—like firewalls, EDR, and web application firewalls—would actually stop an attacker. Tools for adversarial exposure validation, such as Breach and Attack Simulation (BAS), are perfect for this. They let you test your defenses against the latest attack techniques without putting your live systems at risk. This gives you concrete proof of where your gaps are and helps you verify that your remediation efforts are truly effective.
With a prioritized and validated list of exposures, it’s time to act. Mobilization is about getting the right information to the right people to get threats fixed. This isn’t just a job for the security team. Effective remediation requires clear communication and collaboration with IT operations, DevOps, and other stakeholders. Your TEM program should produce clear, actionable guidance that tells teams exactly what needs to be fixed and why it’s a priority. Establishing a streamlined remediation workflow ensures that everyone knows their role and that high-priority risks are addressed quickly, closing the loop from discovery to resolution.
Building a successful threat exposure management program isn’t about finding one silver-bullet tool. It’s about creating a cohesive tech stack where different solutions work together to give you a single, clear picture of your risk. A strong TEM program integrates tools for threat intelligence, attack surface management, and vulnerability assessment. When these systems share data, you can move from simply managing vulnerabilities to proactively reducing your organization’s overall exposure.
Think of threat intelligence as your security team’s early warning system. Up-to-date threat intelligence is essential for TEM because it provides the real-world context you need to understand your risks. These platforms gather data from countless sources—like industry reports, government advisories, and the dark web—to identify emerging attack tactics and pinpoint which vulnerabilities are actively being exploited. This insight helps you understand the “who, what, and why” behind potential attacks, allowing you to focus your defensive efforts on the threats most likely to target your organization.
You can’t protect what you don’t know you have. External Attack Surface Management (EASM) tools help you see your organization from an attacker’s point of view. They continuously scan the internet to discover all of your exposed assets, including forgotten servers, shadow IT, and third-party services connected to your network. EASM is a critical piece of the TEM puzzle, but it doesn’t work in a vacuum. A modern TEM program integrates tools like EASM and CTI to build a more robust and proactive security strategy, ensuring you have a complete map of your potential entry points.
Vulnerability management has long been a cornerstone of security, but its role within TEM is more strategic. Instead of just scanning for flaws and relying on CVSS scores, modern vulnerability management focuses on prioritizing vulnerabilities based on their actual risk to your business. By combining vulnerability data with threat intelligence and asset context, you can identify which flaws pose a genuine threat. This risk-based approach allows your team to stop chasing every single vulnerability and instead concentrate on fixing the ones that matter most.
Your organization’s exposure extends far beyond your network perimeter. Digital Risk Protection (DRP) technologies are designed to monitor your external digital footprint for threats that could harm your brand or expose sensitive data. This includes spotting things like leaked credentials on the dark web, fraudulent social media accounts impersonating your brand, or phishing sites targeting your customers. By safeguarding your online assets, DRP helps you manage your exposure across the open, deep, and dark web, adding another essential layer of defense to your overall security posture.
Adopting a threat exposure management program is a game-changer, but let’s be honest—it’s not always a simple plug-and-play process. Like any significant strategic shift, it comes with its own set of hurdles. Most organizations run into similar challenges when they start moving from a reactive to a proactive security model. The good news is that these obstacles are well-understood, and with the right approach, you can clear them effectively. By anticipating these common issues, you can build a strategy that addresses them from the start, ensuring your TEM program delivers on its promise to reduce risk across your organization.
One of the first roadblocks many teams hit is the sheer investment required. A successful TEM program needs dedicated time, budget, and, most importantly, skilled people. The reality is that there’s a significant cybersecurity talent gap, and finding professionals with the specific expertise needed for continuous exposure management can be tough. You can’t just buy a tool and expect it to run itself; you need analysts who can interpret the data, prioritize threats, and coordinate remediation. This resource strain can stall a program before it even gets off the ground, leaving your organization stuck in a reactive cycle.
The solution isn’t always about hiring a whole new team. Instead, focus on making your current team more efficient. A unified platform that automates asset discovery, vulnerability scanning, and prioritization can drastically reduce the manual workload. By leveraging a solution with built-in threat intelligence from a dedicated research team like HiveForce Labs, you can empower your existing staff to focus on what matters most: fixing the most critical exposures.
It’s a common story: your security stack is a patchwork of new and old technologies that don’t always play well together. Many organizations find it challenging to fit modern TEM tools into their existing infrastructure, especially when legacy systems weren’t built for the kind of constant monitoring a TEM program requires. If your new platform can’t communicate with your existing ticketing systems, asset inventories, or security information and event management (SIEM) tools, you end up creating more data silos and manual work for your team, defeating the purpose of a streamlined process.
To solve this, prioritize tools built with integration in mind. Look for a TEM platform with a robust API and a wide range of pre-built connectors for the tools you already use. This creates a central hub where data from across your security ecosystem can be aggregated and analyzed. An integrated platform not only simplifies your tech stack but also ensures that threat exposure data is seamlessly shared, enabling faster, more effective remediation workflows without the headache of custom development.
Threat exposure management isn’t just a job for the security team; it requires a coordinated effort across security, IT, and DevOps. Unfortunately, these teams often operate in silos with different priorities and communication styles. Security might identify a critical vulnerability, but if they can’t effectively communicate its business impact to the IT team responsible for patching, remediation can be delayed for weeks or even months. This communication gap is one of the biggest barriers to reducing your organization’s overall risk.
The key is to create a shared understanding of risk. A TEM platform can bridge this gap by translating technical vulnerability data into a business-relevant context that everyone can understand. Instead of just presenting a list of CVEs, you can show which business-critical applications are at risk. This helps align different teams around a common goal. By establishing clear, automated workflows for remediation and tracking progress in a centralized dashboard, you can break down silos and foster the collaboration needed to fix exposures quickly.
You might see the terms Threat Exposure Management (TEM) and Continuous Threat Exposure Management (CTEM) used together, but they aren’t interchangeable. That one little word—continuous—makes all the difference. Think of TEM as the essential framework, the blueprint for identifying, prioritizing, and dealing with threats. It’s the strategic plan. CTEM takes that blueprint and turns it into a living, breathing part of your daily security operations. It’s the operational practice that never sleeps.
The core difference is the cadence. A TEM program might operate on a schedule—say, with quarterly vulnerability assessments or annual reviews. It’s structured and valuable, but it can leave gaps between check-ins. CTEM closes those gaps by making exposure management an always-on activity. It integrates the process directly into your workflows, creating a constant feedback loop that helps you adapt to threats as they emerge, not just after the fact. This shift from a periodic to a perpetual model is what helps you stay ahead of attackers.
While a traditional TEM program might involve point-in-time activities, CTEM operates around the clock. This doesn’t mean your team has to pull all-nighters. Instead, it relies on automation to constantly scan your digital footprint for new weaknesses and emerging threats. This gives you a real-time view of your most significant exposures, allowing you to address problems much more quickly. It’s the difference between checking the weather forecast once in the morning and having a live radar map that shows you exactly when and where the storm will hit, giving you time to prepare.
A major advantage of CTEM is its ability to unify your security stack. Instead of having separate tools for threat intelligence, attack surface management, and risk protection that don’t communicate, CTEM brings them all together. This creates a single, cohesive view of your security posture. By breaking down the silos between different security functions, you can translate technical findings into a clear, business-relevant context. This integrated approach ensures that everyone, from your security analysts to your executive team, is working with the same complete picture of your organization’s attack surface.
Adopting a CTEM model is a clear indicator of a mature security program. It signifies a move away from reactive, checklist-based security toward a proactive and dynamic defense strategy. A mature program doesn’t just identify vulnerabilities; it continuously validates controls, tests defenses, and refines its approach based on real-world threat intelligence. The goal is to embed threat exposure management into the fabric of your daily operations. This continuous cycle of discovery, prioritization, and remediation is what truly reduces risk and builds a resilient security posture over time.
You can’t improve what you don’t measure. A successful Threat Exposure Management (TEM) program does more than just reduce your vulnerability count; it demonstrates a clear, quantifiable reduction in business risk. Tracking the right metrics proves the value of your security efforts to leadership and helps you fine-tune your strategy over time. It shifts the conversation from a purely technical one about patching to a business-focused discussion about protecting critical assets and preventing costly incidents.
The goal is to move beyond simple volume metrics. Instead of just reporting how many vulnerabilities you’ve patched, you should focus on how your program is making the organization safer and your team more effective. This means tracking a mix of performance indicators, risk reduction metrics, and efficiency gains. When you can show a downward trend in critical exposures and an upward trend in your team’s capacity, you’re building a powerful case for your TEM program’s impact and justifying continued investment in the people and tools that make it work.
To get a clear picture of your program’s health, you need to track a few core KPIs. These metrics give you a high-level view of your team’s responsiveness and the overall state of your security posture. Start with Mean Time to Remediate (MTTR), which measures how long it takes your team to fix a vulnerability after it’s been identified. A consistently decreasing MTTR shows your processes are getting more efficient. Also, keep an eye on your overall attack surface size. While it may fluctuate, a successful program will prevent uncontrolled growth. A unified platform can help you monitor these KPIs in a single dashboard, making it easier to spot trends and report on progress.
True success in TEM isn’t just about speed; it’s about impact. You need metrics that show you’re reducing actual, tangible risk. Instead of tracking the total number of closed vulnerabilities, focus on the percentage reduction of critical and exploitable exposures—the ones attackers are actively using. You can also measure how effectively your security controls are performing by running simulations. This process of adversarial exposure validation gives you a pass/fail grade on your defenses against specific threats. By focusing on these metrics, you can clearly demonstrate to stakeholders that you are neutralizing the most significant threats to the business, not just chasing down every minor flaw.
A strong TEM program should make your security team more effective, not just busier. To measure this, look at operational efficiency. How much time is your team saving through automated discovery and prioritization? Track the number of high-priority vulnerabilities remediated per week or month to gauge your team’s throughput. Another key metric is the reduction in manual effort for tasks like reporting and ticket creation. When your team spends less time on administrative work, they have more time to focus on complex threats. This is where vulnerability and threat prioritization tools become invaluable, ensuring your analysts’ expertise is applied where it matters most.
How is Threat Exposure Management different from the vulnerability management we’re already doing? Think of it as a shift in focus from quantity to quality. Traditional vulnerability management often becomes a numbers game, where the goal is to patch as many CVEs as possible based on a generic severity score. Threat Exposure Management changes the question from “How many vulnerabilities do we have?” to “Which of our exposures are attackers most likely to use against us?” It adds business context and real-world threat intelligence to the equation, so you can prioritize the handful of weaknesses that pose a genuine risk to your organization.
My team is already swamped with alerts. Won’t this just add more to our plate? Actually, the goal is the exact opposite. A solid Threat Exposure Management program is designed to reduce alert fatigue, not add to it. By using threat intelligence to see which vulnerabilities are actively being exploited in the wild, you can filter out the thousands of low-risk issues that scanners flag. This allows your team to stop chasing every minor flaw and concentrate their limited time and energy on fixing the critical exposures that could lead to a real breach. It’s about working smarter, not just harder.
What’s the most important first step to get a TEM program off the ground? Before you can prioritize or remediate anything, you need visibility. The most critical first step is to get a complete and continuous inventory of your entire attack surface. You simply can’t protect assets you don’t know exist. This means discovering everything from your servers and cloud instances to employee devices and shadow IT. This foundational map of your digital footprint is what all other TEM activities are built upon.
Why is Breach and Attack Simulation (BAS) so important for vulnerability management? Finding a vulnerability is like discovering an unlocked door in your building. Breach and Attack Simulation is like safely testing if an intruder could actually walk through that door, bypass your security cameras, and access a sensitive area. BAS validates whether a vulnerability is truly exploitable in your specific environment and if your existing security controls would stop an attack. It provides concrete proof of where your real gaps are, turning theoretical risks into actionable security insights.
Is there a real difference between TEM and CTEM, or is “continuous” just marketing speak? The difference is very real and it’s all about cadence. Think of TEM as the strategic framework or the blueprint. CTEM, or Continuous Threat Exposure Management, is the operational practice of making that blueprint a living, always-on part of your security program. Instead of doing periodic assessments, CTEM uses automation to constantly monitor your attack surface, analyze new threats, and validate your defenses. It’s the shift from a scheduled check-up to a 24/7 feedback loop that helps you keep pace with attackers.