Comprehensive Threat Exposure Management Platform
When a threat actor disables your security software and starts deleting your backups, you’re already in the middle of a crisis. The operators behind SafePay ransomware are known for these exact tactics, deliberately sabotaging your ability to respond and recover. Catching an attack like this early requires knowing the specific warning signs, from unusual account activity to suspicious lateral movement across your network. This article provides a clear, actionable breakdown of the indicators of compromise associated with a SafePay attack. We’ll cover the essential steps for spotting an intrusion and show you how to build a comprehensive defense to stop them in their tracks.
SafePay ransomware quickly made a name for itself after appearing on the scene, establishing itself as a significant threat to organizations worldwide. This group operates by encrypting files, stealing sensitive data, and demanding a hefty ransom payment to restore access and prevent a public data leak. What makes SafePay particularly dangerous is its speed and efficiency, often moving from initial breach to full-scale encryption in a remarkably short time frame. For security teams, understanding how this group functions is the first step toward building a solid defense. It’s not just about blocking malware; it’s about recognizing the entire attack chain, from the initial entry point to the final ransom note.
At its core, SafePay is designed to render your data completely inaccessible. Once it infiltrates a network, the ransomware uses sophisticated encryption techniques to lock down files, appending a “.safepay” extension to each one. To make recovery even more challenging, it actively seeks out and deletes backup copies it finds on the network. While the encryption tool appears to be custom-built, security researchers have noted similarities to other well-known ransomware families like LockBit Black and Hive. This combination of custom tooling and proven tactics makes it a formidable threat for any organization.
The typical attack lifecycle for a SafePay incident is alarmingly fast. Attackers often gain their initial foothold by exploiting common vulnerabilities in internet-facing devices, such as VPNs, firewalls, and poorly secured Remote Desktop Protocol (RDP) servers. Once inside, they don’t waste any time. They immediately begin scanning the network for shared folders, critical servers, and other high-value targets. In many documented cases, the entire process—from initial breach to widespread data encryption—is completed in less than 24 hours, leaving security teams with very little time to react.
SafePay doesn’t just lock up your files; it also steals them. The group employs a double-extortion strategy that dramatically increases the pressure on its victims. Before encrypting the data, attackers exfiltrate large volumes of sensitive information. This means that even if you have backups and can restore your systems, the threat isn’t over. The attackers will threaten to release your confidential data—customer information, financial records, intellectual property—on the dark web if the ransom isn’t paid. This tactic turns a business disruption into a potential data breach, complicating the incident response process and raising the stakes considerably.
SafePay operators are methodical, typically relying on a few proven entry points to get their foot in the door. They don’t reinvent the wheel; instead, they exploit common security gaps that many organizations struggle to close. Their approach combines technical exploits with social engineering, making it a multi-faceted threat. Understanding their initial access and lateral movement techniques is the first step to building a solid defense. By breaking down their attack chain, you can see where your own security controls might be tested and identify opportunities to stop them before they gain a significant foothold in your environment.
One of the most common ways SafePay gets in is by targeting your network’s perimeter. Attackers are constantly scanning for unpatched vulnerabilities in internet-facing devices like VPNs, firewalls, and Remote Desktop Protocol (RDP) servers. These systems are prime targets because they are designed to allow external access. If not properly configured and updated, they become open doors. This is why continuously understanding your full attack surface is so critical. A single overlooked vulnerability in a VPN appliance can be all an attacker needs to bypass your primary defenses and establish an initial presence on your network.
SafePay doesn’t just rely on technical exploits; they also target your people. The group is known to use phishing emails to trick employees into giving up their login information. Alternatively, they simply purchase stolen credentials from dark web marketplaces, which often come from previous, unrelated data breaches. This tactic bypasses many technical controls entirely, as the attacker logs in with what appears to be legitimate access. Keeping your team informed and staying current on threat advisories can help them spot sophisticated phishing attempts and understand the risks associated with credential reuse.
Once inside, SafePay operators work quickly to expand their access. After gaining an initial foothold, they often use scripts like ShareFinder.ps1 to map out the network and locate valuable data on shared drives. From there, they move from one computer to another using common administrative tools that are likely already in your environment, such as PSExec, WinRM, and RDP. By living off the land, they blend in with normal network traffic, making them harder to detect. This is where you need to validate your security controls to ensure they can detect and block this kind of malicious internal movement.
Understanding who SafePay targets is key to assessing your own organization’s risk. This group doesn’t cast a wide, random net; they are strategic, focusing on specific industries and regions where they can cause the most disruption. For these organizations, an attack isn’t just a technical problem—it’s an operational and financial crisis that can have lasting consequences.
SafePay has a clear geographical focus, primarily hitting organizations in the United States, Germany, the United Kingdom, Australia, and Canada. Within these regions, they concentrate on industries that are highly sensitive to downtime, such as manufacturing, healthcare, and construction. These sectors are prime targets because their reliance on continuous operations and access to critical data makes them more likely to pay a ransom to restore services quickly. An attack on a manufacturing plant can halt production lines, while an attack on a hospital can put patient care at risk, raising the stakes significantly for defenders.
This group is known for using a double-extortion tactic, which puts immense pressure on its victims. First, they encrypt your critical files, changing their names to end with the ‘.safepay’ extension and deleting backup copies to complicate recovery. Then, they threaten to leak the sensitive data they stole if the ransom isn’t paid. This two-pronged attack leaves organizations in a difficult position, forced to weigh the cost of the ransom against the potential damage of a data breach and prolonged operational disruption. A ransom note left on compromised systems outlines their demands, starting the clock on a very difficult decision.
The financial demands from SafePay can be staggering, and they don’t discriminate based on size. In a single month, the group reportedly claimed 73 victims, making them one of the more active ransomware operations. While some of their targets are large enterprises with revenues exceeding $100 million, the majority are smaller businesses with revenues closer to $5 million. This demonstrates that organizations of all sizes are on their radar. For a smaller company, a significant ransom demand can be a devastating blow, highlighting the financial strain these attacks impose across the board.
Catching a ransomware attack early can be the difference between a minor incident and a full-blown crisis. SafePay operators, like many others, leave a trail of digital breadcrumbs as they move through your network. Knowing what to look for is your first line of defense. Pay close attention to these key indicators, as they often signal that an attack is in its early stages.
SafePay often gains its initial foothold using stolen credentials or by exploiting VPN weaknesses. Once inside, one of the first things attackers do is try to fly under the radar by disabling the very tools meant to spot them. If you see alerts that security software like Windows Defender or your endpoint protection has been turned off, treat it as a critical incident. This isn’t a random glitch; it’s a deliberate tactic to make their attack easier. A robust threat exposure management platform can help you continuously monitor for these changes and correlate them with other suspicious activities, giving you a clearer picture of a potential intrusion.
After disabling security tools, attackers focus on gaining more control. They work to escalate their privileges, aiming for administrator-level access that gives them the keys to the kingdom. Keep an eye out for unusual account activity, like a standard user account suddenly attempting to run administrative commands. At the same time, SafePay operators will actively hunt for and try to delete your backup software and shadow copies. This is a calculated move to sabotage your recovery efforts and ensure you have no choice but to consider the ransom. Validating your security controls can show you where these attempts might succeed before an attacker tries.
SafePay doesn’t stay put on one machine. Attackers use common IT administration tools like PSExec, WinRM, and RDP to move laterally from one computer to another. While these are legitimate tools, their use between workstations that don’t normally interact, or at odd hours, is a major red flag. You might also see rapid scanning of network shares and other critical parts of your infrastructure as they map out your environment. This reconnaissance phase is a precursor to data exfiltration and encryption. Understanding these attacker TTPs is crucial for spotting an active intrusion before widespread damage occurs.
Staying ahead of a threat like SafePay requires more than just a good defensive line; it demands foresight. This is where threat intelligence comes in. Instead of reacting to alerts, you can start anticipating an attacker’s next move. By integrating real-world data about active threats into your security strategy, you can shift from a broad, compliance-driven approach to a focused, threat-informed defense. This means you’re not just patching vulnerabilities; you’re fixing the ones that attackers are actually using right now.
Effective threat intelligence gives you context. It tells you who is attacking, what they’re after, and how they operate. For a ransomware group like SafePay, this information is critical. It helps you understand which of your assets are most likely to be targeted and which security gaps they are most likely to exploit. This allows your team to allocate resources more effectively, focusing on the risks that pose a genuine and immediate threat to your organization. With a platform that provides a unified view of these risks, you can turn raw intelligence into confident, decisive action.
To stop an attack, you first need to know what it looks like. Tracking active SafePay campaigns and their associated Indicators of Compromise (IoCs) is your early warning system. IoCs are the digital breadcrumbs attackers leave behind—things like malicious IP addresses, file hashes, or suspicious domain names. When your security tools are armed with up-to-date IoCs, they can spot and block SafePay activity before it escalates. Given that SafePay has quickly become a major global threat, monitoring threat feeds and intelligence reports for the latest IoCs is a non-negotiable part of a proactive defense.
If IoCs are the breadcrumbs, then Tactics, Techniques, and Procedures (TTPs) are the attacker’s playbook. Understanding SafePay’s TTPs means you know how they operate, from initial access to final impact. Research shows that SafePay often gets in by using stolen login details or exploiting weaknesses in internet-facing devices like VPNs and firewalls. By studying their methods, you can strengthen the specific areas they target. Instead of trying to defend against every possible attack vector, you can focus your efforts on countering the exact techniques SafePay is known to use, making your defenses much more efficient and effective.
Your vulnerability scanner probably gives you a list of flaws as long as your arm, and trying to patch everything at once is impossible. Threat intelligence helps you cut through the noise. SafePay operators are opportunistic; they look for organizations with weak security and exploit known vulnerabilities that are easy to weaponize. By correlating threat data with your own vulnerability scans, you can pinpoint the exact flaws that SafePay is actively exploiting in the wild. This allows you to create a vulnerability and threat prioritization strategy that focuses on closing the security gaps that matter most, significantly reducing your real-world exposure.
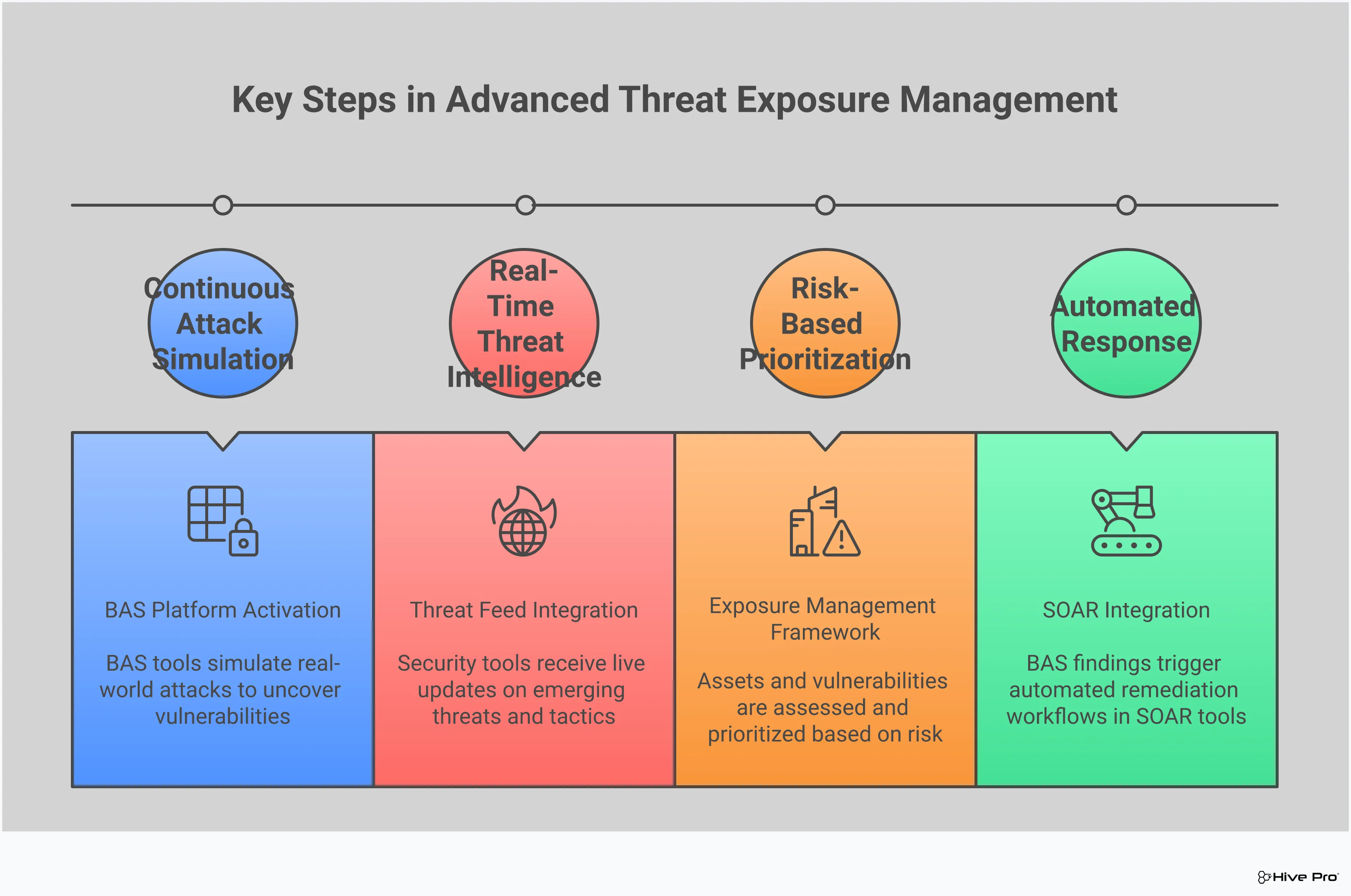
Knowing about a threat is one thing, but knowing if your defenses can actually stop it is another. This is where Breach and Attack Simulation (BAS) comes in. Instead of waiting for an attack to happen, BAS platforms let you proactively test your security posture by running controlled, real-world attack scenarios in your environment. Think of it as a continuous, automated penetration test that shows you exactly where your weaknesses are without causing any actual harm. It’s a safe way to stress-test your systems and find out how they’d perform during a real incident.
By using a BAS tool, you can move beyond theoretical security and get concrete proof of your resilience. These simulations mimic the exact tactics, techniques, and procedures (TTPs) used by threat actors like the group behind SafePay. The goal is to find security gaps before an attacker does. This process of adversarial exposure validation provides clear, actionable insights, helping your team prioritize fixes and confirm that your security controls are configured correctly and working as intended. It’s about replacing assumptions with certainty and giving your team the confidence that your defenses are truly effective.
To stop an attacker, you need to think like one. SafePay often gets in by using stolen login details or by finding weaknesses in VPNs. A BAS platform allows you to safely simulate these exact attack vectors against your own systems. You can run scenarios that test how your network would handle an intrusion attempt via compromised credentials or an unpatched VPN vulnerability. This gives you a clear picture of your exposure at the perimeter and helps you understand how an attacker might gain that initial foothold. By simulating these entry points, you can find and fix the gaps before they become a real security incident.
Once inside, SafePay operators are known to disable security programs and delete backup software to make recovery more difficult. Do you know if your security tools would stand up to these tactics? BAS helps you answer that question by testing the effectiveness of your existing controls. The simulation can attempt to stop security services or tamper with backup systems, just like the real ransomware would. This process validates whether your endpoint detection and response (EDR), antivirus, and data recovery solutions are not only deployed but are also resilient enough to withstand a direct assault. It’s the ultimate reality check for your security stack.
The threat landscape is always changing, which means your security posture needs to be assessed continuously. BAS isn’t a one-and-done activity; it’s a core component of a proactive security strategy. By regularly running simulations based on the latest threat intelligence, you can continuously assess your exposure to threats like SafePay. The results from these tests provide your team with the data needed to guide remediation efforts effectively. This approach allows you to shift from a reactive stance to a proactive one, using a unified platform to manage and reduce your threat exposure over time.
Building a solid defense against a threat like SafePay isn’t about finding a single magic bullet. It’s about creating layers of security that cover your technology, processes, and people. A proactive approach means you’re not just waiting to react to an attack, but actively strengthening your environment to prevent one from succeeding in the first place. By focusing on essential security controls, a resilient architecture, and a well-prepared team, you can significantly reduce your exposure to this ransomware. Let’s walk through the key steps to build a comprehensive defense that stands up to modern threats.
Your endpoints—laptops, servers, and workstations—are often the primary targets for ransomware. Start by enforcing multi-factor authentication (MFA) across all accounts. This simple step adds a critical security layer that makes it much harder for attackers to use stolen credentials. Next, implement application allowlisting. Using tools that only permit approved programs to run can effectively block ransomware and other malicious applications from ever executing. This moves you from a reactive stance of blocking known threats to a proactive one of only allowing known good. These foundational tools are your first and most important line of defense against an intruder gaining a foothold.
A strong security posture relies on multiple layers of defense. Your first priority should be a robust patch management program. You need to regularly update all your software to fix security weaknesses as soon as they are discovered, closing the door on known exploits. Beyond patching, it’s crucial to secure your network perimeter. Block any unmonitored devices from accessing critical network services like Remote Desktop Protocol (RDP) or Windows Remote Management (WinRM) from outside your network. Attackers frequently scan for and exploit these exposed services to gain initial access. By combining diligent patching with strict access controls, you create a much more resilient environment that can better withstand an attack.
Technology can only take you so far; your team is a vital part of your defense. Develop a clear incident response plan that outlines the exact steps to take to quickly find and deal with attacks. This plan should include maintaining offline or immutable backups and a tested disaster recovery process so you can restore operations without paying a ransom. You should also use systems that can detect and alert you to specific ransomware activities, such as attempts to disable security tools, delete backups, or exfiltrate data. Continuous security awareness training is also essential to help your team recognize and report phishing attempts, which are a common entry point for SafePay.
What’s the most common mistake organizations make that lets SafePay in? The most frequent oversight is failing to secure the network perimeter. SafePay operators are very effective at finding and exploiting unpatched VPNs, firewalls, or exposed RDP servers. They also rely heavily on stolen credentials, which often succeed because multi-factor authentication isn’t enforced everywhere. These aren’t complex, zero-day attacks; they are opportunistic strikes that take advantage of basic security gaps that are unfortunately still very common.
We already do vulnerability scanning. How is using Breach and Attack Simulation (BAS) different? Vulnerability scanning is essential for finding potential weaknesses, but it doesn’t tell you if those weaknesses can actually be exploited in your specific environment. A BAS platform takes the next step by safely mimicking the exact techniques an attacker would use to try and exploit those vulnerabilities. It validates whether your security controls—like your firewalls and endpoint protection—would actually detect and block a real attack, giving you proof of your resilience instead of just a list of potential problems.
We get tons of threat intelligence feeds. How do we make that information actually useful against a threat like SafePay? The key is to move from simply collecting intelligence to applying it. Instead of drowning in data, you need a way to connect it directly to your environment. A good threat exposure management platform will correlate intelligence about SafePay’s active campaigns with your own vulnerability data. This allows you to see which of your specific weaknesses are being targeted by this group right now, so you can prioritize patching the flaws that pose an immediate, real-world risk.
Besides encrypting our files, what makes SafePay’s double-extortion tactic so dangerous? The double-extortion model turns a security incident into a potential public relations crisis. Before they encrypt anything, the attackers steal a copy of your sensitive data. This means that even if you have perfect backups and can restore your systems, they still hold your data hostage. The threat of leaking confidential customer information, employee records, or intellectual property online adds immense pressure and complicates your entire response strategy.
My organization isn’t in one of the targeted industries. Are we still at risk? Yes, you are. While SafePay has shown a preference for certain sectors like manufacturing and healthcare, ransomware groups are fundamentally opportunistic. Their automated scanning tools are constantly searching the internet for any organization with an exploitable weakness, regardless of industry. If they find an easy way in, they will take it. Relying on being outside their typical target profile creates a false sense of security.