Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Communicating security needs to leadership can be a challenge when you’re just presenting a long list of technical flaws. The conversation shifts when you can talk about risk in clear business terms. Instead of saying “we have 500 critical vulnerabilities,” you can say “we have 15 vulnerabilities that pose a direct financial risk to our primary revenue stream.” This is the power of risk based vulnerability management (RBVM). It transforms your security program from a technical cost center into a strategic business function. By focusing on the threats that could actually impact operations, revenue, and reputation, you can justify resources and demonstrate a clear return on your security investment.
Risk-Based Vulnerability Management, or RBVM, is a smarter way to handle security weaknesses in your IT environment. Instead of trying to fix every single vulnerability your scanners find, this approach helps you focus on the ones that pose the greatest actual threat to your organization. Think of it as a strategic filter. It moves your team away from a reactive, “patch everything” cycle and toward a proactive stance where you address the most critical risks first.
This method combines data about the vulnerability itself with real-world threat intelligence and the business context of your assets. It answers crucial questions like: Is this vulnerability being actively exploited in the wild? Is it located on a mission-critical server? What would the business impact be if this asset were compromised? By layering these insights, you can create a truly prioritized remediation plan. This ensures your team’s valuable time and resources are spent on fixes that genuinely reduce your organization’s overall risk profile, rather than getting lost in a sea of low-impact alerts. Hive Pro’s approach to vulnerability and threat prioritization is built on this very principle.
The traditional approach to vulnerability management often feels like trying to boil the ocean. Scanners produce massive lists of vulnerabilities, many labeled “high” or “critical” based on generic scores, leaving security teams overwhelmed and unsure where to start. This method treats all assets as equally important and all critical-rated vulnerabilities as equally urgent, which is rarely the case. It also struggles to keep up with modern IT environments, often creating blind spots across cloud infrastructure, web apps, and IoT devices.
A risk-based approach, on the other hand, is all about context. It doesn’t just ask, “Is this a vulnerability?” It asks, “Is this a vulnerability that matters to us?” By considering which assets are most critical and which threats are most active, RBVM cuts through the noise. It helps you see the difference between a critical vulnerability on a non-essential test server and a less severe one on your primary customer database, allowing you to direct your efforts with precision.
At its core, RBVM is guided by a few key principles that work together to provide a clear picture of your risk landscape. First is a comprehensive understanding of your assets and their business value. You can’t protect what you don’t know you have, so a complete inventory is the foundation. Second is the integration of actionable threat intelligence. This means knowing which vulnerabilities have known exploits and are being used by attackers, information that teams like HiveForce Labs work to provide.
Finally, it’s about creating a customized risk score. This score combines the technical severity of a vulnerability with the business criticality of the affected asset and the current threat landscape. This allows you to move beyond generic ratings and build a remediation plan that is tailored specifically to your organization’s unique environment and risk tolerance.
If you’ve ever felt like you’re drowning in a sea of vulnerability alerts, you’re not alone. Traditional vulnerability management often feels like a never-ending game of whack-a-mole. It generates massive lists of issues, often sorted by a static severity score, and leaves your team scrambling to patch everything at once. This approach can lead to serious “vulnerability overload,” where the truly critical threats get lost in the noise. It’s a method that treats all vulnerabilities on all assets as equally important, which we know isn’t true.
Risk-based vulnerability management (RBVM) offers a smarter way forward. Instead of just looking at a vulnerability’s isolated severity rating, RBVM considers the bigger picture. It correlates multiple factors to determine actual risk, asking questions like: How severe is this flaw? Is there active chatter about it in the wild? How likely is it to be exploited? And most importantly, how critical is the asset it affects? This contextual approach helps you move from a reactive checklist to a proactive strategy, allowing you to focus your efforts on the threats that pose a genuine danger to your organization. It’s about understanding your unique vulnerability and threat prioritization to make informed, impactful decisions.
For years, the Common Vulnerability Scoring System (CVSS) has been the go-to for rating vulnerability severity. While it’s a useful starting point, relying on it alone is a recipe for burnout. The reality is that CVSS scores often label nearly 60% of all vulnerabilities as “high” or “critical.” When everything is a top priority, nothing is.
The biggest issue is that CVSS scores lack real-world context. A “critical” vulnerability on a test server that isn’t connected to the internet is far less risky than a “medium” vulnerability on your customer-facing payment portal. Without understanding the business context of the asset and the current threat landscape, a CVSS score is just a number. It doesn’t tell you which vulnerabilities are actively being exploited by attackers or which ones could cause the most damage to your business.
This is where RBVM really shines. It cuts through the noise by using a more intelligent approach to prioritization. By combining data on asset criticality, threat intelligence, and vulnerability severity, RBVM helps you pinpoint the small percentage of vulnerabilities that represent the vast majority of your risk. This allows your security team to stop chasing down every single alert and instead concentrate their limited time, budget, and energy on fixing the problems that matter most.
Modern platforms use sophisticated analytics and even machine learning to automate this process, giving you a clear, risk-ranked list of priorities. By focusing on the most critical vulnerabilities first, your team can make a much bigger impact on your overall security posture with less effort. It’s about working smarter, not just harder, to achieve a more secure and resilient environment.
At its core, RBVM is about prioritizing based on real-world threats, not theoretical ones. This approach is built on three key pillars: threat intelligence, asset criticality, and exploitability. Threat intelligence from sources like HiveForce Labs tells you which vulnerabilities attackers are actively targeting right now. Asset criticality helps you understand the business impact if a system were compromised—is it a development server or the database holding all your customer data?
Finally, exploitability assesses how easy it is for an attacker to take advantage of the flaw. By combining these factors, you can make much better security decisions. This strategic focus ensures you’re using your resources wisely and protecting your organization from the most immediate and significant dangers.
Switching to a risk-based approach feels like a big move, but it’s really about building a solid foundation with a few key components. Think of it less like flipping a switch and more like constructing a well-designed process. When you have these core building blocks in place, you create a sustainable program that moves your team from constantly fighting fires to proactively reducing your real-world exposure. Each piece builds on the last, giving you a clear, logical framework for making smarter security decisions. Let’s walk through what those essential blocks are.
You can’t protect what you don’t know you have. The first step in any strong RBVM program is getting a complete and accurate inventory of every asset across your environment—from servers and laptops to cloud instances and IoT devices. But just listing them isn’t enough. You also need to classify them based on their business criticality. A customer-facing database, for example, carries far more risk than a development server. This process of discovery and classification gives you the context needed to understand the potential impact of a vulnerability, helping you get a complete picture of your attack surface and focus your attention where it truly matters.
A vulnerability without an active exploit is a theoretical problem. A vulnerability with a known exploit being used in the wild is an immediate threat. This is where threat intelligence comes in. By integrating real-time data on what attackers are actually doing, you can see which weaknesses are being actively targeted. This allows you to separate the signal from the noise. Instead of chasing every single vulnerability, you can focus on the ones that pose a clear and present danger to your organization. Using in-house intelligence from dedicated research teams gives you an even greater edge, providing curated insights that are directly relevant to your industry and technology stack.
Once you know your assets and the threats they face, you need a way to connect the two. This is done by creating a custom risk scoring method that goes beyond generic CVSS scores. A meaningful risk score considers multiple factors: the business criticality of the asset, the severity of the vulnerability, and the likelihood of exploitation based on current threat intelligence. This tailored approach helps you prioritize exposure based on what it would actually mean for your business if a specific asset were compromised. It transforms a massive list of vulnerabilities into a manageable, prioritized roadmap for your remediation teams.
Your digital environment is never static. New assets are deployed, software is updated, and new threats emerge every day. That’s why a one-time scan is never enough. A successful RBVM program relies on continuous monitoring to keep your asset inventory and vulnerability data current. Instead of taking occasional snapshots, you need a system that constantly scans for weaknesses and changes in your environment. This proactive approach ensures you can quickly identify and respond to new risks as they appear. A platform that helps you continuously reveal your full attack surface is essential for maintaining a strong security posture over the long term.
Shifting to a risk-based approach is about moving from a reactive, checklist-driven mindset to a proactive, strategic one. Instead of trying to patch every single vulnerability that pops up—an impossible task for any team—you focus your energy on the threats that genuinely endanger your organization. This isn’t about ignoring vulnerabilities; it’s about intelligently prioritizing them based on real-world context. By understanding which flaws are most likely to be exploited and which assets are most critical to your business, you can make a measurable impact on your security posture without burning out your team. It’s the difference between fighting every fire and preventing the ones that could actually burn the building down. This strategic focus allows you to get ahead of attackers by fixing the most dangerous weaknesses first, transforming your vulnerability management program from a constant game of catch-up into a powerful defensive strategy. Ultimately, it’s about making smarter, data-driven decisions that protect the business where it’s most vulnerable, ensuring every action your team takes is both meaningful and effective.
A risk-based approach sharpens your focus on what truly matters: reducing exploitability. Traditional methods often leave teams chasing high CVSS scores that may have little relevance in their specific environment. In contrast, risk-based vulnerability management (RBVM) helps you pinpoint the vulnerabilities that pose an actual threat of exploitation. This strategic approach allows you to direct your remediation efforts toward the issues that attackers are actively targeting. By concentrating on genuinely high-risk flaws, you can make a direct and meaningful impact on your organization’s security, effectively narrowing the attack surface that adversaries can leverage. This shift ensures your team’s hard work translates into a stronger, more resilient defense.
Let’s be honest: no security team has unlimited time, budget, or people. A risk-based approach acknowledges this reality and helps you get the most out of the resources you have. Instead of spreading your efforts thin trying to address a massive backlog of vulnerabilities, you can concentrate your efforts on the most critical threats first. This prioritization means your team spends its valuable time on fixes that deliver the biggest security return on investment. It stops the cycle of constant firefighting and allows you to allocate your budget and personnel to the issues that could cause the most significant damage, ensuring your cybersecurity program operates with maximum efficiency.
When you have clear, risk-based priorities, your team can act faster and more decisively. Instead of debating which of the hundreds of “critical” vulnerabilities to tackle first, they have a clear roadmap based on data. This clarity dramatically reduces the mean-time-to-remediate (MTTR) for the vulnerabilities that matter most. In fact, organizations that use automated, risk-based prioritization can slash their remediation times for critical issues, directly shrinking the window of opportunity for attackers. By streamlining the decision-making process, you empower your team to move from detection to remediation with greater speed and confidence.
Meeting compliance requirements can often feel like a frantic scramble before an audit. A risk-based approach helps you move toward a state of continuous compliance by embedding these requirements directly into your daily security workflows. Many regulations and standards, like PCI DSS or HIPAA, are fundamentally concerned with protecting critical data and systems from significant threats. By prioritizing vulnerabilities based on risk, you are inherently addressing the very issues that auditors focus on. This alignment makes audit preparation much smoother and less stressful, as you can readily demonstrate a proactive, logical, and consistent process for managing your organization’s cyber risk.
Moving to a risk-based approach is all about smart prioritization. Instead of trying to fix every single vulnerability that pops up, you focus your energy on the ones that pose a genuine threat to your organization. This means looking beyond a simple CVSS score and asking more pointed questions about what each vulnerability means in the context of your business. A solid risk assessment process helps you cut through the noise and see which threats need your immediate attention. It’s about working smarter, not just harder, to reduce your overall exposure.
This process hinges on four key areas: understanding what’s most important to your business, knowing which threats are most likely to happen, seeing how they fit into your specific environment, and calculating the potential fallout if an attack succeeds. By systematically evaluating vulnerabilities through these lenses, you can create a clear, defensible roadmap for remediation that protects your most valuable assets from the most probable threats.
You can’t protect everything equally, so the first step is to figure out what you need to protect the most. Not all assets are created equal. A server that processes customer payments is far more critical than a printer in the marketing department. This is where you need to connect with business leaders to assign a value to each asset. Think about what would happen if a particular system went down. Would it halt operations? Cost you revenue? Damage your reputation? By classifying your assets based on their business criticality, you can ensure your security team directs its efforts toward the most dangerous problems first.
Once you know what’s important, you need to determine which threats are most likely to target those assets. This is where real-time threat intelligence becomes invaluable. A vulnerability might have a high severity score, but if there are no known exploits for it in the wild, it’s less of an immediate concern than a lower-scored vulnerability that attackers are actively using. You should be asking: Is there a public exploit available? Are threat actors talking about it? Is it part of a known attack campaign? Answering these questions helps you prioritize vulnerabilities based on genuine, real-world risk, not just theoretical severity.
A vulnerability doesn’t exist in a vacuum. Its actual risk level depends entirely on your specific environment. For example, a critical vulnerability on a server that’s isolated from the internet and has multiple security controls in place poses a much lower risk than the same vulnerability on a public-facing web server. You need to consider your existing security posture, network architecture, and any compensating controls. This contextual awareness is what separates a generic vulnerability scan from a true risk assessment. It helps you focus on the weaknesses that present the biggest actual risk to your organization, not just a theoretical one.
Finally, you need to think about the “so what?” factor. If a critical asset is compromised, what’s the potential damage? This isn’t just about technical impact; it’s about business impact. You should try to quantify this in terms your leadership understands, like potential financial loss, regulatory fines, operational downtime, or harm to your brand’s reputation. Understanding the potential impact in clear business terms helps everyone, from the security team to the C-suite, make better decisions about where to invest time and resources. It transforms the conversation from “we need to patch this” to “we need to patch this to prevent a potential million-dollar loss.”
Transitioning to a risk-based approach might seem like a huge undertaking, but you can break it down into manageable steps. Think of it as building a new, more efficient system piece by piece. The goal is to move from a reactive scramble to a proactive, strategic security posture. It starts with knowing what you have and ends with integrating security into your daily operations. This framework will help you focus your team’s efforts where they can have the greatest impact, ensuring you’re tackling the threats that pose a genuine risk to your organization. Let’s walk through the key phases of putting a successful RBVM program into practice.
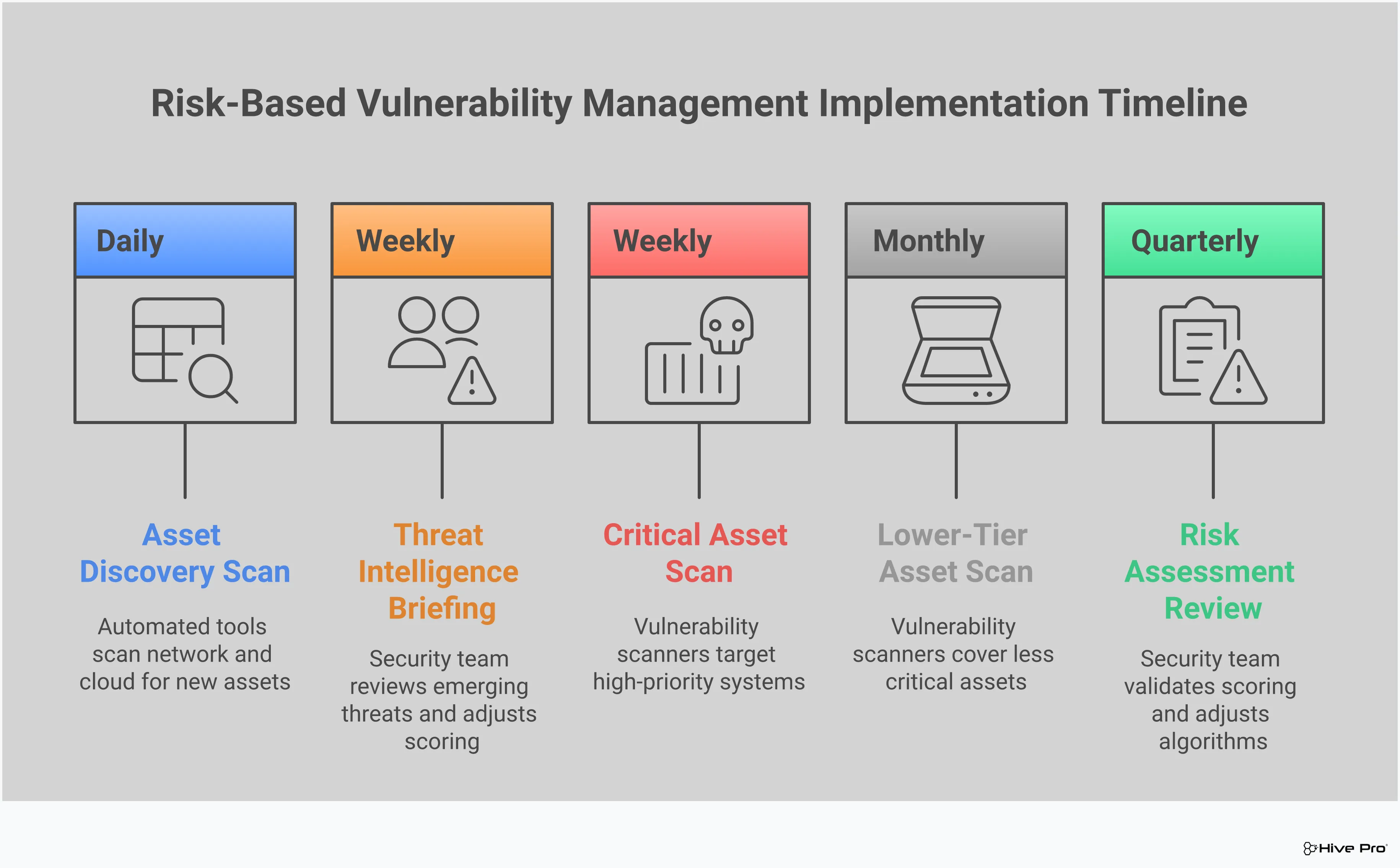
You can’t protect what you don’t know you have. That’s why the first step is always to create a comprehensive inventory of every asset across your organization. This isn’t just about listing servers and laptops; it includes everything from cloud services and IoT devices to applications and data repositories. A complete view of your total attack surface is the foundation of any effective security program. Once you have your list, the next move is to assess the business criticality of each asset. Which systems are essential for daily operations? Which ones store sensitive customer data? Answering these questions helps you understand the potential impact if an asset were compromised, which is a crucial piece of the risk puzzle.
With your asset inventory in hand, it’s time to define what “risk” means to your organization. This involves creating a risk scoring system that goes beyond standard CVSS scores. Your criteria should evaluate vulnerabilities based on a combination of factors: the business importance of the affected asset, the likelihood of an attack based on real-world threat intelligence, and the potential damage—financial or reputational—a successful exploit could cause. By establishing clear thresholds for what constitutes a critical, high, medium, or low risk, you create a consistent framework for vulnerability and threat prioritization. This ensures everyone on your team is on the same page and that you’re focusing on the threats that truly matter.
Identifying and prioritizing risks is only half the battle; you also need a clear plan for fixing them. This is where efficient remediation workflows come in. Based on your risk scores, create a prioritized list of actions for your team. This isn’t just a to-do list; it’s a strategic plan with clear ownership and deadlines. For example, you might set a policy that all critical vulnerabilities must be patched within 48 hours, while low-risk issues can be addressed in the next regular maintenance cycle. Automating these workflows within a unified platform like Uni5 Xposure can help assign tasks, track progress, and ensure nothing falls through the cracks, turning your risk intelligence into swift, decisive action.
Finally, for RBVM to be truly effective, it needs to be woven into the fabric of your daily operations, not treated as a separate, periodic task. This means integrating security assessments into your core processes. When the development team is building new software, security should be part of the conversation from the start (a core principle of DevSecOps). When the IT team is deploying a new system, a vulnerability assessment should be a standard part of the process. This continuous approach ensures that security is always a consideration, helping you identify and address potential risks before they become major problems. It shifts your security posture from being reactive to proactively resilient.
Having a solid RBVM strategy is the first step, but executing it effectively requires the right technology. The goal is to build a tech stack that automates data collection, adds crucial context, and gives your team a clear, unified view of your risk landscape. Without the right tools, even the best-laid plans can get bogged down by manual processes and data overload. Think of your tools as the engine that powers your program, turning raw data into actionable insights that guide your remediation efforts.
These tools don’t operate in silos; they work together to create a comprehensive system that helps you move from simply finding vulnerabilities to proactively reducing your overall exposure. From initial scanning to intelligent prioritization, each piece plays a critical role in making your RBVM program efficient, effective, and scalable. The right combination of technology will not only help you identify which vulnerabilities to fix first but will also provide the evidence needed to communicate risk to stakeholders and justify resource allocation. Let’s look at the key platforms and engines that form the backbone of a successful RBVM program.
Think of vulnerability assessment platforms as your foundation. These are the scanners and agents that continuously search your environment—from servers and endpoints to cloud instances and applications—to identify vulnerabilities. They are essential for the discovery phase, creating the initial list of potential weaknesses you need to address. While these platforms are great at telling you what vulnerabilities exist, they often lack the context to tell you which ones matter most to your organization. An effective RBVM program uses this raw data as a starting point, feeding it into more advanced systems for analysis and prioritization.
This is where you add real-world context to your vulnerability data. Threat intelligence feeds provide crucial information on which vulnerabilities are being actively exploited by attackers in the wild. Instead of just relying on a theoretical severity score, you can see which threats are trending, what tactics attackers are using, and if a specific vulnerability is part of a known exploit kit. Integrating actionable threat intelligence helps you separate the theoretical risks from the clear and present dangers, allowing your team to focus on the vulnerabilities that pose an immediate threat to your organization.
CTEM platforms are the evolution of traditional vulnerability management. They serve as the central hub for your RBVM program, pulling together data from your vulnerability scanners, asset inventories, and threat intelligence feeds into a single, cohesive view. A CTEM platform goes beyond just managing known vulnerabilities; it helps you understand your entire attack surface and how different exposures connect. By adopting a continuous, risk-based approach, you can maintain a proactive stance against evolving threats instead of constantly reacting to new ones. This unified view is critical for breaking down data silos and making informed, strategic security decisions.
If CTEM platforms are the hub, automated prioritization engines are the brains of the operation. These engines use sophisticated algorithms to analyze all the data you’ve collected—vulnerability severity, asset criticality, and real-time threat intelligence—to score and rank your risks. This is what allows you to move past the noise of thousands of low-risk alerts. Organizations that implement this kind of automated prioritization can drastically reduce the time it takes to remediate critical vulnerabilities. By automating the analysis, you free up your team to focus on fixing the issues that truly matter, making your remediation efforts faster and far more effective.
Making the switch to a risk-based approach is a smart move, but it’s not always a straight path. Like any significant operational shift, implementing RBVM comes with a few common hurdles. Many teams find themselves wrestling with an overwhelming number of alerts, struggling with incomplete asset data, or trying to get different departments on the same page.
The good news is that these challenges are well-understood and completely solvable. Thinking through them ahead of time helps you build a more resilient and effective program from day one. It’s less about finding a perfect, one-size-fits-all solution and more about adopting the right mindset and tools, like a Continuous Threat Exposure Management (CTEM) platform, to create a clear, proactive security workflow. Let’s walk through the most common obstacles and the practical steps you can take to address them.
If your team feels like they’re drowning in alerts, you’re not alone. Traditional vulnerability scanners often flag a huge percentage of vulnerabilities as “high” or “critical” based on generic CVSS scores, even when many pose little actual threat to your organization. This constant noise leads to alert fatigue, where your team is so overwhelmed that they can’t easily spot the truly dangerous threats.
The solution is to cut through the noise with better context. An RBVM strategy helps you prioritize vulnerabilities based on real-world threat intelligence and business impact. Instead of trying to fix everything at once, your team can focus its energy on the weaknesses that attackers are actively exploiting or that protect your most critical assets.
You can’t protect what you don’t know you have. An effective RBVM program is built on a foundation of a complete and accurate asset inventory. Without a clear picture of every device, application, and cloud instance in your environment—and its business purpose—your risk assessments will always be based on incomplete information. This can lead to miscalculated priorities and critical blind spots.
To solve this, you need to move beyond static spreadsheets and embrace continuous attack surface management. This involves implementing processes and tools that automatically discover, classify, and map all your assets. By understanding what each asset is and how critical it is to your operations, you can make much more accurate and defensible decisions about where to focus your remediation efforts.
Vulnerability management isn’t just a job for the security team; it’s a shared responsibility. Too often, security teams identify issues and simply “throw them over the wall” to IT or DevOps for remediation, creating friction and delays. This siloed approach doesn’t work because it lacks shared context and goals, leaving IT teams struggling to understand which of the hundreds of requests to tackle first.
RBVM acts as a common language that helps bridge this gap. When you can clearly articulate why a specific vulnerability is a top priority—linking it to active threats and potential business impact—it fosters more productive conversations. By creating clear remediation workflows and giving all teams a unified view of risk, you encourage a collaborative culture where everyone understands their role in protecting the organization.
Adopting RBVM is as much a cultural shift as it is a technical one. It requires moving your team away from a compliance-driven, “patch everything” mindset to a more strategic, risk-informed approach. Team members who are used to relying solely on scanner reports and CVSS scores may need support and training to start thinking like an attacker and prioritizing based on a wider range of data points.
The key is to invest in your people and your processes. Provide training on threat intelligence and risk assessment principles. At the same time, equip your team with tools that automate the heavy lifting of data correlation and prioritization. This empowers them to make faster, smarter decisions without needing to be seasoned threat analysts, turning vulnerability management into a sustainable, ongoing practice.
Putting a risk-based vulnerability management program into practice requires more than just the right tools. It’s a strategic shift that involves your people, processes, and a commitment to continuous growth. By adopting a few key best practices, you can build a program that not only works but also evolves with your organization and the threat landscape. These habits help you move from a reactive cycle of patching to a proactive state of cyber resilience, ensuring your efforts are always focused on what truly matters.
A successful RBVM program needs a solid foundation. That starts with clear governance that outlines roles, responsibilities, and processes, ensuring everyone knows their part in reducing risk. This framework should align your security efforts directly with your organization’s business goals, making it clear why certain vulnerabilities get top priority. To track your progress, establish meaningful metrics. Instead of just counting patched vulnerabilities, measure the actual reduction in your overall risk score, the time it takes to remediate critical threats, and the percentage of critical assets covered. This data-driven approach helps you demonstrate the program’s value and make smarter decisions.
The cyber threat landscape is anything but static, and your RBVM program shouldn’t be either. Treat it as a living process that requires constant refinement. Regularly review your workflows, risk scoring criteria, and remediation timelines to find areas for improvement. Research shows that organizations using risk-based approaches significantly cut down remediation times for critical issues. Adopting a Continuous Threat Exposure Management (CTEM) mindset is key here. By continuously monitoring your attack surface and adapting your strategy based on new intelligence and performance data, you ensure your defenses remain effective against the latest threats.
Your team is your greatest asset in the fight against cyber threats. The most advanced tools can’t reach their full potential without skilled professionals to manage them. Investing in ongoing training is crucial for keeping your team’s skills sharp and up-to-date with emerging threats and technologies. This goes beyond the security team; developers, IT operations, and other stakeholders should also understand their role in the vulnerability management lifecycle. Fostering a culture that prioritizes security and collaboration ensures that everyone is working together toward the common goal of protecting the organization. This shared responsibility makes your entire security posture stronger.
How do you know if your RBVM program is actually working? By consistently measuring its effectiveness. Define key performance indicators (KPIs) that reflect your program’s goals, such as Mean Time to Remediate (MTTR) for high-risk vulnerabilities or the reduction of your overall attack surface. Tracking these metrics over time provides concrete evidence of your program’s impact. This data is invaluable for communicating success to leadership and securing future investment. It also helps you meet compliance requirements by demonstrating a proactive and documented approach to managing cyber risk, turning security from a cost center into a clear business enabler.
How is RBVM different from just prioritizing vulnerabilities with high CVSS scores? Think of CVSS scores as a single ingredient, while RBVM is the entire recipe. A high CVSS score tells you a vulnerability is technically severe in a vacuum, but it doesn’t tell you if it’s a real threat to your organization. RBVM adds the missing context by layering in other critical factors, like whether attackers are actively exploiting the flaw and how important the affected asset is to your business. This gives you a much more accurate picture of your actual risk.
My team is already swamped. Will switching to RBVM add more work? It’s a common concern, but the goal of RBVM is actually to reduce your team’s workload, not add to it. By helping you focus on the small percentage of vulnerabilities that pose the most significant threat, it eliminates the wasted effort spent chasing down low-risk issues. Instead of drowning in a sea of alerts, your team gets a clear, prioritized list, allowing them to work more efficiently and make a bigger impact on your security posture with less burnout.
What’s the most important first step to get started with RBVM? The most crucial first step is getting a complete and accurate inventory of all your assets. You simply can’t protect what you don’t know you have. Once you have a full picture of your environment, you can begin classifying those assets based on their business criticality. This foundational step provides the context you need to make every subsequent risk decision meaningful and effective.
Does RBVM mean we can just ignore vulnerabilities that are scored as ‘low’ or ‘medium’? Not at all. RBVM isn’t about ignoring vulnerabilities; it’s about intelligently sequencing your remediation efforts. While you’ll focus your immediate attention on the most critical risks, lower-priority issues still belong in your backlog. The difference is that you can address them during regular maintenance cycles instead of dropping everything for a flaw that poses little immediate danger. This ensures nothing gets forgotten, but your most urgent work always comes first.
How does RBVM relate to a Continuous Threat Exposure Management (CTEM) program? RBVM is a core component of a modern CTEM program. While RBVM focuses specifically on prioritizing known vulnerabilities, CTEM takes a broader view of your entire attack surface, including misconfigurations, identity issues, and other potential exposures. Think of RBVM as the “prioritization” phase within the larger, continuous CTEM lifecycle of discovery, prioritization, validation, and remediation.