Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
A long list of vulnerabilities without context isn’t a security strategy—it’s just noise. Legacy vulnerability scanners are great at finding potential flaws, but they often fail to answer the most important question: “What should we fix right now?” This is why Threat Exposure Management (TEM) represents such a critical evolution. A modern TEM program moves beyond simple scanning by enriching vulnerability data with real-time threat intelligence and business context. This allows you to prioritize the handful of exposures that pose a genuine, immediate risk to your organization. This guide explains the crucial difference between legacy scanning and modern exposure management, and explores the recommended threat exposure management tools in automated security that provide the actionable intelligence your team needs to focus its efforts effectively.
Think of Threat Exposure Management (TEM) as your security team’s strategic game plan for cyber defense. It’s a continuous process of identifying, prioritizing, and managing risks across every potential entry point an attacker could use. The main goal is to shrink your attack surface and reduce your overall risk by giving you a clear, unified picture of your security posture. Instead of just reacting to threats as they pop up, a modern TEM approach helps you get ahead of them.
This isn’t just about running scans and patching vulnerabilities. It’s a holistic strategy that involves understanding your entire digital footprint—from on-premise servers to cloud assets and third-party services. By continuously monitoring your total attack surface, you can spot weaknesses before they’re exploited. This approach transforms security from a series of disconnected tasks into a cohesive, proactive program. It allows teams to stop chasing endless alerts and focus their efforts on the threats that truly matter to the business, making security operations more efficient and effective.
For years, many security teams operated in a reactive mode, waiting for an alert to signal a problem and then scrambling to fix it. The shift to proactive security flips that model on its head. A strong TEM program is designed to prevent cyberattacks before they can even start. It uses threat intelligence to anticipate an attacker’s next move and strengthen defenses against emerging risks. This means you’re not just patching known holes; you’re building a more resilient security posture.
This proactive stance is built on the foundation of continuous monitoring. By keeping a constant watch over your environment, security teams can identify and respond to threats as they appear, significantly reducing the likelihood of a successful attack. It’s the difference between having smoke detectors and having a 24/7 fire watch. You’re actively looking for signs of trouble, which allows you to act with speed and precision, neutralizing threats before they can cause real damage.
A comprehensive TEM solution is built on a few key pillars that work together to provide complete visibility and control. First is continuous monitoring, which involves constantly scanning your entire digital presence to find weak spots and potential exposures. Next, and just as crucial, is vulnerability and threat prioritization. Not all vulnerabilities carry the same level of risk, so a good TEM platform helps you focus on the ones that pose the most immediate and significant threat to your organization.
This prioritization is powered by up-to-date threat intelligence. To be effective, a TEM solution must incorporate real-world data from a wide range of sources, including security reports, government warnings, and insights from research teams like HiveForce Labs. This intelligence provides the context needed to understand which threats are actively being exploited in the wild. Finally, all of this comes together to give you a complete understanding of your security situation, covering everything from internal systems to external partners.
Choosing a Threat Exposure Management (TEM) platform is a significant decision. The right tool can transform your security posture from reactive to proactive, but the market is crowded with options that all promise to solve your problems. To cut through the noise, you need to focus on the core capabilities that deliver real value. A top-tier TEM platform isn’t just about finding vulnerabilities; it’s about providing a continuous, unified view of your entire security landscape.
The goal is to find a solution that acts as a central hub for your security operations, connecting the dots between assets, vulnerabilities, and active threats. It should give your team the context they need to prioritize what truly matters, automate routine tasks, and integrate smoothly with the tools you already use. Think of it as the command center for your defense strategy. As you evaluate different platforms, look for these five essential features. They are the building blocks of a modern, effective threat exposure management program and will help you move beyond simply managing vulnerabilities to actively reducing your organization’s risk.
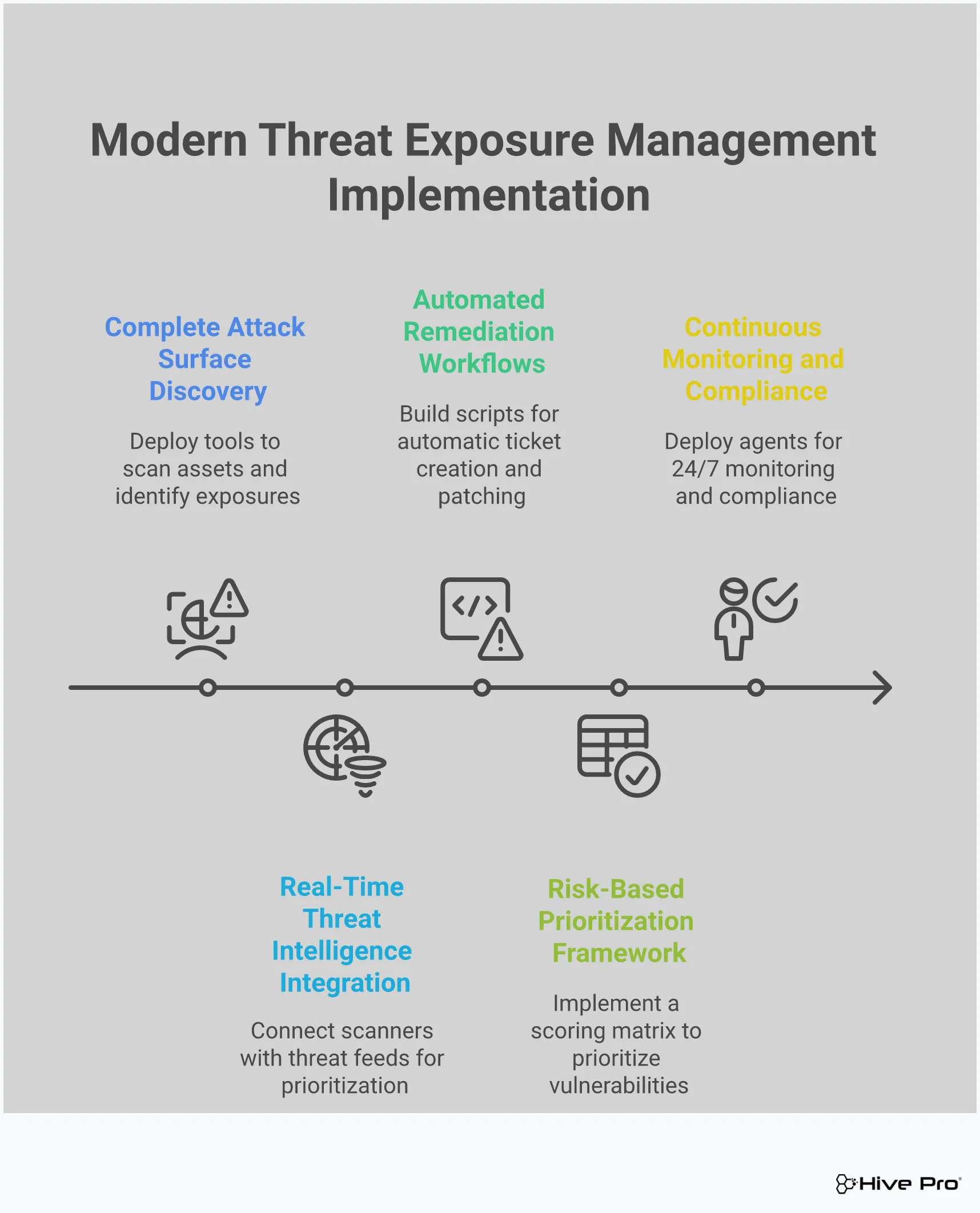
You can’t protect what you can’t see. A fundamental requirement for any TEM platform is the ability to provide complete visibility across your entire digital footprint. This means discovering and mapping every asset, from on-premise servers and employee laptops to cloud instances, web applications, and IoT devices. A comprehensive platform should provide total attack surface management to give you a single, unified inventory. This continuous discovery process ensures that no shadow IT or forgotten server becomes an entry point for an attacker. Without this complete picture, your security efforts will always have blind spots.
A long list of vulnerabilities is just noise. The key to effective security is knowing which threats to fix first. A leading TEM platform enriches vulnerability data with real-time threat intelligence, giving you the context needed to act decisively. This means incorporating data from multiple sources—like government advisories, dark web chatter, and expert security research—to understand which vulnerabilities are actively being exploited in the wild. This vulnerability and threat prioritization helps your team focus its limited resources on the exposures that pose an immediate and genuine risk to your organization, rather than chasing down low-priority issues.
Finding threats is only half the battle; fixing them is what counts. Modern TEM platforms help close the loop by automating parts of the remediation process. This can range from creating tickets automatically in your IT service management system to running scripts that patch simple misconfigurations. By automating these routine tasks, you can significantly reduce your mean time to remediate (MTTR) and free up your security analysts to work on more complex and strategic initiatives. Automation ensures that critical fixes are applied quickly and consistently, shrinking the window of opportunity for attackers.
Your TEM platform shouldn’t be a silo. To be truly effective, it must integrate seamlessly with your existing security and IT ecosystem. Look for a solution with robust, pre-built integrations for tools like SIEMs, EDRs, and ticketing systems. A strong API is also critical, as it allows you to share data and automate workflows across your entire security stack. This creates a unified system where information flows freely, eliminating gaps in visibility and ensuring that every team is working with the same accurate, up-to-date information. This level of integration is key to building a cohesive and responsive security operation.
Demonstrating compliance with regulations like HIPAA, PCI DSS, and GDPR is a constant pressure for security teams. A top TEM platform simplifies this process by providing automated reporting and continuous monitoring capabilities. It should allow you to easily generate reports that show your security posture against specific regulatory frameworks and track your progress over time. These clear, data-driven reports are not only essential for passing audits but also for communicating risk and demonstrating the value of your security program to executives and the board. This helps you maintain a strong compliance posture with far less manual effort.
Once you know what you’re looking for, it’s time to see what the market has to offer. The right Threat Exposure Management (TEM) platform will feel like a natural extension of your security team, giving you the visibility and control needed to act decisively. Different solutions have different strengths, so it’s helpful to understand the landscape before you start scheduling demos. We’ll look at a few top contenders to give you a sense of what’s available and how to think about the overall value of your investment.
The Hive Pro Uni5 Xposure Platform is designed to give you a constant, real-time view of your entire attack surface. Instead of waiting for monthly scans, it continuously discovers new digital assets across all your environments—from on-premise to cloud—in minutes or hours. This approach closes the visibility gaps where attackers often hide. By combining automated scanning, risk assessment, and remediation guidance in one place, Uni5 Xposure helps your team move from a reactive posture to a proactive one. It’s built to find and help you fix problems quickly, ensuring there are no hidden weak spots for threats to exploit.
As you research, you’ll come across other names in the TEM space. For example, solutions like Edgescan are known for providing a clear view of the attack surface and uncovering hidden assets like APIs. Others, such as CrowdStrike Falcon Exposure Management, use AI to deliver a comprehensive picture of your environment and automate vulnerability management. The common thread among these tools is their ability to map out all the digital components of your organization that could be targeted. Understanding your complete attack surface is the foundational first step, and many modern platforms are built to handle this complex task.
Investing in a TEM program is about more than just buying software; it’s about fundamentally improving your security outcomes. A complete program is essential for protecting your organization from breaches and minimizing the damage from any cyber threats that do get through. In fact, Gartner predicts that by 2026, organizations that base their security investments on a TEM program will be three times less likely to suffer a breach. The ROI comes from this risk reduction. By focusing on vulnerability and threat prioritization, you can direct your resources to the issues that pose a genuine threat, preventing costly incidents before they happen.
Choosing a Threat Exposure Management (TEM) platform isn’t just about buying software; it’s about adopting a new, proactive security philosophy. The right tool can transform your team’s workflow from a constant fire drill to a strategic operation. But with so many options, how do you find the perfect fit? It comes down to a thoughtful evaluation of your unique environment, existing tech stack, and long-term security goals.
Think of this process as building a custom security toolkit. You wouldn’t use a hammer to turn a screw, and you shouldn’t pick a TEM tool that doesn’t align with your specific needs. A platform that works wonders for a cloud-native startup might not be the best choice for a large enterprise with complex on-premise infrastructure. By breaking down the decision into clear, manageable steps, you can confidently select a solution that not only addresses your current challenges but also scales with you as your organization and the threat landscape evolve. Let’s walk through the key areas to focus on to ensure you make a smart, sustainable investment.
Before you even look at a demo, you need a clear scorecard. What does a successful TEM platform look like for your team? Start by listing your non-negotiables. The platform must be able to provide a complete picture of your total attack surface, from your servers and endpoints to ephemeral cloud assets and third-party services. It should also connect identified vulnerabilities with real-world threat intelligence to help you prioritize what actually matters. Look for a tool with clear, intuitive dashboards and automated reporting that can be easily understood by everyone from your security analysts to the C-suite. Finally, consider scalability. Your chosen solution needs to handle massive amounts of data without breaking a sweat, especially as your digital footprint grows.
A TEM platform doesn’t operate in a vacuum. It needs to play well with the security tools you already have in place. Make a list of your essential systems, like your SIEM, SOAR, and EDR solutions, and confirm that any potential TEM tool can integrate seamlessly. This is crucial for creating a unified view of your security posture and avoiding dangerous visibility gaps. A key part of this integration is the ability to pull in high-quality threat intelligence. The best TEM platforms leverage data from multiple sources—including proprietary research, government warnings, and dark web monitoring—to give you the context needed to understand and act on emerging threats. This is where a strong in-house research team like HiveForce Labs can be a major differentiator.
Implementing a TEM tool will require resources, both in terms of budget and team bandwidth. As you evaluate options, think about how the platform will fit into your existing workflows. A good TEM solution should help you focus your team’s efforts where they’ll have the most impact. It does this by helping you decide which fixes are most critical based on both the severity of the vulnerability and its potential business impact. This allows you to create a strategic remediation plan that strengthens your defenses against the most likely attack vectors. The ultimate goal is to use the platform’s intelligence to proactively improve your security controls and stop attacks before they can even start.
How will you know if your new TEM program is successful? You need to define your key performance indicators (KPIs) from day one. The most obvious metric is a reduction in overall risk, which you can track by measuring the size of your attack surface and the number of critical vulnerabilities over time. You should also assess how the tool improves your team’s efficiency. Are you finding and fixing threats faster? Is your mean time to respond (MTTR) going down? A successful TEM implementation should also help you make smarter decisions about your security budget, ensuring you’re investing in the areas that provide the greatest risk reduction.
Choosing the right Threat Exposure Management (TEM) platform is a huge step, but the real work begins once you bring it into your environment. A successful implementation isn’t just about flipping a switch; it’s about integrating the tool into your team’s daily rhythm and building solid processes around it. Think of it as laying the foundation for a more proactive, resilient security posture. By focusing on a smart setup, continuous team development, and clear protocols, you can make sure your new platform delivers on its promise to reduce your organization’s risk.
Your first move is to ensure your TEM platform can see everything. A successful setup starts with a comprehensive discovery process that maps your entire digital footprint. Make sure your tool can scan all your digital systems, from on-premise servers and employee laptops to temporary cloud instances and third-party services. This complete visibility is the only way to get a true picture of your total attack surface.
Once you have that visibility, configure the platform to connect vulnerabilities with real-time threat intelligence. This context is what separates a modern TEM solution from a legacy scanner. It allows you to move beyond generic severity scores and prioritize threats based on which ones are actively being exploited. Finally, customize your dashboards and reporting so that everyone from your security analysts to the C-suite can understand the organization’s risk posture at a glance.
A powerful tool is only effective in the hands of a well-trained team. Before you go live, invest time in training everyone who will interact with the platform. This goes beyond just showing them which buttons to click. Help them understand the strategy behind the tool, what the automation can and cannot do, and how its insights should inform their decisions.
Beyond formal training, foster a culture of collaboration. Your TEM platform will surface issues that touch multiple departments, so it’s crucial to encourage regular conversations between your security, IT, and development teams. When everyone understands the shared goal of reducing exposure, you can break down silos and create a more unified and effective response to threats. This collaborative approach ensures that security is a shared responsibility, not just a task for one department.
You can’t fix every vulnerability at once, and you shouldn’t try to. The goal is to address the issues that pose the greatest actual risk to your business. Use your TEM platform to build a risk prioritization framework that helps your team focus its efforts. This framework should use the platform’s intelligence to decide which threats are most critical to address first, based on factors like exploitability, asset criticality, and potential business impact.
This process also involves looking at your existing security controls. Your TEM solution can help you perform an honest assessment of your current tools and identify gaps in your defenses. By understanding which controls are underperforming, you can make informed decisions about where to invest your resources for the biggest security gains, ensuring you’re strengthening your posture where it matters most.
Threat exposure is not a static problem, so your approach to managing it can’t be either. A one-time scan is just a snapshot; true security comes from continuous vigilance. Establish protocols for ongoing monitoring to regularly check your digital presence for new weak spots and potential risks. This should be an automated, continuous process that gives your team a real-time view of your security posture.
This proactive monitoring is what allows your team to find and react to threats as they emerge, significantly reducing the likelihood of a successful attack. By making continuous monitoring a core part of your security program, you shift from a reactive cycle of incident response to a proactive strategy of continuous threat exposure management. This constant awareness is the key to staying ahead of attackers and maintaining a strong defense.
Bringing a new platform into your security stack can feel like a major project, but it doesn’t have to be a headache. Most of the hurdles teams face when rolling out a Threat Exposure Management (TEM) solution are predictable and, more importantly, preventable. With a bit of planning, you can ensure a smooth transition and start seeing value from your investment right away.
The key is to think through the entire lifecycle of the tool before you even sign a contract. This means considering how it will connect with your existing systems, who will manage it, what data it will need, and how you’ll confirm it’s watching over your entire environment. By addressing these common challenges head-on, you set your team up for a successful implementation that strengthens your security posture from day one. Let’s walk through the four biggest areas to focus on.
Your TEM platform shouldn’t be another data silo. For it to be truly effective, it needs to communicate seamlessly with the rest of your security ecosystem, including your SIEM, EDR, and patch management systems. When your tools can share information freely, you get a unified view of your exposure without the blind spots that disconnected systems create. Before committing to a solution, ask for a list of native integrations and review its API capabilities. A platform with a robust and flexible API, like the Uni5 Xposure Platform, allows you to build custom connections, ensuring it fits perfectly into your existing workflows instead of forcing you to build new ones.
Let’s be realistic: not every security team has a dedicated data scientist or a squad of automation engineers. Some of the most advanced TEM tools rely on complex technologies like AI and machine learning, and a common hurdle is finding team members with the right skills to manage them. When evaluating platforms, pay close attention to the user interface and the level of expertise required to operate it. Look for a solution that automates complex analysis and presents findings in a clear, actionable way. Also, consider the vendor’s training and support resources. A great tool becomes even better when your team feels confident using it to its full potential.
A TEM platform is powered by data. The more comprehensive and accurate the data it ingests, the more valuable its insights will be. Before you begin implementation, it’s essential to map out your data sources. This includes everything from asset inventories and vulnerability scanners to cloud configuration managers and threat intelligence feeds. Developing a clear data management strategy ensures all relevant information is collected, normalized, and fed into the platform correctly. This initial work pays off by giving you a truly complete picture of your attack surface and enabling more effective threat prioritization from the start.
You can’t protect what you can’t see. One of the biggest mistakes organizations make is failing to achieve complete coverage of their digital environment. Your attack surface extends far beyond your on-premise servers; it includes cloud infrastructure, SaaS applications, IoT devices, and even third-party partner systems. To get the most out of your TEM tool, you need a thorough understanding of this entire landscape. Take the time to map your complete digital footprint and ensure your chosen solution can monitor all of it. This comprehensive visibility is the foundation for an effective threat exposure management program and is critical for preventing attacks.
A threat exposure management program isn’t a one-and-done project. The digital landscape is constantly shifting, with new technologies, evolving threats, and an expanding attack surface. To stay effective, your TEM program must be built for the long haul. This means creating a strategy that is not only robust today but also flexible enough to adapt to the challenges of tomorrow.
Future-proofing your program involves a commitment to continuous improvement and an awareness of the broader security ecosystem. By focusing on scalability, staying current with emerging trends, and leveraging dynamic threat intelligence, you can ensure your security posture remains strong and resilient. Let’s walk through the key areas to focus on to build a TEM program that lasts.
To maintain strong security, you need a constant, real-time view of your entire environment. The days of monthly or even weekly scans are behind us. Modern TEM platforms should offer continuous discovery, identifying new digital assets across all your systems—from the cloud and on-premise servers to partner networks—in minutes or hours. This gives you a complete and current picture of your total attack surface. As your organization adopts new technologies, your TEM tool must keep pace, integrating these new assets into its monitoring and assessment processes without missing a beat. This proactive approach ensures there are no hidden weak spots for attackers to exploit.
As your business grows, your security operations must grow with it. A scalable TEM platform is essential for managing an expanding digital footprint. Before you commit to a tool, make sure it can handle an increase in assets, data volume, and user activity without a drop in performance. Your platform should be able to scan all your digital systems, including temporary cloud instances, servers, and third-party services. A key part of scaling effectively is automation. The right tool will connect identified vulnerabilities with relevant threat information to help you prioritize risks and automate remediation workflows, freeing up your team to focus on more strategic initiatives instead of getting bogged down in manual tasks.
A static defense is a losing battle. Cyberattacks are always changing, which is why your TEM program must be powered by dynamic, up-to-date threat intelligence. This means going beyond standard vulnerability databases and incorporating intelligence from a wide range of sources, including security reports, government warnings, and even chatter from the dark web. A strong TEM program uses this intelligence to get ahead of attacks before they happen. By understanding the tactics, techniques, and procedures (TTPs) of current threat actors, you can proactively strengthen your defenses. This is where a dedicated research team, like HiveForce Labs, becomes invaluable, providing the context needed to turn raw data into actionable security improvements.
How is Threat Exposure Management different from the vulnerability management I’m already doing? Think of it as a strategy versus a task. Traditional vulnerability management often focuses on scanning known assets and patching a long list of vulnerabilities based on generic severity scores. Threat Exposure Management is a continuous program that looks at your entire digital footprint—including cloud services and shadow IT—and prioritizes what to fix based on real-world threat intelligence. It’s about proactively reducing your risk by focusing on the exposures attackers are most likely to use against you, not just checking boxes on a scan report.
My team is already overloaded. Won’t this just add another tool to manage? I completely get that concern, but a good TEM platform should actually reduce your team’s workload. By connecting vulnerabilities to active threats, it cuts through the noise of endless alerts and tells you exactly what needs your attention right now. It helps you focus your limited time and resources on the handful of issues that pose a genuine risk to the business. Plus, with automation for tasks like ticketing and reporting, it frees your analysts from routine work so they can concentrate on more strategic security initiatives.
With thousands of vulnerabilities, how do I realistically decide what to fix first? This is the core problem that a modern TEM program solves. Instead of relying solely on a CVSS score, a strong platform enriches that data with up-to-the-minute threat intelligence. It helps you see which vulnerabilities are actively being exploited in the wild, which ones are part of a known attacker’s playbook, and how critical the affected asset is to your business. This context allows you to create a clear, risk-based action plan and confidently tackle the most urgent threats first.
What’s the single most important first step to starting a TEM program? Before you can manage your exposure, you have to see it all. The most critical first step is getting a complete and continuous inventory of your entire attack surface. This means discovering every single asset connected to your organization, from servers and laptops to cloud instances, web apps, and IoT devices. Without this comprehensive visibility, you’ll always have blind spots where threats can hide. A solid TEM program is built on this foundation of total visibility.
How does a TEM platform work with the security tools we already have? A TEM platform shouldn’t operate in a silo; it should be the central hub that connects your security stack. It’s designed to integrate smoothly with the tools you already use, like your SIEM, EDR, and ticketing systems. By sharing data across these platforms, it creates a single, unified view of your security posture and helps automate your response workflows. This ensures everyone is working from the same information and eliminates the gaps that can occur when tools don’t communicate.