Comprehensive Threat Exposure Management Platform
You can’t protect what you don’t know you have. In an environment of sprawling cloud instances, remote endpoints, and shadow IT, gaining a complete and accurate picture of your attack surface is a massive challenge. Periodic scans only provide a snapshot in time, missing assets that spin up and down between assessments. This visibility gap is where attackers thrive. To close it, you need a living, breathing map of your entire digital footprint. A platform for continuous exposure assessment provides this foundational visibility by continuously discovering and cataloging every asset across your hybrid environment, ensuring your security efforts are built on a complete and accurate foundation.
If you feel like you’re constantly playing catch-up with an endless list of vulnerabilities, you’re not alone. A Continuous Exposure Assessment Platform is designed to shift your security posture from reactive to proactive. Think of it as a central hub that doesn’t just find security weaknesses but helps you understand them from an attacker’s point of view. It continuously scans your entire digital footprint—from your cloud environments to your on-premise servers—to identify and prioritize the security gaps that pose a real threat to your business.
Instead of just handing you a list of problems, these platforms provide the context you need to fix what matters most. They connect the dots between a single vulnerability, a misconfigured asset, and a potential attack path, giving you a clear, unified view of your cyber risk. This approach helps you move beyond simply managing vulnerabilities and start actively reducing your exposure to threats with a comprehensive exposure management platform.
At its heart, a continuous exposure assessment platform operates on a simple but powerful cycle. First comes Discovery. The platform continuously scans your environment to map out your entire attack surface, identifying every asset you own, whether you knew about it or not. Next is Prioritization. Instead of treating all vulnerabilities equally, the platform uses real-time threat intelligence and business context to determine which exposures are most likely to be exploited. Finally, there’s Mobilization, which involves guiding your team on how to fix the most critical issues first, ensuring your remediation efforts have the greatest impact.
For your team, this means a significant shift in daily operations. Instead of sifting through thousands of low-risk alerts, your team can focus its energy on the handful of exposures that represent genuine danger. A platform like this provides a consolidated view of high-risk vulnerabilities, showing you exactly how an attacker could chain them together to breach your defenses. This allows you to validate your security controls against real-world attack scenarios. It’s about moving away from a compliance-driven checklist and toward a proactive strategy that addresses actual, exploitable weaknesses before they can be used against you.
Traditional vulnerability management often leaves you with a massive, unmanageable list of CVEs. A continuous exposure assessment platform goes much deeper. It assesses a wider range of issues, including cloud misconfigurations, weak credentials, and risky user permissions—things a standard scanner might miss. It enriches this data with crucial business context, like which assets are critical to your operations, and insights from threat intelligence labs like HiveForce Labs. This holistic approach helps you with vulnerability and threat prioritization based on potential business impact, not just a technical severity score, transforming your security program from a guessing game into a confident, strategic operation.
Adopting a new security framework can feel like a massive undertaking. You know you need to move from a reactive, fire-fighting mode to a proactive stance, but getting there is filled with potential roadblocks. Your teams are already stretched thin, your tech stack is a complex web of tools that don’t always play nice, and getting a complete picture of your environment feels like a moving target. These are not just your problems; they are common challenges that many organizations face when trying to mature their security programs. The reality is that modern IT environments are too dynamic and complex for manual processes or siloed tools to keep up. This is where the implementation of a new, overarching system can seem daunting.
A continuous exposure management platform is designed to address these very issues head-on. It acts as a central nervous system for your security operations, connecting disparate data points, workflows, and teams. Instead of adding another layer of complexity, it simplifies your entire security posture by providing a single source of truth. By automating asset discovery, integrating with your existing tools, and providing clear, actionable priorities, the platform removes the friction that stalls so many security initiatives. This allows you to move past the implementation hurdles and focus on what truly matters: understanding and reducing your organization’s exposure to threats. Let’s break down how it helps you solve some of the most persistent challenges.
You can’t protect what you don’t know you have. In today’s sprawling digital estates—spanning on-prem servers, cloud instances, IoT devices, and web applications—gaining a complete and accurate asset inventory is the first major hurdle. Without this foundational visibility, your security efforts are based on guesswork. A continuous exposure management platform tackles this by providing total attack surface management. It continuously discovers and catalogs all your assets, giving you a unified view of your entire environment. This isn’t a one-time snapshot; it’s a living, breathing map of your attack surface that updates as your infrastructure changes. This comprehensive visibility is the bedrock of any effective security program.
Your security team already uses a variety of tools, from vulnerability scanners to configuration management databases. The problem is that these tools often operate in silos, creating fragmented data and inefficient workflows. A strong exposure management platform acts as a connective tissue, integrating with your existing security and IT ecosystem. It pulls data from all these disparate sources and normalizes it, creating a single, coherent view of your risk posture. This allows you to implement standardized risk scoring and add crucial business context, which is essential for effective vulnerability and threat prioritization. Instead of juggling multiple dashboards, your team can work from one unified platform, making their efforts more streamlined and impactful.
Most security teams are fighting an uphill battle with limited resources and an overwhelming number of alerts. The sheer volume of vulnerabilities can lead to alert fatigue and burnout, making it impossible to address everything. This is where intelligent prioritization becomes a game-changer. By integrating real-time threat intelligence and automation, a platform like Uni5 Xposure helps you cut through the noise. It automatically identifies which vulnerabilities are actively being exploited or pose the greatest risk to your critical assets. This allows your team to focus their time and energy on the exposures that matter most, streamlining remediation efforts and drastically reducing manual workloads. It’s about working smarter, not just harder.
Cybersecurity is a team sport, but it’s often played in separate arenas. Security, IT operations, and DevOps teams frequently work in silos, leading to miscommunication and slow remediation cycles. An exposure management platform breaks down these barriers by creating a shared space for collaboration. When everyone is looking at the same data, dashboards, and risk priorities, conversations become much more productive. Security can provide IT with clear, context-rich reports that explain why a patch is critical, while DevOps can see how their code impacts the organization’s overall risk posture. This shared understanding fosters a culture of collective ownership and ensures that everyone is working together toward the common goal of reducing exposure.
So, how does a continuous exposure assessment platform actually function? Think of it as a four-part cycle that runs on a constant loop, keeping your security posture sharp and responsive. It’s not about running a scan, getting a report, and calling it a day. Instead, it’s a dynamic process designed to keep pace with your ever-changing digital environment. This approach moves your team from a reactive state—scrambling to patch vulnerabilities after they’re discovered—to a proactive one where you can anticipate and neutralize threats before they become real problems.
The cycle begins with discovery, where the platform maps out your entire digital footprint. Next, it collects and consolidates data from all your security tools to create a single, unified view of your risk landscape. With this complete picture, the platform then prioritizes exposures, using real-world threat intelligence to pinpoint which issues pose the most immediate danger to your business. Finally, it helps automate the response, streamlining remediation workflows and ensuring accountability. This continuous loop—discover, collect, prioritize, and automate—is the engine that powers a modern, effective exposure management program, all managed through a central hub like the Uni5 Xposure Platform.
You can’t protect what you don’t know you have. The first step in continuous exposure assessment is creating a complete and constantly updated inventory of all your digital assets. This goes far beyond a simple list of servers and laptops. A modern platform provides total attack surface management by identifying everything connected to your network—from on-premise hardware and cloud instances to IoT devices, mobile endpoints, and third-party services. Because your environment is always changing, with new assets coming online and old ones being decommissioned, this discovery process can’t be a one-time event. It has to be continuous, giving you a real-time map of your entire digital footprint as it evolves.
Once you have a clear view of your assets, the next step is to gather all the relevant exposure data associated with them. This means pulling in information from a wide range of sources, not just your vulnerability scanner. A strong exposure assessment platform aggregates data on vulnerabilities, misconfigurations, weak credentials, and policy violations from all your security tools. By consolidating this information, you break down the data silos that often exist between different teams and tools. This creates a single source of truth, providing the rich context needed to understand your true risk posture and make informed decisions about where to focus your efforts.
With a sea of vulnerabilities, how do you know which ones to fix first? This is where intelligent prioritization comes in. Instead of relying solely on generic CVSS scores, a continuous exposure assessment platform uses advanced analytics and real-world threat intelligence to determine which risks are most critical to your organization. It considers factors like whether a vulnerability is actively being exploited in the wild, the business criticality of the affected asset, and the effectiveness of existing security controls. This risk-based approach allows your team’s limited time and resources to focus on the threats that pose the greatest danger, a process guided by insights from threat intelligence teams like HiveForce Labs.
Finding and prioritizing threats is only half the battle; you also have to fix them. The final stage of the cycle is all about streamlining remediation. An exposure assessment platform helps automate your response actions by integrating directly with your existing IT and development workflows. It can automatically create tickets in systems like Jira or ServiceNow, assign them to the correct team members, and provide clear instructions for remediation. This automation not only speeds up the patching process but also ensures accountability and makes it easy to track progress. By performing adversarial exposure validation, you can close the loop and confirm that your actions have effectively reduced exposure.
Choosing the right exposure assessment platform can feel overwhelming, but it boils down to finding a solution that gives you clarity and control. You’re not just looking for another tool that spits out a long list of vulnerabilities. You need a platform that connects the dots between your assets, potential threats, and business context to show you what truly matters. The goal is to move from a reactive cycle of patching and praying to a proactive strategy where you can anticipate and neutralize threats before they cause damage.
A great platform acts as a central hub for your security posture, pulling in data from across your environment to give you a single, unified view of risk. It should help you answer critical questions like, “What are our most exposed assets?” and “Which vulnerabilities are attackers most likely to target right now?” Look for a solution that not only identifies weaknesses but also validates your defenses and streamlines your remediation efforts. This approach helps you focus your team’s limited time and resources on the fixes that will have the biggest impact on reducing your overall risk.
Static vulnerability data is a snapshot in time, but the threat landscape changes by the minute. That’s why your platform must be powered by real-time threat intelligence. This isn’t just about knowing a vulnerability exists; it’s about understanding if it’s being actively exploited in the wild, who is targeting it, and what techniques they’re using. A platform that integrates up-to-the-minute threat advisories can instantly re-prioritize your risks based on emerging campaigns. This context is what separates a theoretical weakness from an immediate, five-alarm fire, allowing your team to focus on the threats that pose a clear and present danger to your organization.
To effectively prioritize, you need to see the full picture. Relying solely on CVSS scores is no longer enough. A modern exposure assessment platform uses advanced analytics and AI to correlate multiple data points for a more accurate risk profile. It should consider the business criticality of an asset, the severity of the vulnerability, and the latest threat intelligence. This intelligent vulnerability and threat prioritization helps you cut through the noise of thousands of alerts. Instead of a flat list of problems, you get a stack-ranked list of actions that are directly tied to protecting your most important business functions.
How do you know if your security tools are actually working as intended? A top-tier platform doesn’t just assume your defenses are effective—it tests them. Through techniques like breach and attack simulation, it can safely mimic real-world attacker behaviors to see how your controls respond. This process of adversarial exposure validation helps you identify gaps in your defenses, such as misconfigured firewalls or ineffective endpoint protection, before an actual attacker can exploit them. It’s a crucial step for confirming your security investments are delivering real value and ensuring your protective layers are truly protecting you.
Your exposure assessment platform shouldn’t be another isolated data silo. To be truly effective, it must integrate smoothly with the tools your team already uses every day. Look for a platform with a robust API and pre-built integrations for your scanners, asset inventories, ticketing systems, and security orchestration tools. When your exposure management platform can communicate seamlessly with your entire security ecosystem, you can automate workflows, enrich data, and accelerate remediation. This creates a more efficient and cohesive security operation, freeing your team from manual data entry and allowing them to focus on strategic risk reduction.
Communicating risk effectively is just as important as finding it. Your platform needs to translate complex technical data into clear, concise reports that resonate with different audiences. Your security operations team needs granular details to execute remediation, while your CISO and the board need high-level dashboards that frame risk in terms of business impact. The ability to create customizable reports is essential for demonstrating progress, justifying security investments, and fostering a shared understanding of the organization’s security posture across all departments. This ensures everyone, from the analyst to the executive, is on the same page.
When new approaches to security emerge, so do the misconceptions. It’s easy to get tangled in assumptions about what it takes to adopt a modern security platform. Let’s clear the air and look at some of the most common myths surrounding continuous exposure assessment—and find out what’s really true.
The thought of implementing a new platform can bring to mind endless meetings, complex configurations, and major disruptions. Many teams worry that adopting a continuous exposure assessment tool will be an overwhelming project. The reality is that modern platforms are designed to be user-friendly and integrate smoothly with your existing security stack. Instead of a complete overhaul, think of it as a powerful addition. A good platform will connect with the tools you already use, pulling data together to give you a unified view of your risks without forcing you to start from scratch. The goal is to simplify your security operations, not make them more complicated.
Another common concern is that you need a huge team and an even bigger budget to manage an exposure assessment program. This simply isn’t the case. These platforms are built to make your existing team more effective, not to create more work. By automating asset discovery, risk analysis, and reporting, they handle the heavy lifting so your team can focus on strategic remediation. You can start with a focused implementation and expand your efforts over time as you get more comfortable. The right platform acts as a force multiplier, allowing even smaller teams to manage their attack surface proactively and efficiently.
There’s a persistent belief that advanced security solutions are only for large corporations with unlimited resources. But cyber threats don’t care about the size of your company, and your security posture shouldn’t be limited by it either. Exposure assessment platforms offer scalable solutions that can be tailored to fit different operational sizes and budgets. Whether you’re a growing mid-sized company or a global enterprise, understanding your exposure is critical. These platforms provide valuable insights for organizations of all sizes, helping you prioritize threats and protect your most important assets.
Some people confuse continuous exposure management with traditional, periodic vulnerability scanning. They think once the platform is up and running, the job is done. In reality, the “continuous” part is key. Your digital environment is constantly changing, with new assets coming online and new threats emerging daily. An effective exposure management program requires ongoing monitoring, evaluation, and adaptation. The Uni5 Xposure platform is designed for this dynamic reality, providing a constant feedback loop that helps you stay ahead of attackers and respond to evolving risks in real time.
Choosing a great exposure assessment platform is a fantastic first step, but the real value comes from how you integrate it into your security program. Simply plugging it in and hoping for the best won’t get you the results you need. To truly transform your approach from reactive to proactive, you need a thoughtful implementation plan. It’s about creating a solid foundation that aligns your technology, processes, and people to work in harmony.
Think of it like this: you’ve just bought a professional-grade kitchen, but you won’t become a master chef overnight. You need to organize your tools, learn the new equipment, and establish a workflow that makes sense for creating incredible meals. The same principle applies here. A powerful platform is just a tool until you build effective processes around it. By focusing on a few key areas from the start—like standardizing how you measure risk, bringing your teams together, automating workflows, and committing to continuous monitoring—you can ensure your platform delivers on its promise. This approach helps your team work smarter, not harder, to reduce your organization’s exposure and build a more resilient security posture.
If your security, IT, and development teams are all using different ways to measure risk, you’re not speaking the same language. This leads to confusion and disagreement about what to fix first. To effectively prioritize, you need a tool that standardizes risk scoring across your entire environment. A unified platform brings data from all your different scanners and tools into one place and applies a consistent scoring methodology. This ensures everyone, from the SOC analyst to the CISO, is looking at the same picture of risk. The best platforms go a step further by allowing you to add business context, helping you understand which vulnerabilities pose a real threat to your most critical assets. This is how you move from a long list of vulnerabilities to a short, actionable list of prioritized threats.
Cybersecurity isn’t just a job for the security team; it’s a shared responsibility. An effective exposure management program involves “cross-functional teams including security, IT, operations, and business stakeholders,” according to experts at Splunk. When you bring these teams together on a single platform, you break down the silos that slow down remediation. IT and DevOps teams get the context they need to understand why a patch is critical, while security gets visibility into the remediation process. This collaborative approach fosters a culture of shared ownership, ensuring that everyone is working toward the common goal of reducing risk. A unified platform like Uni5 Xposure acts as that central hub where everyone can see the same data and coordinate their efforts seamlessly.
Are your teams still bogged down with manual processes, like creating tickets in spreadsheets or chasing down owners via email? These outdated methods are slow, error-prone, and simply can’t keep up with the modern threat landscape. This is where automation becomes your best friend. Modern exposure management platforms are designed to “automate remediation workflows, assign ownership based on hierarchy, and integrate with IT ticketing systems,” as noted by Nucleus Security. By automating these routine tasks, you can dramatically speed up your response times, reduce the manual burden on your team, and ensure that critical vulnerabilities are never overlooked. This frees up your security professionals to focus on more strategic initiatives, like threat hunting and improving your overall security posture.
The days of running a quarterly vulnerability scan and calling it a day are long gone. Your attack surface is constantly changing, with new assets coming online and new threats emerging daily. That’s why a continuous monitoring strategy is non-negotiable. Your platform should be the engine for this strategy, constantly scanning your environment to provide a real-time view of your exposure. By “integrating real-time risk assessment, threat intelligence, and automation,” these platforms help security teams focus on the exposures that matter most, according to Seemplicity. This ongoing vigilance is the core of a proactive security program, allowing you to discover and address weaknesses before attackers can exploit them. It’s a fundamental part of total attack surface management and the key to staying ahead of threats.
Putting a powerful exposure assessment platform in place is a huge step, but the technology itself is only half the equation. To truly get ahead of threats, you need to build a structured program around it. This means creating a repeatable, strategic process that turns data into action and transforms your security posture from reactive to proactive. An effective program doesn’t just find vulnerabilities; it creates a clear, organization-wide approach to managing and reducing risk.
Think of it as the operational blueprint for your security efforts. It’s what connects your tools, your teams, and your business goals into a single, cohesive strategy. This program ensures that everyone understands their role, that priorities are based on real-world risk, and that your progress is measurable. By focusing on a few key areas—building a solid framework, taking a risk-based approach, defining your metrics, and planning for the future—you can create a sustainable exposure management program that scales with your organization and adapts to the ever-changing threat landscape. This is how you move from simply managing vulnerabilities to truly managing exposure with the help of a platform like Uni5 Xposure.
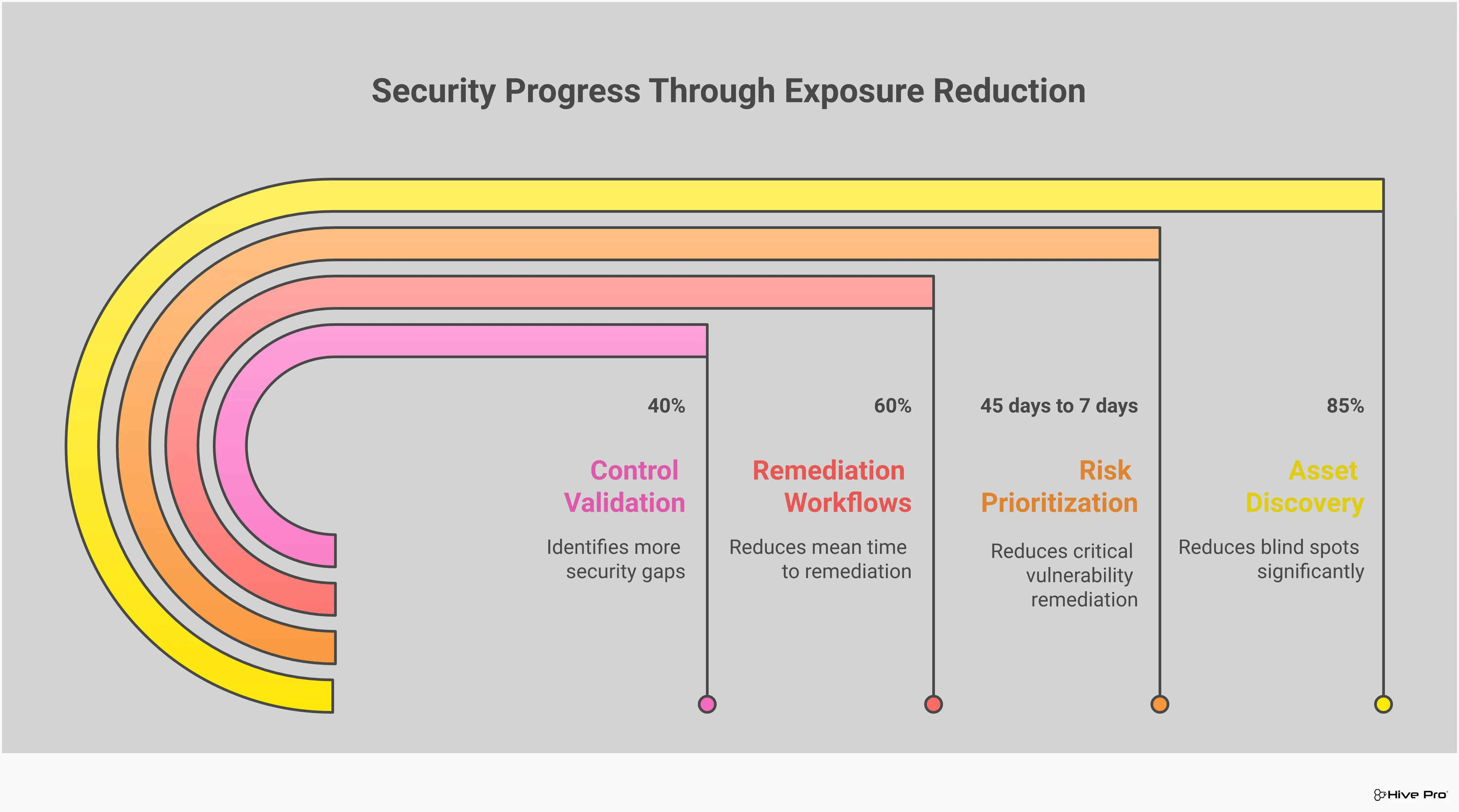
Your first step is to establish a solid framework. This isn’t just a checklist; it’s a comprehensive plan that outlines how you’ll identify, analyze, and manage exposures across your entire digital environment. A strong framework combines the right technologies—like vulnerability scanners, application security tools, and attack surface management—with clear operational processes. It defines how your teams will work together to understand the data and take the necessary steps for remediation. By creating this structure, you ensure that your total attack surface management is consistent, thorough, and aligned with your security goals from day one.
Instead of trying to fix every single vulnerability, a risk-based approach helps you focus on what matters most. This means prioritizing exposures based on their potential impact on your business and the likelihood of exploitation. By integrating continuous monitoring, environmental context, and real-world threat intelligence, you can shift from a reactive cycle of patching to a proactive strategy. This intelligence-driven approach allows your team to direct their time and resources toward the threats that pose a genuine danger, making your vulnerability and threat prioritization efforts far more effective and efficient.
You can’t improve what you don’t measure. Defining clear key performance metrics (KPMs) is essential for tracking the success of your exposure management program and demonstrating its value to leadership. These metrics should go beyond simple vulnerability counts. Focus on outcomes that reflect a genuine reduction in risk, such as the mean time to remediate critical vulnerabilities, the percentage of exploitable exposures, or the reduction in critical attack paths. To do this effectively, you need standardized risk scoring that incorporates business context and is backed by up-to-date intelligence from sources like HiveForce Labs.
The threat landscape is constantly changing, and your exposure management program must be built to adapt. Planning for its evolution means treating it as a living initiative, not a one-time project. This involves creating a feedback loop for continuous improvement and fostering collaboration across different departments. Your security, IT, and operations teams should work together to refine processes and ensure the program stays aligned with business objectives. A successful program is one that can grow and adjust, ensuring your organization remains resilient against emerging threats and new technologies over the long term.
The world of exposure assessment is moving fast, shifting away from periodic scans and reactive fixes toward a more dynamic, continuous approach. The goal is no longer just to find vulnerabilities but to understand and manage your entire attack surface in real time. This evolution is driven by new technologies that help security teams get ahead of threats instead of just chasing them. The future is about building a proactive security posture that can adapt as quickly as the threat landscape changes.
This means integrating different security tools into a single, cohesive platform that gives you a complete picture of your risk. Instead of juggling data from multiple sources, you get a unified view that makes it easier to see what truly matters. The focus is on smart automation and intelligent prioritization, allowing your team to spend less time on manual tasks and more time on strategic initiatives. It’s about transforming your security program from a necessary cost center into a confident, action-oriented function that protects the business where it counts.
Machine learning (ML) is becoming a game-changer for exposure management. With the sheer volume of assets and alerts security teams face, it’s impossible to manually sift through everything. ML algorithms can analyze massive datasets to identify patterns, predict potential threats, and automate routine tasks. This technology helps platforms automate remediation workflows by assigning ticket ownership and integrating directly with your IT systems. This means risks can be addressed more efficiently and at a scale that just wasn’t possible before. By handling the heavy lifting, ML frees up your team to focus on the complex threats that require human expertise and critical thinking.
If machine learning is about making sense of the present, predictive analytics is about anticipating the future. Instead of just reacting to known vulnerabilities, this technology helps you forecast which exposures are most likely to be exploited. By analyzing threat intelligence, historical attack data, and your unique environmental context, predictive models can pinpoint emerging risks before they become active threats. This allows your team to prioritize vulnerabilities that pose the greatest danger, streamlining remediation efforts and significantly reducing your window of exposure. It’s a fundamental shift from a defensive stance to a forward-looking strategy.
The future of exposure assessment lies in creating a truly integrated and proactive security ecosystem. This is the core idea behind Continuous Threat Exposure Management (CTEM), a framework that treats security as a continuous, cyclical process rather than a series of one-off tasks. A modern exposure management program requires a foundational platform that can unify different security technologies into a single source of truth. This integration allows for continuous monitoring, assessment, and validation across your entire attack surface, ensuring you can find and fix your most critical security gaps with confidence.
My team is already swamped with alerts. Won’t this just add more noise? That’s a completely valid concern, and it’s one of the main problems these platforms are designed to solve. Instead of adding to the noise, a continuous exposure assessment platform cuts through it. It uses real-world threat intelligence and understands your business context to prioritize the handful of vulnerabilities that pose a genuine threat. This means your team can stop chasing down thousands of low-risk alerts and focus their energy on the critical issues that attackers are actively exploiting.
How does this kind of platform work with the security tools we already have? It’s designed to be the central hub for your security operations, not another siloed tool. A strong platform integrates with your existing ecosystem—your vulnerability scanners, cloud configuration tools, and asset inventories. It pulls all that disparate data together, normalizes it, and gives you a single, unified view of your risk posture. This actually makes your current tools more valuable by adding the context they need to work together effectively.
What’s the real difference between this and traditional vulnerability management? Traditional vulnerability management often gives you a massive, unmanageable list of technical flaws, ranked by a generic severity score. A continuous exposure assessment platform goes much further. It looks at your entire attack surface, including misconfigurations and weak credentials, and prioritizes issues based on their potential business impact and whether they are actively being targeted by attackers. It’s a strategic shift from just listing problems to actively reducing your exposure to real-world threats.
Is this just about finding problems, or does it actually help us fix them? Finding problems is only the first step. A key function of an exposure assessment platform is to streamline and accelerate remediation. It helps by providing clear, context-rich guidance on what to fix first and why it matters. Many platforms can also automate the response by creating tickets in your IT systems, assigning them to the right teams, and tracking the entire remediation process from discovery to validation, ensuring critical gaps are actually closed.
How can a platform like this help me communicate risk to our leadership team? This is one of its most powerful features. The platform translates complex technical data into clear, business-focused reports and dashboards. Instead of presenting a long list of CVEs, you can show your leadership a prioritized view of risk that highlights the potential impact on critical business assets. This allows you to have more productive conversations about security, justify investments, and demonstrate how your team’s efforts are directly reducing the organization’s overall risk.