Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
In the early era the abilities of a computer to share and transfer information between a client server model across all communication lines gave insights to computer security and Cybersecurity.
During an annual conference held in the late 1960’s which accommodated more security experts and analysts to brainstorm the idea of computer security and how it can be penetrated. Major discussions were held on the lines of penetration in computer security which eventually evolved into the term “Penetration Testing” or famously known as “Pentest”.
The need for Penetration Testing is driven by the fact that resources are shared. In years gone by, this resource-sharing has increased manifold. First came the multi usage single system, then the enterprise networks which linked different departments within an organization. The internet itself is also resource-sharing innovation which increased the data sharing limits even more, and now we are moving into the next era, with the rise of connected devices and the Internet of Things (IoT).
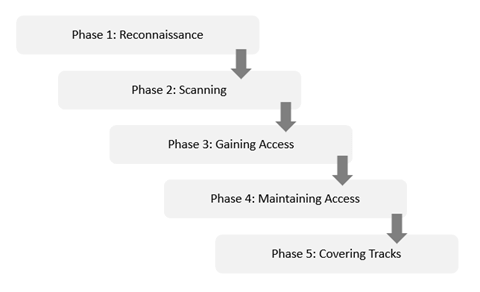
Reconnaissance, scanning, gaining access, maintaining access, covering tracks still remain the fundamental steps of a penetration test, but the process which was looked upon for an asset after the development lifecycle, is now an integral part and sits in every stage of development lifecycle of an asset, be it an application (web/mobile), network infrastructure, Architectural or configurational reviews, penetration tests is now everywhere.
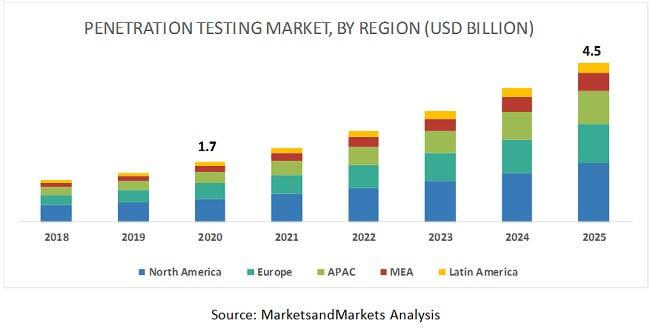
With the increase in the number of cyber incidents, the world is now recognising the importance of a penetration testing activity and its benefits of saving information and money right from the beginning. Looking at the penetration testing market trends, the global penetration testing market size is projected to grow from USD 1.7 billion in 2020 to USD 4.5 billion by 2025, at a Compound Annual Growth Rate (CAGR) of 21.8% from 2020 to 2025 according to markets and research. The major factors driving the market include enterprises implementing security measures due to increased sophistication in cyberattacks. The below projection is further divided by regions.
Author: Bhishm Narula
[sharethis-inline-buttons]