Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
An attacker doesn’t see your company the way you do. They don’t see departments, projects, or business units. They see a collection of potential entry points—a web of digital assets they can probe for a single weakness. Their goal is to find the one unlocked door you forgot about. This is why mapping attack surface for enterprises is so critical. It’s about systematically seeing your organization from an adversary’s perspective. By charting every digital doorway, from cloud storage buckets to third-party software, you can find and close those doors before they do. This guide will show you how to adopt that mindset and build a more resilient defense.
Think of attack surface mapping as creating a complete inventory of every possible entry point an attacker could use to get into your systems. It’s the process of identifying, cataloging, and analyzing all the digital assets your organization owns that are exposed to the internet. This isn’t just about servers and websites; it’s about finding every single digital doorway—from forgotten subdomains and old APIs to employee laptops and cloud storage buckets. The goal is to see your organization from an attacker’s perspective so you can find and fix weaknesses before they do.
A comprehensive map gives you a clear, unified view of your security posture. Without it, you’re essentially flying blind, trying to defend a perimeter you can’t fully see. By systematically charting out these points of exposure, you can move from a reactive stance—patching vulnerabilities as they’re discovered—to a proactive one. This approach helps you build a complete picture of your total attack surface and manage it effectively. It’s the foundational step in understanding where you’re vulnerable and how to direct your security efforts for the biggest impact.
The enterprise attack surface is the sum of all your organization’s digital assets that are accessible either internally or externally. In today’s complex IT environments, this goes far beyond the traditional on-premise network. It includes everything from your cloud infrastructure and SaaS applications to IoT devices, mobile endpoints used by remote employees, and even the operational technology on a factory floor. It’s a sprawling, dynamic collection of hardware, software, and data that constantly changes as your business evolves. Understanding this entire landscape is the first step toward securing it.
Simply put, you can’t protect what you don’t know you have. Mapping your attack surface is critical because it reveals all your digital assets, including the hidden, forgotten, or unsanctioned ones often referred to as “shadow IT.” This visibility is crucial for preventing breaches. When you understand your full exposure, you can find weaknesses, prioritize security efforts on the most critical assets, and significantly reduce the likelihood of a successful attack or data leak. This process turns abstract risk into a tangible list of items you can act on, allowing for effective vulnerability and threat prioritization.
Your attack surface can be broken down into a few key categories. The digital attack surface is the most obvious, including everything from your websites and web applications to APIs and cloud services. But you also have to consider physical entry points, like unsecured servers or employee devices that could be stolen. Finally, there’s the human element—your employees—who can be targeted through social engineering tactics like phishing. Each of these areas contains potential vectors that attackers can exploit, making it essential to perform adversarial exposure validation across all of them.
To effectively map your attack surface, you first need to understand what it includes. It’s not just about your servers and websites; it’s every single point where an attacker could potentially get in. Think of it as the sum of all your risks. A comprehensive view means looking beyond the purely digital and considering the physical, human, and third-party elements that create your organization’s unique exposure profile. Breaking it down helps you see the full picture and ensures no entry point is left unchecked.
Your digital attack surface is what most people think of first: all the internet-facing hardware and software assets that an attacker could target. This includes everything from your corporate website and web applications to APIs, cloud servers, and employee laptops. Essentially, if it has an IP address and is connected to your network, it’s part of your digital footprint. The goal of attack surface mapping is to identify and monitor these assets continuously. Unmanaged or forgotten assets, often called shadow IT, can create significant blind spots, making a complete and current inventory your first line of defense.
Your attack surface extends into the real world. The physical attack surface covers all the tangible access points and vulnerabilities in your organization’s environment. This goes beyond just building access control. It includes unsecured server rooms, improperly disposed-of hardware containing sensitive data, and even the risk of an unauthorized person tailgating an employee through a secure door. A strong security posture requires evaluating how you protect your physical spaces and assets, as a breach here can give an attacker direct access to your internal network, bypassing many digital defenses entirely.
People are a critical part of your attack surface. Social engineering is how attackers exploit human psychology to trick people into divulging confidential information or performing actions that compromise security. This isn’t about complex hacking; it’s about manipulation. Phishing emails that convince an employee to click a malicious link or a phone call where an attacker impersonates an IT support tech are classic examples. Your social engineering attack surface is defined by how susceptible your team is to these tactics, making ongoing security awareness training an essential part of reducing this risk.
As more organizations move to the cloud, the cloud environment has become a major component of the modern attack surface. Your cloud attack surface includes everything you run in services like AWS, Azure, or Google Cloud. This means APIs, third-party applications integrated into your cloud stack, storage buckets, databases, and every user account with access. The ease and scalability of the cloud can also lead to misconfigurations and overlooked vulnerabilities. Understanding these components is crucial, as a single poorly configured storage bucket or an over-privileged user account can expose massive amounts of sensitive data.
Your organization doesn’t operate in a vacuum. Your attack surface includes the risks introduced by your vendors, partners, and software supply chain. Every time you integrate a third-party application or grant a vendor access to your systems, you are extending your security perimeter to include theirs. If a vendor has poor security practices, they can become an entry point into your network. That’s why it’s so important to vet your vendors and continuously monitor these connections. You need to know who has access to your data and ensure they are protecting it as carefully as you do.
Mapping your attack surface can feel like a huge undertaking, but breaking it down into manageable steps makes it much more approachable. Think of it as creating a detailed map of your digital kingdom—first, you identify the borders, then you find the weak spots in the walls, and finally, you decide which ones to reinforce first. This five-step process will guide you from discovery to remediation, helping you build a clear and actionable security plan. It’s all about moving from a reactive stance to a proactive one, where you’re in control of your security posture. Let’s walk through it together.
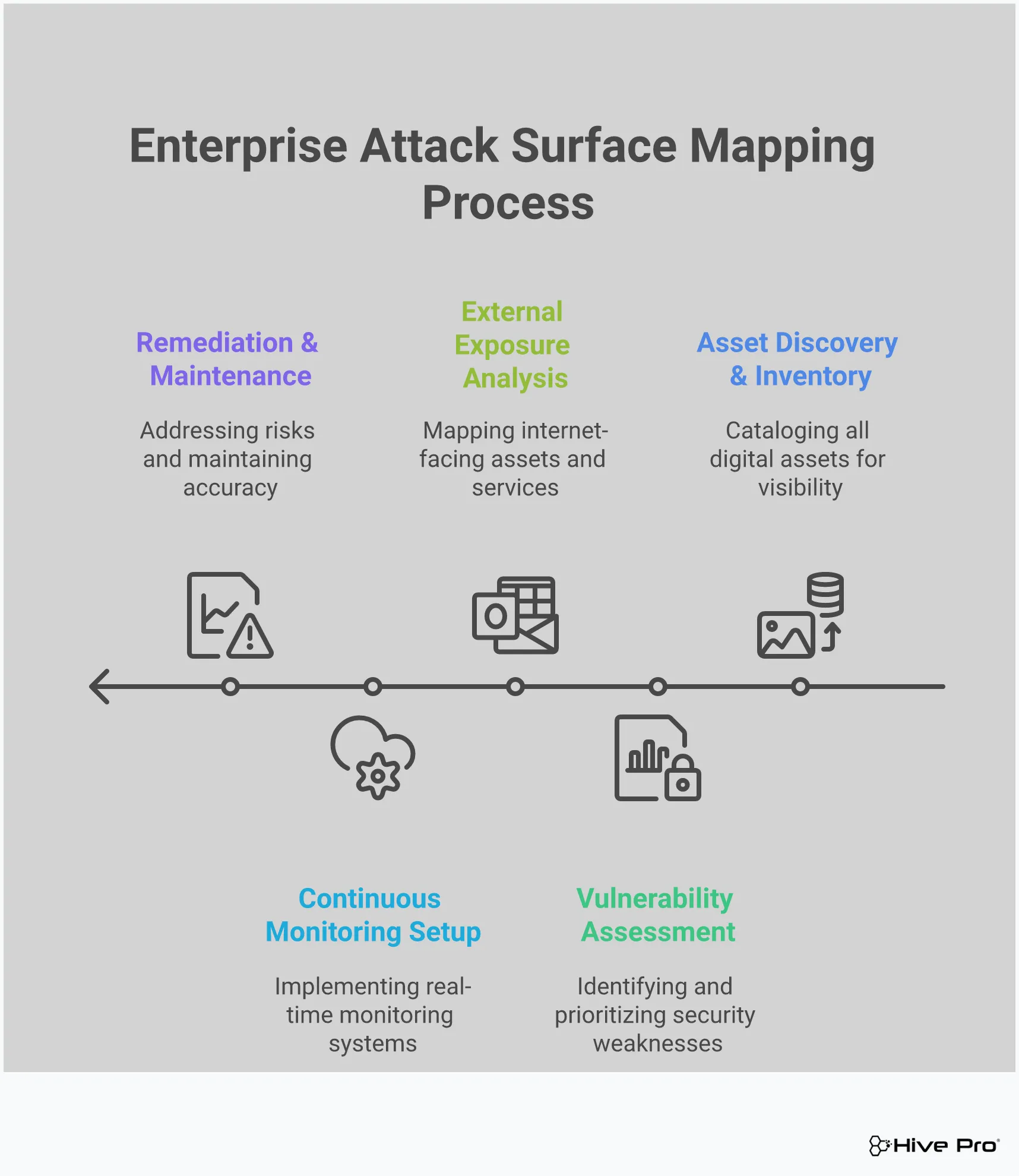
You can’t protect what you don’t know you have. The first step is a comprehensive discovery process to identify every single asset connected to your organization. This includes everything from known servers, applications, and cloud instances to forgotten subdomains and shadow IT. The goal is to create a complete inventory of all your external-facing assets. This foundational map is crucial for understanding what needs protection and how each component interacts with potential threats. A thorough Total Attack Surface Management strategy begins with this complete visibility, ensuring no stone is left unturned and no asset is left exposed.
Once you have a complete inventory of your assets, it’s time to inspect them for weaknesses. This step involves scanning each asset for known vulnerabilities, misconfigurations, and other security gaps that an attacker could exploit. By proactively finding these weaknesses before an attacker does, you can shift your security posture from reactive to preventative. This assessment helps you understand the specific risks associated with each part of your attack surface. It’s not just about finding flaws; it’s about understanding the context of those flaws and how they could be used in an attack, which is a key part of effective vulnerability and threat prioritization.
Not all vulnerabilities carry the same weight. A minor flaw on a non-critical system is less urgent than an unprotected database filled with sensitive customer data. This is where classification and risk scoring come in. By analyzing factors like asset criticality, vulnerability severity, and existing security controls, you can prioritize which issues to tackle first. This process helps your team focus its time and resources on the most critical problems, allowing for a much more efficient remediation process. Instead of getting lost in a sea of low-level alerts, you can direct your efforts where they’ll have the greatest impact on your security.
Your digital footprint is constantly changing. New systems are deployed, applications are updated, and cloud environments scale up and down. Because your attack surface is dynamic, a one-time assessment is never enough. You need to establish continuous monitoring to stay ahead of new threats and changes in your environment. This means implementing tools and processes that constantly scan for new assets and vulnerabilities. A Continuous Threat Exposure Management (CTEM) platform automates this process, providing real-time visibility and ensuring you’re always aware of your current exposure level, not just the one from last quarter’s scan.
Discovery and prioritization are only half the battle; the final step is taking action. Based on your risk scoring, create a clear and structured remediation plan. This plan should outline who is responsible for fixing each vulnerability, the timeline for remediation, and the steps required to verify the fix. It’s also about building good security hygiene, like regularly updating software, reviewing access rules, and watching for new threats. A well-defined remediation plan turns your mapping efforts into tangible security improvements, ensuring that identified risks are actually resolved and your organization becomes more resilient over time.
Manually mapping your attack surface is like trying to chart the ocean in a rowboat—it’s just not feasible. You need the right technology to get a clear, comprehensive picture of your assets and exposures. The right tools don’t just find assets; they help you understand the context, prioritize risks, and see how everything connects. While you can assemble a stack of individual solutions, many teams find it more effective to use a unified platform that brings these capabilities together.
A comprehensive Threat Exposure Management Platform can integrate data from various sources, giving you a single source of truth for your entire attack surface. This approach eliminates the silos that often form between different security tools, providing a more holistic view of your risk landscape. Instead of juggling multiple dashboards, your team can work from one unified interface to discover assets, prioritize vulnerabilities, and validate security controls. This streamlines your workflow and helps you move from simply managing vulnerabilities to proactively reducing your overall exposure. Let’s look at some of the core tool categories that make this possible.
Think of network scanning tools as your first line of reconnaissance. They are essential for identifying every active device connected to your network, from servers and laptops to printers and IoT devices. These tools help you build a foundational map of your network topology, showing you exactly what’s online and how it’s configured.
More importantly, they are critical for spotting unauthorized or rogue devices that could introduce significant security risks. By regularly scanning your network, you can maintain an accurate inventory and ensure that every connected device is accounted for and properly secured. This visibility is the starting point for any effective attack surface management program.
Once you know what assets you have, the next step is to find their weaknesses. Vulnerability assessment platforms play a critical role here by continuously scanning your systems and software for known vulnerabilities. These platforms check your assets against massive databases of common vulnerabilities and exposures (CVEs), giving you a detailed report of your security posture.
The real value, however, comes from prioritization. A good platform doesn’t just give you a long list of flaws; it helps you understand which ones pose the greatest threat to your organization. By providing context and risk-based scoring, these tools allow you to focus your remediation efforts on the issues that matter most, a core principle of effective vulnerability and threat prioritization.
As more assets move to the cloud, your attack surface expands into environments you don’t physically control. Cloud security solutions are specifically designed to protect these cloud-based assets and applications. They continuously monitor your cloud environments—whether AWS, Azure, or Google Cloud—for misconfigurations, compliance gaps, and potential vulnerabilities.
These tools are vital for minimizing your cloud attack surface, as simple misconfigurations are a leading cause of cloud data breaches. By providing deep visibility into your cloud infrastructure, they help you enforce security policies and ensure your data remains protected. This specialized focus is crucial for any organization with a significant cloud presence.
Your digital environment is constantly changing. New devices come online, software is updated, and cloud instances are spun up and down. Automated discovery tools are crucial for keeping up with this dynamic landscape. They work around the clock to continuously identify and catalog all your digital assets, from on-premise hardware to cloud services and web applications.
This continuous process ensures you always have an up-to-date inventory, which is the bedrock of effective attack surface management. Without a complete and current asset list, you’re operating with blind spots where threats can easily hide. Automation removes the manual effort and human error from asset inventory, giving you a reliable foundation for your security program.
Knowing your vulnerabilities is one thing; knowing which ones are actively being exploited by attackers is another. Threat intelligence feeds provide real-time information about emerging threats, new attack techniques, and active campaigns. This intelligence adds a critical layer of context to your vulnerability data.
By integrating threat intelligence from sources like HiveForce Labs, you can see which of your vulnerabilities are tied to active threats in the wild. This allows you to prioritize remediation based not just on a technical severity score, but on the actual, immediate risk to your business. It’s the key to moving from a reactive stance to a proactive one, where you can address potential risks before they become incidents.
Mapping your attack surface isn’t a one-and-done project; it’s an ongoing process filled with moving parts. Many security teams run into the same hurdles, from assets that appear and disappear in minutes to the hidden risks of shadow IT. The good news is that these challenges are manageable. With the right approach and tools, you can move from feeling overwhelmed by the complexity to being in control of your security posture. Let’s walk through some of the most common obstacles and how you can clear them.
Modern IT infrastructures are anything but static. Cloud systems, virtual machines, and containers are constantly being created, modified, and decommissioned, which makes keeping an accurate map a real challenge. A quarterly scan just won’t cut it anymore. The key is to shift from periodic snapshots to continuous visibility. By implementing tools that offer Total Attack Surface Management, you can automate the discovery process. This ensures your map is always up-to-date, reflecting the true state of your environment in real time. This approach allows you to spot new assets and potential exposures the moment they appear, closing the gap between discovery and defense.
The cloud offers incredible flexibility, but it also introduces layers of complexity that can obscure your true attack surface. Between multi-cloud setups, microservices, and containerized applications, it’s easy to lose track of how everything connects and where vulnerabilities might hide. To get a clear picture, you need tools designed specifically for the cloud. These solutions can parse complex configurations and dependencies, helping you understand the relationships between different cloud assets. A strong cloud security strategy involves using platforms that can consolidate data from all your cloud providers into a single, unified view, making it much easier to spot misconfigurations and potential attack paths.
One of the biggest mapping challenges comes from assets you don’t even know you have. Shadow IT—when employees use unauthorized software, devices, or cloud services—creates dangerous blind spots. These unmanaged assets aren’t patched, monitored, or configured correctly, making them easy entry points for attackers. Tackling this requires a combination of policy and technology. Start by establishing clear guidelines for approved tools and services. Then, use a discovery tool that can continuously scan your networks and cloud environments for unauthorized assets. This proactive approach helps you find and manage shadow IT before it can be exploited.
Your organization’s security perimeter doesn’t end with your own assets. It extends to every third-party vendor, partner, and software supplier you work with. A vulnerability in a partner’s system can quickly become your problem. That’s why a thorough third-party risk management program is essential. You need to vet vendors before bringing them on board and continuously monitor their security posture. This includes understanding what data they have access to and ensuring they meet your security standards. By making third-party risk assessments a standard part of your process, you can effectively manage the risks introduced by your supply chain.
Let’s be honest: most security teams are stretched thin. There often isn’t enough time, budget, or specialized staff to manually map and manage an ever-expanding attack surface. This is where automation and intelligent prioritization become your best allies. Instead of trying to fix everything at once, focus on the exposures that pose the greatest threat to your business. A modern platform like Uni5 Xposure automates the heavy lifting of discovery and analysis. It helps you prioritize vulnerabilities based on real-world threat intelligence, allowing your team to direct its limited resources toward the issues that matter most and operate more efficiently.
Mapping your attack surface is a huge step, but it’s really just the beginning. The map shows you the terrain; now you have to secure it. Effective management turns that static picture into a dynamic, proactive security strategy. It’s about creating a sustainable program that not only identifies exposures but also prioritizes and remediates them before they can be exploited. This means moving beyond one-off assessments and building a continuous cycle of discovery, validation, and response.
Adopting a few core best practices can make all the difference between feeling overwhelmed by a long list of vulnerabilities and confidently taking action. It’s about working smarter, not just harder. By setting clear goals, you ensure your efforts are focused on what matters most to the business. By validating your controls, you make sure your defenses are actually working as intended. And by fostering collaboration, you get a more complete and accurate picture of your risk. These practices help transform your total attack surface management from a reactive chore into a proactive, strategic function that strengthens your entire security posture. Let’s walk through five key practices that will help you build a resilient and effective program.
Before you dive into remediation, take a step back and define what success looks like. You can’t protect everything equally, so you need to know what your most critical assets are. Are you focused on protecting sensitive customer data, ensuring the uptime of a key application, or securing intellectual property? Setting clear goals helps you align your security efforts with broader business objectives. This clarity ensures you’re not just chasing down every minor vulnerability but are strategically reducing the risks that pose the greatest threat to your organization. As experts at CyCognito note, it’s essential to “know exactly what you want to protect and what areas you will focus on.” This foundational step guides your entire management strategy.
Your attack surface is not static—it changes every time a new device is added, a new application is deployed, or a configuration is updated. That’s why your security controls need constant attention. It’s not enough to set them up and assume they’re working. Regular validation is key to ensuring your defenses are effective against emerging threats. This involves continuously testing your security measures to find gaps and weaknesses. By performing adversarial exposure validation, you can simulate real-world attack scenarios to see how your controls hold up. This ongoing process helps you move from a “set it and forget it” mindset to one of continuous vigilance, ensuring your security posture adapts as quickly as your environment changes.
When you discover a critical vulnerability, what happens next? Without a clear plan, teams can waste precious time figuring out who is responsible and what steps to take. Establishing clear response protocols is essential for acting quickly and effectively. This means prioritizing vulnerabilities based on their potential impact and exploitability, not just their CVSS score. Most organizations have far more weaknesses than they can fix at once, so it’s crucial to focus on the highest-risk ones first. A solid response plan should define roles, outline communication channels, and set clear timelines for remediation. This ensures that when a serious threat appears, your team is ready to act decisively.
Security is a team sport, not a siloed function. Your attack surface spans across IT, DevOps, cloud teams, and various business units, and you can’t get a complete picture without their input. Encouraging collaboration between these departments is vital for comprehensive attack surface management. IT and DevOps teams have deep knowledge of the infrastructure and applications, while business leaders can provide context on which assets are most critical. By working together, you can uncover shadow IT, understand dependencies, and ensure that security measures don’t disrupt essential operations. This collaborative approach, as highlighted by SentinelOne, ensures nothing is missed and fosters a shared sense of ownership over the organization’s security.
The threat landscape is always evolving, and your security practices must evolve with it. Effective attack surface management is not a one-time project but an ongoing commitment to improvement. This means creating a feedback loop where you regularly review your security posture, learn from incidents, and adapt your strategies. Stay informed on new threats by following threat advisories and update your software and security rules accordingly. Regularly reassessing your access controls and security policies ensures they remain effective over time. By embracing a cycle of continuous improvement, you build a resilient security program that can stand up to the challenges of tomorrow, not just the threats of today.
Mapping your attack surface isn’t a one-and-done project. It’s a foundational part of a living, breathing security program. A resilient strategy is one that adapts to your changing environment, leverages modern technology, and grows with your organization. It moves you from a reactive stance—scrambling to patch vulnerabilities as they’re discovered—to a proactive one where you can anticipate and neutralize threats. Building this kind of strategy requires a thoughtful approach that considers not just the technology you use, but also the people and processes that support it. By focusing on evolution, automation, scalability, team skills, and clear metrics, you can create a mapping program that doesn’t just identify risks but actively reduces them over time. This approach ensures your security efforts are sustainable, effective, and aligned with your business goals.
Your business isn’t static, and neither is your attack surface. New assets come online, cloud services are spun up, and code is deployed daily. That’s why your mapping strategy needs to be built for the long haul. Think of it as an ongoing process, not a one-time project. As experts at CyCognito note, “Attack surface mapping is not a one-time project; it’s an ongoing process that helps organizations understand their weaknesses and stop attacks before they happen.” Schedule regular reviews of your mapping strategy to ensure it still meets your needs. As your company grows or adopts new technologies, your approach will need to evolve right along with it. A continuous threat exposure management program is the best way to keep pace.
The sheer scale and dynamic nature of a modern enterprise attack surface make manual mapping impossible. This is where AI and automation become your most valuable allies. These technologies can continuously scan your environment, identify new assets, and analyze potential vulnerabilities far faster and more accurately than any human team could. An advanced attack surface management platform “natively combines AI-powered threat detection with comprehensive visibility into the services and tools within an organization’s digital assets.” By automating the discovery and initial assessment phases, you free up your security team to focus on higher-value tasks like threat analysis, strategic planning, and remediation. This allows you to maintain constant vigilance without burning out your team.
If you’re part of a large organization, trying to map everything at once can be overwhelming. A better approach is to “break down the mapping process into smaller parts, focusing on one business unit or region at a time.” As you do this, make sure the tools and processes you implement are built to scale. Your strategy must account for a complex mix of environments, including multiple cloud providers and on-premise data centers. Look for solutions that provide a unified view across all these disparate systems. A platform that can grow with you will prevent you from having to rip and replace your tools down the line, saving you significant time and resources as your company expands.
Your tools are only as effective as the people who use them. A resilient mapping strategy must include a plan for continuously developing your team’s expertise. The threat landscape is always changing, so it’s crucial to “regularly teach your security team and employees about new threats and how to defend against them.” This means investing in ongoing training, encouraging certifications, and providing access to high-quality threat intelligence. When your team understands the latest attack vectors and mitigation techniques, they can better interpret the data from your mapping tools and make smarter, faster decisions. Keeping them informed with resources like regular threat advisories is a simple way to support their growth.
How do you know if your mapping strategy is working? You need to measure it. Establishing clear key performance indicators (KPIs) is essential for tracking your progress and demonstrating the value of your program to leadership. These aren’t just vanity numbers; they are “the specific metrics used to measure the effectiveness of your organization’s cybersecurity.” Start by tracking metrics like Mean Time to Detect (MTTD) for new assets, Mean Time to Remediate (MTTR) for critical vulnerabilities, and the percentage of your attack surface under active monitoring. These KPIs provide concrete evidence of your program’s impact and help you identify areas for improvement, ensuring your vulnerability prioritization efforts are truly effective.
Once you’ve mastered the basics of identifying and inventorying your assets, it’s time to adopt a more proactive, attacker-centric mindset. Basic mapping tells you what you have, but advanced techniques show you how it could be compromised. This is where you move from simply cataloging your attack surface to actively managing your exposure. By thinking like an adversary, you can uncover hidden risks and strengthen your defenses before they’re ever put to the test.
These advanced methods help you connect the dots between individual vulnerabilities, test your security controls under realistic conditions, and focus your team’s efforts on the threats that truly matter. It’s about shifting from a reactive posture of patching known issues to a strategic approach that anticipates and neutralizes potential attack vectors. Let’s explore four techniques that can help your team make this critical shift and build a more resilient security program.
Simply knowing you have a vulnerability isn’t enough. The real risk often lies in how an attacker could chain multiple, seemingly low-risk weaknesses together to reach a critical asset. Attack path analysis helps you visualize these potential routes. By mapping how an attacker might move laterally across your network, you can understand how they might exploit weaknesses to escalate privileges or access sensitive data. This process turns a flat list of vulnerabilities into a dynamic map of potential breach scenarios, allowing you to sever those paths by fixing the most pivotal choke points first.
How do you know if your security controls will actually work during a real attack? Breach and Attack Simulation (BAS) provides the answer. These platforms safely and continuously simulate real-world attack techniques against your environment. Think of it as automated red teaming. By running these attack simulations and tests, you can find weaknesses in your defenses before an actual attacker does. This goes beyond vulnerability scanning by validating whether your security stack—from firewalls to EDR—is configured correctly and can effectively detect and block threats.
Your team has limited time and resources, so you can’t fix everything at once. Advanced mapping helps you cut through the noise and focus on what matters most. Instead of relying solely on generic CVSS scores, you can use threat intelligence and business context to prioritize exposures. This approach helps your team figure out which problems are the most critical, like an internet-facing database with a known exploit, so you can fix those first. Effective vulnerability and threat prioritization ensures your remediation efforts have the greatest possible impact on reducing your overall risk.
Your security posture is not static. New assets come online, configurations change, and new threats emerge every day. That’s why your security controls require continuous validation. This means you need to regularly check your security, update software, and review access rules to ensure they remain effective. Techniques like BAS can automate much of this process, providing ongoing assurance that your defenses are working as intended. Consistent adversarial exposure validation helps you catch misconfigurations or gaps in coverage before they can be exploited, keeping your defenses aligned with your changing attack surface.
What’s the difference between attack surface mapping and a traditional vulnerability scan? Think of it this way: a vulnerability scan looks for unlocked windows and doors on a building you already know about. Attack surface mapping is the process of creating the complete blueprint of your entire property first, including forgotten sheds, old tunnels, and access points you didn’t even know existed. Mapping is the foundational step of discovery and inventory, while scanning is the subsequent step of checking those inventoried assets for specific weaknesses. You need the complete map before you can effectively find all the vulnerabilities.
How often should we be mapping our attack surface? The most effective approach isn’t to think of mapping as a scheduled event, like a quarterly check-up. Your digital environment changes by the minute, so your map needs to reflect that reality. The goal is to move from periodic snapshots to a continuous, real-time view. This is where automated tools become essential, as they constantly work in the background to discover new assets and changes the moment they happen, ensuring your map is always current.
Our security team is already stretched thin. How can we realistically manage this? This is a very common and valid concern. The key is to lean on automation and intelligent prioritization. A modern threat exposure management platform does the heavy lifting of discovery and analysis for you. Instead of creating more manual work, it helps you focus your limited time on the risks that pose the most immediate threat to your business. The goal isn’t to fix every single flaw but to use technology to pinpoint and address the critical few that truly matter.
What’s the most common blind spot you see when companies start mapping their attack surface? Hands down, the biggest blind spots are shadow IT and third-party dependencies. Teams are often surprised to find cloud services spun up by a marketing team or an old API connected to a former vendor that was never decommissioned. These unmanaged assets and connections aren’t being patched or monitored, making them easy entry points. A thorough mapping process brings these hidden risks out of the shadows so you can finally manage them.
Is attack surface mapping the same as Continuous Threat Exposure Management (CTEM)? They are closely related, but not quite the same thing. Attack surface mapping is a critical component of a CTEM program. CTEM is the complete, cyclical framework that includes discovering your attack surface, prioritizing vulnerabilities, validating your security controls, and guiding remediation. Mapping is the foundational discovery phase within that larger, continuous strategy for proactively reducing your organization’s exposure.