JSON Web Tokens – Attack and Defense
In this blog, we will learn about JSON web tokens and advantages of using them over traditional methods of authorization and authentication. We will delve deeper into the ways a malicious adversary can attack JWT implementations and learn about preventing such pitfalls.
What is JWT?
JSON web tokens (JWT) are JSON objects and are an open standard (RFC 7519). A JSON web token is a standard format that is used to securely transfer information between the two parties.
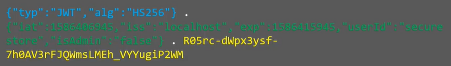
The Structure of JWT (JSON web token) consists of three parts separated by dots(.) and encoded with Base64 algorithm.

- Header: Header contains the information of the token like, which type of token it is, and the type of algorithm used in the token.
- Payload: Payload contains the user identification information for authorization, parameters such as userid, username, role, etc.
- Signature: Signature part contains the information for the resource server to verify the token, it is valid or tampered.
JWT is used to create tokens for authorization requests. Server generates the token for a user and sends it to the client. The client requests data and authorized features to the server using JWT and the server will respond with relevant information after validating the token.
Advantages of using JWT
- Implementing JWT removes the need for cookies and prevents attacks like CSRF and CORS bypasses.
- Session management is easily done as it is self-contained token having the token expiry information.
- It is a more secure way for the authorization as it has digital signature using strong cryptographic algorithms.
Hacking JWT
Though JWT provides many advantages above session cookies, they are vulnerable to misconfiguration based attacks. A JWT is as good as the way it has been implemented. Following attacks could arise due to bad implementation:
- Abusing ‘none’ Algorithm: This method checks for “none algorithm” in the JSON web token, If the token supports “none algorithm” and the signature part is set to none, then any token will be considered as a valid token which could affect access controls. With only header and payload, the attacker can imitate any site using forged tokens. The attacker can add any token to get sensitive information for the admin panel too by crafting the different payload for admin.
- Signature Stripping Attack: This is the common method to attack JSON Web tokens just by removing the signature from the token. Some JWT validations libraries can result in unsigned tokens being taken as valid tokens. In this way, JSON web tokens can be easily tampered, and attackers can send the request to the server using tampered requests. If server does not validated token signatures, the tampered token could lead to critical information from the server
- Brute forcing Secret Key: Brute forcing of the signature is still possible for some small size shared-secrets using the HS256 algorithm, used for signing the token. There is a tool (JWT cracker) for cracking the shared-secret for the HS256 JSON Web token.
Securing JWT Hacks
To make sure implementation based attacks are not possible, following prevention techniques can be used:
- Validating each section of JWT at the server-side.
- Avoid using ‘none’ algorithm type for signature in the token.
- Avoid implementation issues while integrating with third-party libraries.
Author: Sushma Ahuja
