Comprehensive Threat Exposure Management Platform
Knowing you have a vulnerability is one thing; knowing if you’re truly exposed is another. A critical vulnerability might exist on a server, but can an attacker actually reach it? Will your firewall block the attempt? Will your EDR detect the payload? Traditional vulnerability management can’t answer these questions, leaving you patching in the dark. To get real answers, you need to test your defenses against the same tactics attackers use. This is where Breach and Attack Simulation (BAS) comes in, providing a safe way to validate your security controls. When you combine this with real-time threat intelligence, you get the crucial insight Hive Pro provides: a clear, evidence-based picture of your actual risk.
Hive Pro is a cybersecurity company that provides a next-generation Threat Exposure Management Platform. If your security team feels like they’re constantly playing catch-up, buried under a mountain of vulnerability alerts, Hive Pro is designed to change that. Instead of just reacting to issues as they appear, the platform helps you get ahead of attackers by focusing on what truly matters. It provides a unified view of all your cyber risks in a single place, cutting through the noise to highlight the threats that pose an imminent danger to your organization.
The goal is to transform your security program from a reactive, and often overwhelming, cycle of patching into a proactive strategy for reducing your overall exposure. Hive Pro’s approach is straightforward but powerful: it continuously scans your entire attack surface, uses its own in-house intelligence to prioritize threats based on real-world attacker behavior, and then provides a clear, actionable path from discovery to remediation. This shifts your team from guessing what to fix next to taking confident action based on solid intelligence.
At the heart of Hive Pro is the Uni5 Xposure platform. Think of it as your central command center for seeing and managing your organization’s entire threat landscape. The platform helps you discover all the potential weak spots where an attacker might try to get in—from your on-premise servers and cloud assets to your web applications. But it doesn’t just hand you another impossibly long list of problems to solve. Uni5 Xposure intelligently figures out which vulnerabilities are the most dangerous by analyzing real-world threat data. From there, it provides clear, actionable guidance on how to fix them, turning a sea of data into a manageable, prioritized to-do list.
What makes Hive Pro’s prioritization so effective is the intelligence from HiveForce Labs, its dedicated in-house threat and vulnerability research team. This isn’t just generic data pulled from public feeds; it’s predictive and prescriptive analytics designed to proactively neutralize threats. The platform uses this intelligence to identify critical vulnerabilities that are actively being exploited in the wild, helping you reduce your attack surface before attackers have a chance to find those same openings. Having this expert team means you get timely, relevant insights directly integrated into your workflow, giving you a significant advantage in understanding and mitigating the risks that matter most to your business.
Hive Pro helps you make the critical shift from traditional, reactive vulnerability management to a proactive defense posture. Many organizations are stuck on a “patching treadmill,” chasing down vulnerabilities based on generic severity scores—a model known as Risk-Based Vulnerability Management (RBVM). Hive Pro champions a more modern approach called Continuous Threat Exposure Management (CTEM). This is a continuous, adaptive framework that integrates real-time threat detection, intelligent vulnerability and threat prioritization, and streamlined mitigation. It’s about continuously monitoring your environment and making improvements, ensuring you’re always prepared for the next threat instead of just cleaning up after the last one.
So, how does Hive Pro actually help you shift from a reactive to a proactive security posture? It’s all about a continuous, cyclical process powered by the Uni5 Xposure platform. Instead of treating vulnerability management as a series of one-off tasks, Hive Pro implements a complete framework that helps you understand, prioritize, and validate your security efforts from end to end. This structured approach is designed to give you a clear, actionable path to reducing your overall threat exposure. Let’s walk through the key stages of how it operates.
You can’t protect what you don’t know you have. The first step is getting a complete and accurate picture of your entire digital footprint. The Hive Pro platform performs continuous Total Attack Surface Management, discovering and inventorying all your assets, whether they are on-premise, in the cloud, or part of your external-facing infrastructure. This isn’t just a quarterly scan; it’s an ongoing process that identifies new devices, applications, and potential entry points as they appear. By providing a unified view of your assets, it eliminates the blind spots where attackers often find their way in, giving your team a solid foundation for all subsequent security activities.
Once you have a full inventory of your assets and their vulnerabilities, the next question is: what do you fix first? With thousands of potential weaknesses, trying to patch everything is impossible. This is where Hive Pro’s intelligent Vulnerability & Threat Prioritization comes in. Using threat intelligence from its in-house HiveForce Labs, the platform analyzes which vulnerabilities are actively being exploited by attackers in the wild. It enriches this data with business context to pinpoint the exposures that pose the greatest risk to your specific organization. This allows your team to focus its limited time and resources on fixing the critical issues that could actually lead to a breach.
Finding a vulnerability is one thing; knowing if your security controls can stop an attack exploiting it is another. Hive Pro allows you to test your defenses with Adversarial Exposure Validation. This built-in Breach and Attack Simulation (BAS) capability runs safe, controlled attack scenarios against your environment to see how your security stack holds up. It helps you answer critical questions like, “Can our firewall block this threat?” or “Will our EDR detect this type of malware?” By combining exposure assessment with attack simulation in a single platform, you get real-world proof of your security effectiveness and can identify gaps in your defenses before an actual attacker does.
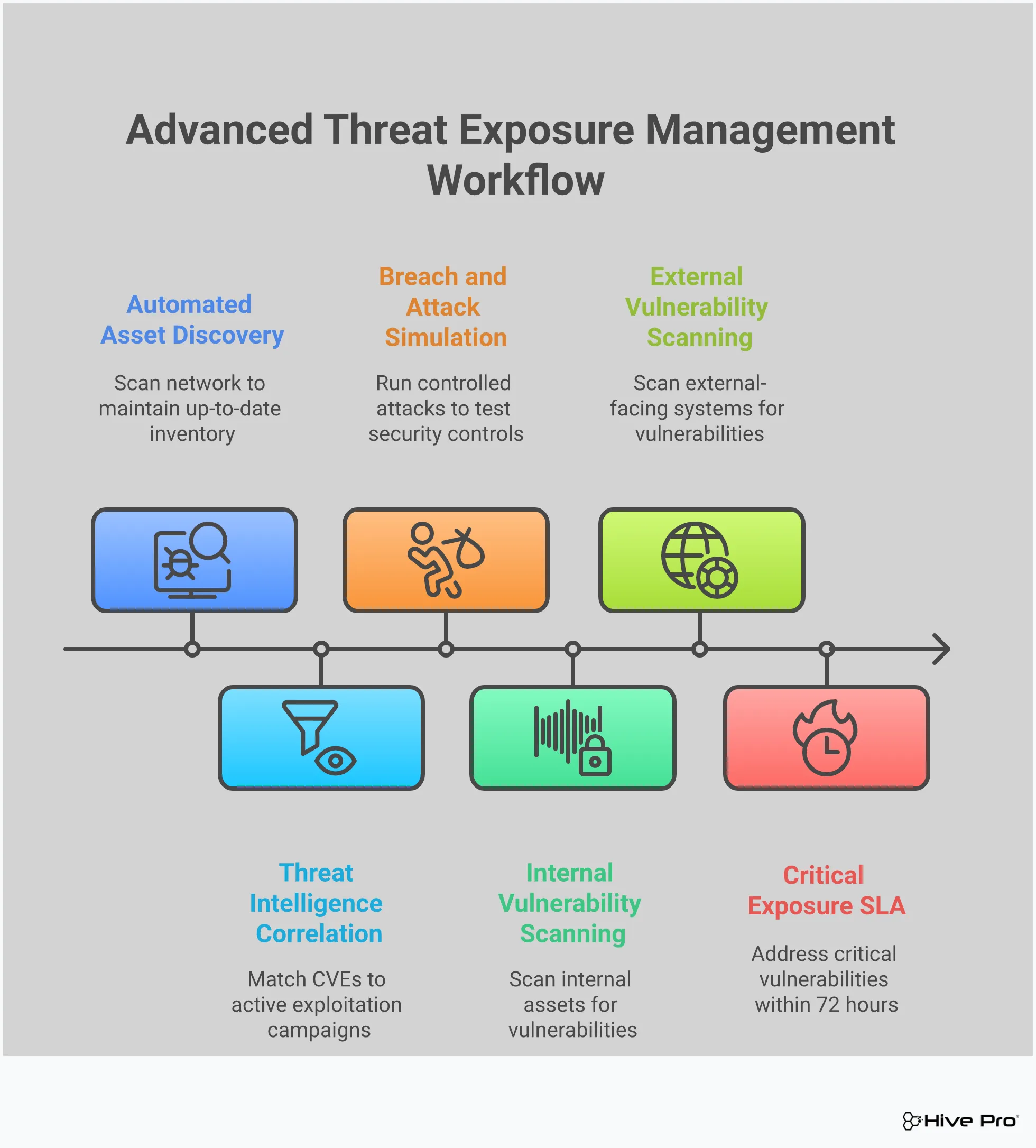
These stages aren’t just separate features; they are integrated components of a complete Continuous Threat Exposure Management (CTEM) framework. The Uni5 Xposure platform guides you through all five stages defined by Gartner: Scoping, Discovery, Prioritization, Validation, and Mobilization. This end-to-end approach ensures that your security efforts are connected and build on each other. From discovering your full attack surface and prioritizing real-world threats to validating your defenses and mobilizing remediation teams, Hive Pro provides a unified workflow. This transforms your vulnerability management program from a reactive checklist into a strategic, proactive operation focused on measurable risk reduction.
Adopting a new platform is a big decision, so let’s get straight to the point: what tangible results can you expect? Moving to a proactive threat exposure management model with Hive Pro isn’t just about swapping out tools; it’s about fundamentally changing how your team operates for the better. The platform is designed to deliver clear, measurable improvements that directly address the biggest challenges security teams face, from alert fatigue to inefficient patching cycles. By consolidating your view of risk and focusing your efforts on the threats that pose a genuine danger, you can achieve a stronger security posture without burning out your team. Let’s look at the specific benefits you can gain.
If your team is struggling to keep up with a constant flood of alerts from tools like Qualys, Tenable, or Rapid7, this is a game-changer. Hive Pro helps you cut through the noise by focusing on what’s truly critical. The platform’s approach to vulnerability and threat prioritization moves beyond simple CVSS scores, incorporating real-time threat intelligence to identify which vulnerabilities are actively being exploited. This allows your team to concentrate its resources on the small fraction of vulnerabilities that pose an immediate threat, dramatically reducing the backlog. By addressing the most urgent risks first, Hive Pro helps organizations reduce their exploitable vulnerabilities by as much as 95%.
Toggling between different dashboards and spreadsheets to get a complete picture of your security landscape is inefficient and increases the chance that something critical will be missed. The Uni5 Xposure Platform brings all your security risks together on a single screen. This unified view covers your entire attack surface, from on-premise servers to cloud assets and web applications. Having a comprehensive, real-time overview allows you to make faster, more informed decisions. It also simplifies reporting to leadership, as you can clearly demonstrate your organization’s risk posture and the progress your team is making to improve it.
The best way to handle a security incident is to prevent it from happening in the first place. Hive Pro shifts your team from a reactive stance to a proactive one. By predicting and highlighting the most likely attack paths, the platform helps you get ahead of adversaries. This predictive capability not only strengthens your defenses but also reduces the workload for your security analysts. Instead of chasing down every potential threat, your team can focus on targeted remediation efforts that have the greatest impact. This focused approach means you can resolve critical issues faster, shrinking the window of opportunity for attackers.
Theoretical risk scores can only tell you so much. Hive Pro goes a step further by validating your exposures through attack simulations. This process of adversarial exposure validation tests your security controls against real-world attack scenarios, showing you exactly how your defenses would hold up. This practical validation provides concrete proof of your security posture and uncovers weaknesses that vulnerability scans alone might miss. By confirming which risks are real and which are theoretical, you can enhance your overall security posture while also improving your team’s operational efficiency, ensuring that time and resources are spent where they’re needed most.
In cybersecurity, knowledge isn’t just power—it’s your first line of defense. Knowing which vulnerabilities exist is one thing, but understanding which ones are actively being exploited by attackers is what separates a reactive team from a proactive one. This is where threat intelligence becomes a game-changer, transforming your vulnerability management program from a guessing game into a precise, targeted operation. Hive Pro integrates threat intelligence directly into its platform, giving you a clear, real-time view of the threats that matter most. Instead of drowning in a sea of CVEs and theoretical risk scores, you can focus your resources on the vulnerabilities that pose a genuine, immediate risk to your organization. This intelligence-led approach helps you stay ahead of attackers by seeing what they see and patching what they plan to target, effectively shrinking your attack surface and preventing breaches before they happen. It’s about working smarter, not just harder, by using data to drive your defensive strategy.
Imagine having a dedicated research team feeding you critical updates every single day. That’s the advantage you get with HiveForce Labs, Hive Pro’s in-house intelligence unit. The platform provides daily threat advisories with real-time updates on emerging exploits, new vulnerabilities, and evolving attacker tactics. This constant stream of information ensures you’re never caught off guard by the latest threats circulating in the wild. You can immediately see how new developments impact your specific environment and take action before an attacker has the chance to make a move. It’s like having a direct line to the front lines of cybersecurity research, built right into your workflow.
Not all vulnerabilities are created equal. Many will never be exploited, while a select few become the go-to tools for attackers. Hive Pro’s Uni5 Xposure platform uses predictive and prescriptive analytics to help you proactively neutralize the most critical cybersecurity vulnerabilities. By correlating data from your environment with real-world threat intelligence, the platform highlights which vulnerabilities are not just high-risk on paper, but are actively being used in attacks. This allows you to significantly reduce your attack surface by focusing your remediation efforts on the issues that present a clear and present danger, cutting through the noise of thousands of low-risk alerts.
A strong security posture on paper doesn’t always hold up in a real attack. Hive Pro helps you bridge that gap by validating your exposure through realistic attack simulations. Instead of relying on theoretical risk scores, you can test your security controls against the same tactics and techniques used by actual adversaries. This Breach and Attack Simulation (BAS) capability gives you a true assessment of your defensive readiness. You can identify gaps in your security stack, find misconfigurations, and confirm that your controls are working as expected. It’s the ultimate reality check, providing concrete evidence of where you’re protected and where you need to improve.
Keeping up with the day-to-day threat landscape is crucial, but it’s just as important to understand the bigger picture. To help you stay strategically informed, Hive Pro delivers curated weekly and monthly cyber threat digests. These roundups provide high-level summaries, identify emerging trends, and offer critical insights into the evolving threat landscape. This allows you and your leadership team to look beyond immediate threats and make more informed, long-term decisions about your security strategy. It’s a simple way to stay ahead of what’s coming next without getting bogged down in the details of every single new threat.
Traditional vulnerability management often feels like a never-ending game of whack-a-mole. You run a scan, get a massive list of CVEs, and then your team spends weeks trying to figure out which ones to patch first. It’s a reactive cycle that can leave you feeling constantly behind, buried in data but lacking clear direction. This approach struggles to keep up with today’s sprawling attack surfaces and sophisticated threats. It focuses on the vulnerability but often misses the bigger picture of actual exposure.
Hive Pro offers a different path forward by shifting the focus from reactive vulnerability management to proactive threat exposure management. Instead of just identifying weaknesses, the platform helps you understand your true risk by connecting vulnerabilities to active threats, asset criticality, and existing security controls. This is the core of a Continuous Threat Exposure Management (CTEM) program—a unified, proactive strategy that gives you a continuous, 360-degree view of your security posture. It’s about moving from asking “What are we vulnerable to?” to answering “How are we most likely to be attacked, and what can we do about it right now?” This fundamental shift is built on a unified platform, seamless integration with your current tools, and a proactive mindset.
If your security team is constantly switching between different dashboards for vulnerability scanning, threat intelligence, and asset management, you know how fragmented the traditional approach can be. These siloed tools create blind spots and make it nearly impossible to get a clear, consolidated view of your actual risk. You’re left trying to piece together a puzzle with missing pieces.
Hive Pro’s Uni5 Xposure platform brings everything together into a single, actionable framework. It unifies data on vulnerabilities, threats, business context, and security controls, eliminating the need to juggle multiple tools. This gives security leaders a real-time, cross-environment view of exposure, from your code repositories to your cloud infrastructure. By breaking down these silos, you can finally align your security efforts with your most critical business priorities.
Adopting a new platform shouldn’t mean you have to abandon the tools your team already knows and trusts. A common hurdle with new security solutions is the “rip and replace” requirement, which can be disruptive and costly. Hive Pro is designed to work with your current security ecosystem, not against it.
The Uni5 Xposure platform seamlessly integrates with a wide range of vulnerability scanners, patch management systems, and ITSM platforms you already have in place. It acts as a central intelligence hub, pulling data from these disparate sources to enrich its analysis and provide a more complete picture of your exposure. This integration makes the transition from a traditional, risk-based approach to a full Continuous Threat Exposure Management program much smoother.
The classic vulnerability management cycle is inherently reactive: scan, find thousands of issues, and then race to patch the ones that seem most urgent based on a CVSS score. This often leads to “patch fatigue” and leaves teams struggling to keep up, all while potentially missing the vulnerabilities that attackers are actually exploiting.
Hive Pro flips the script by enabling a proactive defense. Instead of just reacting to a long list of vulnerabilities, the platform uses predictive and prescriptive analytics to help you neutralize critical threats before they can be exploited. The focus shifts from simply patching to strategically reducing your total attack surface. By prioritizing threats based on real-world exploitability and business impact, you can direct your resources to the fixes that matter most and get ahead of attackers.
When you’re evaluating a new security platform, technical specs and feature lists only tell part of the story. The real test is how it performs in the hands of security teams on the front lines. Across the board, professionals who use Hive Pro consistently point to its thoughtful design, collaborative capabilities, and the clarity it brings to complex security challenges. It’s one thing for a platform to have powerful features; it’s another for it to be genuinely useful and easy to adopt.
For busy teams juggling countless alerts and priorities, a tool that simplifies their work instead of adding complexity is a game-changer. User feedback highlights that Hive Pro delivers on this promise by making threat exposure management more intuitive and actionable. From its user-friendly interface to the way it fosters better teamwork, the platform is clearly designed with the end-user in mind. This focus on usability allows teams to spend less time managing their tools and more time reducing risk and strengthening their security posture. Let’s look at what users are saying about their experience.
In a field filled with complex tools and steep learning curves, simplicity is a superpower. Users consistently praise Hive Pro for being “intuitive, insightful, and highly actionable.” This means your team can get started quickly, making sense of complex exposure data without weeks of training. The platform is designed to guide you toward the most critical actions, translating raw data into a clear, manageable path forward. This ease of use is essential for making a proactive defense strategy accessible to the entire security organization, not just a few specialists. When a platform feels intuitive, teams are more likely to use it to its full potential, leading to better security outcomes.
Effective cybersecurity is a team sport, but siloed tools can often create friction between departments. Hive Pro helps bridge these gaps by creating a unified environment where everyone works from the same playbook. The platform’s design fosters a more collaborative atmosphere, a point reflected in its high ratings for work-life balance. When workflows are streamlined and communication is clear, teams experience less friction and can resolve issues faster. By providing a single source of truth for your organization’s cyber risks, Hive Pro ensures that vulnerability management, SecOps, and IT teams are all aligned on priorities and remediation efforts, leading to a more cohesive and efficient security program.
Security teams are often drowning in data but starved for wisdom. The challenge isn’t a lack of information, but the difficulty in identifying what truly matters. This is where Hive Pro excels, earning an impressive 4.9 out of 5 rating on Gartner Peer Insights for its Exposure Assessment capabilities. Users value the platform’s ability to cut through the noise and provide clear, contextualized insights that support confident, data-driven decisions. Instead of just presenting a long list of vulnerabilities, Hive Pro helps you understand your total attack surface and focus on the threats that pose a genuine risk to your business. This clarity is fundamental for shifting from a reactive to a proactive security model.
How is this different from the vulnerability scanner I already use? Think of your current scanner as a tool that creates a list of potential problems. Hive Pro takes that list and tells you which handful of problems could actually burn your house down. Instead of just identifying vulnerabilities, our platform adds a critical layer of intelligence. It analyzes which weaknesses are actively being exploited by attackers in the real world, so your team can stop chasing thousands of low-priority alerts and focus on the few that pose a genuine, immediate threat.
Do I need to replace my current security tools to use Hive Pro? Not at all. Hive Pro is designed to make your existing security stack smarter, not replace it. The platform integrates seamlessly with the vulnerability scanners, patch management systems, and other tools you already rely on. It acts as a central command center, pulling in data from these different sources to give you a single, unified view of your threat exposure and help you get more value from the tools you’ve already invested in.
What makes Hive Pro’s threat intelligence different from other sources? Many threat intelligence feeds are generic and can add to the noise. Our intelligence comes from our in-house research team, HiveForce Labs. They focus specifically on attacker behavior and active exploits, providing predictive and prescriptive insights. This means the intelligence powering our platform isn’t just a list of what’s theoretically possible; it’s a focused view of what attackers are doing right now, allowing you to fix weaknesses before they become the target of the next big attack.
How does Breach and Attack Simulation (BAS) help with vulnerability management? Finding a vulnerability is only half the battle. The real question is whether your security controls could stop an attacker from actually exploiting it. Our built-in BAS capabilities let you safely run simulated attacks against your environment to test your defenses. This helps you validate whether a vulnerability truly represents an exposure, or if your existing controls already have it covered. It provides real-world proof of your security posture and helps you find gaps before an attacker does.
My team is already overwhelmed. Will this create more work? The entire purpose of the platform is to do the opposite. We know security teams are stretched thin, which is why Hive Pro is designed to reduce the workload, not add to it. By automatically prioritizing the tiny fraction of vulnerabilities that pose a real danger, it eliminates the noise and guesswork. Your team gets a clear, manageable to-do list of what to fix first, allowing them to work more efficiently and have a greater impact on your organization’s security.