Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Is your security program truly reducing risk, or is it just getting really good at patching? This question is at the heart of the exposure management vs vulnerability management debate. A traditional approach can tell you that a door has a weak lock, but it can’t tell you if that door leads to a broom closet or your company’s crown jewels. Exposure management provides that missing context. It layers in threat intelligence, business criticality, and attack path analysis to help you distinguish between a theoretical weakness and a clear and present danger, allowing you to work smarter and make confident, risk-based decisions.
Think of exposure management as a continuous process for finding and fixing security risks before they can be exploited. It’s about seeing your organization through an attacker’s eyes, identifying all the potential entry points and weak spots across your entire digital footprint. Imagine you’re securing a house. You wouldn’t just check if the front door lock is strong (a vulnerability); you’d also walk the entire property to see if a window was left open, if the back gate is unlocked, or if a ladder is leaning against the wall. These are all exposures—potential pathways for an intruder.
This approach shifts security from a narrow focus on individual software flaws to a holistic view of your entire attack surface. The goal is to move from a reactive “patch-it-when-we-find-it” cycle to a proactive security posture. Instead of just working through a list of known vulnerabilities, you’re actively hunting for any condition that could lead to a breach. A modern threat exposure management platform helps you map these pathways, assess the risks, and prioritize what to fix first, all in real time. This allows you to make smarter, more informed decisions about where to focus your team’s limited time and resources.
In practice, exposure management involves a cycle of finding, validating, and fixing security risks across every digital asset your organization owns—from servers and laptops to cloud instances and software. The goal is to map out every potential attack path an adversary could take. This goes far beyond just looking for software bugs. It means examining everything that contributes to your overall risk, including your network configurations, data flows, user identities, and any external-facing systems. It’s about building a complete picture of your attack surface to achieve total attack surface management and understand where you are truly exposed.
Exposure management works by bringing all your security data together into a single, unified view. Instead of juggling alerts from a dozen different tools, this approach connects the dots to give you a complete picture of your risk. It uses continuous scanning and monitoring to watch for problems around the clock. This allows you to see not just classic vulnerabilities, but also other critical exposures like misconfigurations in your cloud environment, user accounts with too many permissions, or exposed employee credentials. By correlating this information, you can achieve true vulnerability and threat prioritization, focusing on the exposures that pose the most immediate and significant threat to your business.
Before we can really appreciate what exposure management brings to the table, we need to have a solid understanding of its predecessor: vulnerability management. For decades, this has been the go-to strategy for security teams. It’s a foundational practice, but as the threat landscape has evolved, its limitations have become more apparent. Think of it as the essential first step in a much longer journey toward true cyber resilience. Let’s break down what it is and how the traditional process works.
At its core, vulnerability management is the process of finding, evaluating, and fixing known weaknesses in your software and systems. It’s a practice that’s been around for over 20 years, focusing on patching specific software bugs, often identified by a CVE number. The cycle is straightforward: you scan your assets to discover vulnerabilities, work on vulnerability and threat prioritization, assign them for remediation, and then verify that the patch was successful. It’s a necessary, systematic approach to closing known security gaps. The goal is to methodically reduce the number of exploitable flaws in your environment, one patch at a time.
It’s easy to confuse vulnerability assessment with vulnerability management, but they aren’t the same thing. An assessment is just the scan—it gives you a list of what’s broken, like a vulnerable server. Management is the entire lifecycle of dealing with those findings. The real challenge with traditional vulnerability management is that it often stops there. It tells you a flaw exists but doesn’t always connect the dots to tell you if it’s a genuine problem for your business. It identifies known weaknesses but often lacks the context to map potential attack paths or prioritize what truly puts your most critical assets at risk. This is where the focus on individual flaws, rather than the complete attack surface, can leave you exposed.
At first glance, exposure management might sound like a simple rebranding of vulnerability management. But the two represent a fundamental difference in how we approach cybersecurity. Think of it as the difference between patching individual potholes and redesigning an entire traffic system for safety and efficiency. While vulnerability management is essential for fixing known flaws, exposure management takes a holistic view of your entire digital landscape to understand and reduce your true, contextualized risk. It’s about moving from a checklist of problems to a strategic map of your defenses.
Traditional vulnerability management is focused and specific. Its main job is to find and catalog software flaws, usually identified by a Common Vulnerabilities and Exposures (CVE) number. It’s an inventory of known weaknesses in your applications and systems. Exposure management, on the other hand, dramatically widens the lens. It examines your entire total attack surface, looking beyond just CVEs. This includes everything from misconfigured cloud services and weak identity controls to exposed APIs and shadow IT. It connects the dots between these different elements to show you the bigger picture of how an attacker might see—and target—your organization.
This is where the difference becomes critical for security teams. Vulnerability management often prioritizes tasks based on technical severity scores like CVSS. While useful, this can generate a massive list of “critical” vulnerabilities without the context of which ones pose a genuine, immediate threat to your business. Exposure management changes the conversation by prioritizing based on real-world risk. It helps you answer the most important questions: Can this vulnerability actually be exploited in our environment? What critical assets would be compromised? Is there active threat intelligence showing attackers are using this exploit right now? This approach cuts through the noise, allowing you to focus on the threats that truly matter.
Vulnerability management is, by its nature, a reactive process. It’s a necessary cycle of scan, find, patch, and repeat. You are constantly responding to a list of problems that have already been discovered. Exposure management encourages a proactive mindset. It’s about getting ahead of attackers by continuously testing your defenses and understanding how different exposures could be chained together in an attack path. Instead of just asking, “What’s vulnerable?” it asks, “How could we be breached, and what can we do to make that harder?” This approach provides a holistic view of your true risk, telling you not just what’s broken, but if that break actually matters.
If you feel like you’re playing a constant game of whack-a-mole with vulnerabilities, you’re not alone. Traditional vulnerability management has been a cornerstone of cybersecurity for years, and for good reason. It helps us find and catalog weaknesses in our systems. But the digital world has expanded far beyond what these legacy approaches were built for. Today’s environments are a complex mix of on-premise servers, cloud infrastructure, IoT devices, and countless applications. Simply scanning for known vulnerabilities isn’t cutting it anymore.
Security teams are often left with a mountain of data but no clear path forward. This approach can create more noise than signal, leaving you to sort through thousands of “critical” alerts without understanding which ones pose a genuine, immediate threat to your business. It’s time to move beyond just managing vulnerabilities and start managing your total exposure.
We’ve all been trained to jump when we see a high CVSS score. But these scores, while useful for standardization, often lack the real-world context needed to make smart decisions. A vulnerability’s severity score doesn’t tell you if it’s actively being exploited in the wild, if a public exploit is available, or if it even applies to your specific environment. This can lead to teams spending weeks patching a “critical” vulnerability on an isolated, low-impact asset while a “medium” vulnerability on a crown-jewel server goes unnoticed. True vulnerability and threat prioritization requires looking beyond the score to understand the actual risk to your organization.
Traditional vulnerability management is good at what it was designed for: finding known weaknesses in your software and operating systems. The problem is, that’s only a fraction of your modern attack surface. What about misconfigured cloud storage, exposed APIs, or forgotten subdomains that make up your total attack surface? These are the entry points attackers love to find, yet they often fall outside the scope of legacy scanning tools. Without a complete picture of all your assets—both known and unknown—you’re essentially leaving doors unlocked and hoping no one checks the handle. You can’t protect what you can’t see, and these visibility gaps create significant, unaddressed risks.
If your security team is drowning in alerts, you know this challenge all too well. Vulnerability scanners can generate reports with thousands of findings, and each one comes with a demand for attention. This constant flood of information leads to serious alert fatigue, making it nearly impossible to distinguish real threats from background noise. When everything is marked as urgent, nothing is. This problem is often made worse by using too many separate security tools, which creates data silos and prevents you from getting a clear picture. A unified view of cyber risks is essential to cut through the clutter and focus your team’s efforts on the exposures that truly matter.
The way you prioritize risk is arguably the biggest difference between vulnerability management and exposure management. Traditional vulnerability management often leans heavily on technical severity scores, like the Common Vulnerability Scoring System (CVSS). While helpful, a CVSS score exists in a vacuum. It tells you how severe a vulnerability could be in a perfect storm, but it doesn’t tell you if that storm is even on the horizon for your specific organization. This can lead to teams spending countless hours patching “critical” vulnerabilities on low-impact, isolated assets while a less severe but internet-exposed vulnerability on a crown-jewel application gets overlooked.
Exposure management flips the script by prioritizing risks based on a much richer set of data. It moves beyond a single score to ask a series of critical questions: Is this vulnerability actually exploitable in our environment? Is it on a mission-critical asset? Can an attacker reach it from the outside? Are threat actors actively using this exploit in the wild? By layering asset criticality, threat intelligence, and attack path analysis on top of vulnerability data, you get a realistic, contextualized view of your risk. This allows you to focus your team’s time and energy on the exposures that pose a clear and present danger to your business.
A high CVSS score on a server in an isolated development lab is far less urgent than a medium-score vulnerability on your main, public-facing web application. Exposure management understands this distinction and brings that crucial context into the prioritization process. It goes beyond the theoretical severity of a flaw to assess its real-world risk to your organization. This approach combines vulnerability data with a deep understanding of your attack surface, asking if an attacker can actually reach the weakness and if the system it affects is vital to your operations. By layering these factors, you get a true risk score that reflects your unique environment, allowing you to prioritize with confidence.
Security isn’t just an IT function; it’s a core business concern. A key strength of exposure management is its ability to translate technical risks into tangible business impact. Instead of just reporting on the number of open CVEs, you can have a more meaningful conversation about which exposures threaten customer data, which could disrupt key services, or which might damage the company’s reputation. This reframes remediation as a strategic activity that protects the bottom line. By focusing on the exposures that truly matter to business operations, you can more effectively guide your security efforts and protect what’s most important to the organization.
Your internal context is only half the picture. The other half is what’s happening outside your walls in the global threat landscape. A modern exposure management program integrates real-time threat intelligence to see which vulnerabilities are being actively exploited by attackers. This means paying close attention to data from sources like CISA’s Known Exploited Vulnerabilities (KEV) catalog and insights from dedicated security research teams. Understanding which flaws are part of an attacker’s current playbook helps you act decisively. This intelligence-led approach, powered by teams like HiveForce Labs, allows you to get ahead of attacks by fixing the holes that threat actors are targeting right now.
Think of your list of vulnerabilities as a map of potential entry points into your organization. Without context, every door and window looks equally important. Threat intelligence is the guide that tells you which doors attackers are actively trying to pick, which windows they’ve broken before, and what tools they’re using to do it. It transforms your vulnerability management from a compliance-driven checklist into an intelligence-led defense strategy.
Instead of just asking, “What are our weaknesses?” you start asking, “Which of our weaknesses are attackers most likely to use against us right now?” This shift is fundamental to exposure management. It moves the focus from a theoretical risk score to the practical reality of active threats. By layering in data on attacker tactics, techniques, and procedures (TTPs), you can see your attack surface through their eyes. This allows you to prioritize remediation efforts not just on what could happen, but on what is likely to happen, based on credible, up-to-the-minute intelligence from sources like HiveForce Labs.
The threat landscape isn’t static, so your defense can’t be either. Integrating real-time threat data means your security posture can adapt as new threats emerge. This involves continuously feeding your exposure management program with insights on new malware campaigns, zero-day exploits, and shifts in attacker behavior. This live feed gives you visibility into cyber activities as they unfold, allowing you to connect the dots between a global event and a specific vulnerability in your environment. It’s the difference between reading last week’s news and getting a live alert, ensuring your team is always working with the most current picture of risk.
A high CVSS score doesn’t always mean a high risk to your business. Many high-severity vulnerabilities are never actively exploited in the wild. Threat intelligence helps you see which CVEs are actually being used by attackers. By combining vulnerability data with real-world exploitation evidence, you can perform more effective vulnerability and threat prioritization. This allows your team to distinguish between a theoretical weakness and a clear and present danger, focusing your resources on the vulnerabilities that are part of a known attacker’s playbook. This context is crucial for making smart, risk-based decisions.
Ultimately, the goal is to cut through the noise. With thousands of vulnerabilities to deal with, your team can’t fix everything at once. Threat intelligence helps you focus on what truly matters by highlighting the exposures that pose an immediate threat. By integrating data points like CISA’s Known Exploited Vulnerabilities (KEV) catalog and EPSS scores, you can align your remediation efforts with active attacker behavior. This intelligence-driven approach, supported by timely threat advisories, ensures your team spends its time and energy closing the gaps that attackers are most likely to find and exploit today.
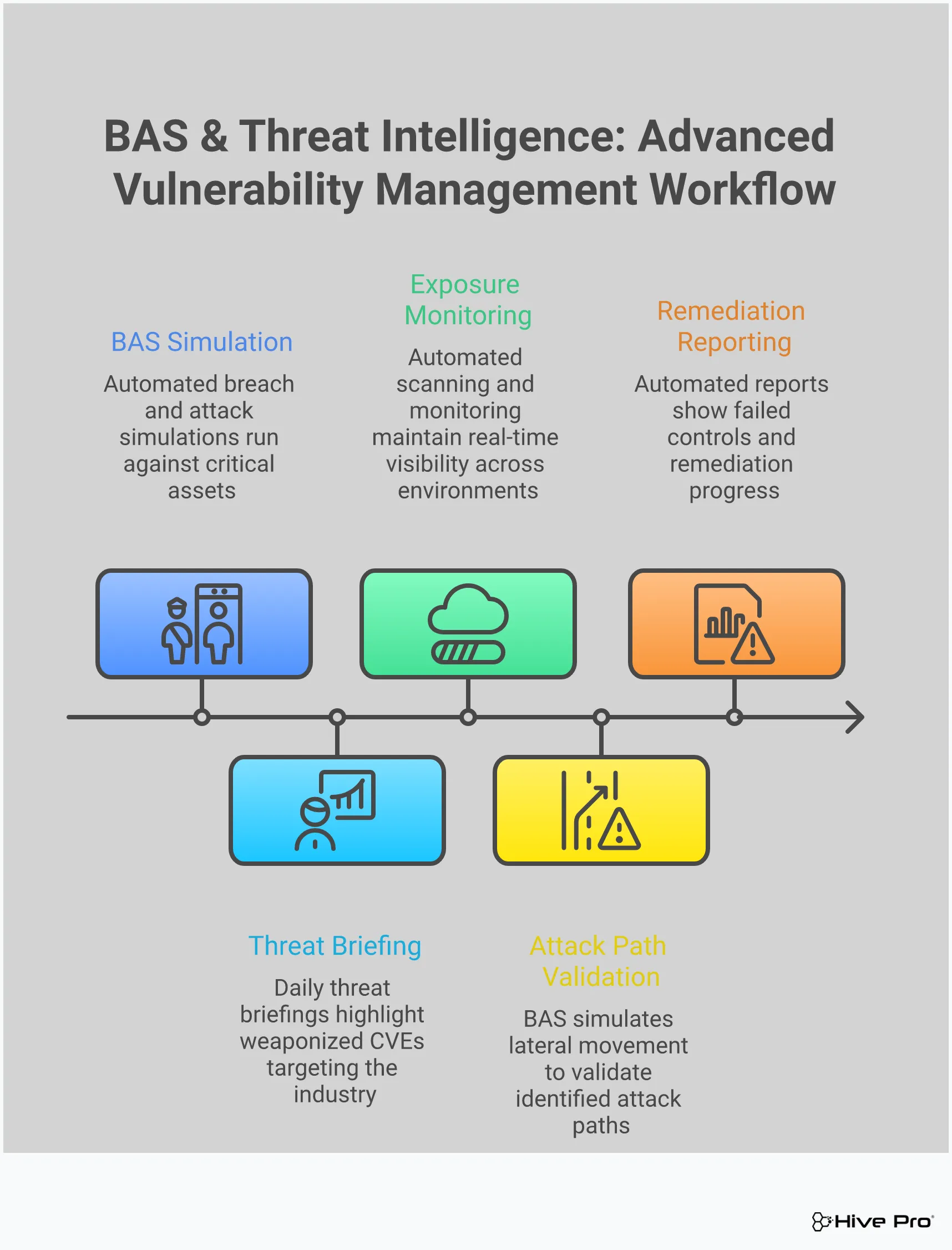
If vulnerability management is about finding the weak spots, Breach and Attack Simulation (BAS) is about actively testing them to see if they’ll break. Think of it as a fire drill for your cybersecurity defenses. Instead of just assuming your security tools will work during an actual attack, BAS lets you safely simulate real-world attack scenarios to see what happens. It’s a fundamental shift from a passive, hope-for-the-best approach to an active, evidence-based one.
This process helps answer the critical question that keeps security leaders up at night: “Are we truly secure, or do we just look good on paper?” By automating these controlled attacks, BAS platforms allow you to continuously validate your security controls, test your detection and response capabilities, and identify the most likely paths an attacker could take through your network. It moves the conversation beyond a simple list of vulnerabilities and toward a practical understanding of your actual resilience against an active threat. This is a key component of a modern threat exposure management program, helping you confirm that your security investments are delivering real protection.
You’ve invested heavily in firewalls, endpoint detection and response (EDR), and other security tools. But are they configured correctly? Are they actually blocking malicious activity as promised? BAS acts as a sparring partner for your security stack, running controlled simulations to see if your defenses can take a punch. This process of Adversarial Exposure Validation helps you find gaps, misconfigurations, and policy weaknesses before a real attacker can exploit them. It’s the ultimate quality assurance check, giving you concrete proof that your security controls are performing as expected and providing the protection you paid for.
BAS doesn’t just run generic tests; it simulates the specific tactics, techniques, and procedures (TTPs) used by today’s most active threat actors. This is where the platform’s value really shines. By leveraging up-to-the-minute threat intelligence from research teams like HiveForce Labs, BAS platforms can replicate the exact attack chains seen in the wild. This allows you to test your defenses against threats that are not just theoretical but are actively targeting organizations like yours. You can move from worrying about thousands of potential vulnerabilities to focusing on your resilience against the handful of attack paths that matter most right now.
Your environment is in a constant state of flux. New assets come online, software gets updated, and configurations change daily. A security assessment from last quarter is already out of date. BAS addresses this by making security testing a continuous, automated process. Instead of relying on periodic, manual penetration tests, you can run simulations automatically and frequently. This provides a constant feedback loop, giving you an always-on, realistic view of your security posture. This continuous assessment is a core principle of any strong exposure management strategy, ensuring you can adapt quickly as your attack surface evolves and new threats emerge.
Shifting from traditional vulnerability management to a comprehensive exposure management strategy is a smart move, but let’s be real—it’s not as simple as flipping a switch. This change impacts your processes, your technology, and your people. Like any significant operational upgrade, it comes with a few hurdles. But thinking through these potential challenges ahead of time is the best way to ensure a smooth transition.
Most organizations run into similar obstacles when they make the switch. They often find themselves wrestling with a flood of data from disconnected tools, navigating team dynamics and old habits, and figuring out how to make new platforms play nicely with their existing security stack. Let’s walk through each of these common challenges so you can build a game plan to address them head-on.
If your security team is juggling a dozen or more separate tools, you’re not alone. The problem is that this “tool sprawl” creates a messy, fragmented view of your security posture. Each tool generates its own data and alerts, making it nearly impossible to connect the dots and understand your true risk. This complexity can slow remediation from days to weeks or even months.
An exposure management program helps you cut through that noise. The goal is to unify your security data into a single, coherent view. Instead of drowning in raw data, you get synthesized insights that show you how different assets and weaknesses connect, giving you a clear picture of potential attack paths.
Your security team is likely already dealing with a high volume of alerts. The idea of adding another layer to their work can feel overwhelming. It’s important to frame exposure management not as another task, but as a better way of working. It helps reduce alert fatigue by showing your team which issues are actually exploitable and pose a real threat.
This approach requires a mental shift from a reactive “patch everything” mindset to a proactive one focused on business impact. Instead of chasing down every low-level vulnerability, your team can concentrate its efforts on the vulnerabilities that matter most.
You’ve already invested time and money into your current security tools, and you shouldn’t have to start from scratch. A modern exposure management platform is designed to be an integration layer, not a replacement for your entire stack. It should connect seamlessly with the tools you already use, from application security scanners to cloud security platforms.
Think of it as the connective tissue for your security program. By pulling data from your existing solutions, an exposure management platform can give you a complete and continuous view of your total attack surface. This allows you to leverage your current investments while gaining the context and visibility needed to see and manage risk across your entire organization.
Deciding between vulnerability management and exposure management isn’t about picking a winner. It’s about understanding where your security program is today and where you need it to be. Vulnerability management is a foundational practice that finds and fixes specific software flaws. Exposure management is the next step, offering a much wider view of your entire attack surface. It connects vulnerabilities with other weaknesses like misconfigurations, identity issues, and active threats to give you a true picture of your business risk. The right choice depends on your team’s maturity, your organization’s complexity, and your tolerance for risk.
To make the right call, start by looking at the kind of risks you’re trying to manage. If your primary concern is patching known software bugs, or CVEs, then a traditional vulnerability management program might feel sufficient. However, if you’re worried about the bigger picture—how a weak password, a misconfigured cloud asset, and a software flaw could combine into a major breach—then you’re thinking like an exposure management pro. Many risks simply can’t be fixed with a patch. They come from the complex interactions within your digital environment, which is where an exposure management program truly shines by providing that essential context.
The most effective security strategies don’t force an “either/or” decision. Instead, they treat vulnerability management as a critical component of a broader exposure management framework. Think of it this way: your VM program is excellent at identifying the “what” (the specific CVE), while your EM program answers the “so what?” (the actual business risk). By combining both, you create a much stronger security posture that addresses both individual flaws and the systemic risks they create. This integrated approach helps you manage threats more proactively and ensures your team’s efforts are always focused on the most critical issues, moving you from a reactive cycle to a strategic one.
How you measure success will shift depending on your approach. With vulnerability management, you’re likely tracking metrics like time-to-remediate, patch compliance rates, and the number of open critical vulnerabilities. These are important, but they don’t always tell the full story of risk reduction. An effective exposure management program tracks metrics that resonate with business leaders, such as the reduction in overall attack surface, the number of critical attack paths neutralized, and improved security control validation. Tracking the right vulnerability management metrics helps you demonstrate your team’s value in protecting the organization’s most important assets and securing future investment.
Shifting from vulnerability management to exposure management can feel like a big leap, but it doesn’t have to be overwhelming. It’s about adopting a new mindset and a more strategic process. Think of it less as a complete overhaul and more as a smart evolution of your current security practices. A successful transition boils down to a few core principles: seeing everything you need to protect, understanding what threats matter most, and working together to fix them.
This isn’t about buying a single tool and calling it a day. It’s a continuous cycle that helps you stay ahead of attackers. By focusing on your entire attack surface and the real-world threats targeting it, you can move from a reactive state of patching endless vulnerabilities to proactively reducing your actual risk. A Continuous Threat Exposure Management (CTEM) program provides the framework for this shift. Let’s break down the practical steps you can take to put this into action and build a more resilient security posture for your organization.
You can’t protect what you don’t know you have. The first step is getting a complete and continuous view of your entire digital footprint. Your attack surface is dynamic—new cloud assets are spun up, old code is forgotten, and third-party applications are integrated. A one-time scan won’t cut it. You need a process for continuous discovery to find all your internet-facing assets, including shadow IT and forgotten infrastructure. This gives you the foundational visibility needed for a true attack surface management program, ensuring no potential entry point goes unnoticed.
Once you have a clear view of your attack surface, the next question is: what do you fix first? With thousands of potential exposures, manual analysis is impossible. This is where automation becomes your best friend. Modern exposure management tools automatically pull in context from various sources—like real-time threat intelligence and business criticality—to score risks accurately. This allows you to move beyond basic CVSS scores and focus your team’s limited time and resources on the vulnerabilities that pose a genuine threat to your organization. This intelligent vulnerability and threat prioritization is what separates a busy security team from an effective one.
Exposure management is a team sport. Security can’t operate in a vacuum. To truly reduce exposure, you need buy-in and collaboration from IT, DevOps, and business leaders. This means breaking down silos and creating shared goals. Establish clear lines of communication and responsibility so that when a critical exposure is identified, the right team can act on it quickly. When everyone understands their role in protecting the organization—from developers writing secure code to IT teams patching systems—your entire security posture becomes stronger. This unified approach is the key to turning insights into meaningful action and lasting risk reduction.
Isn’t “exposure management” just a new marketing term for vulnerability management? Not at all. While they’re related, the difference is in the scope and mindset. Vulnerability management is a critical process focused on finding and patching specific software flaws, or CVEs. Exposure management takes a much broader view. It looks at your entire attack surface—including misconfigurations, weak identity controls, and exposed data—to understand how these different elements could be chained together in a real attack. It’s the difference between checking if a lock is broken and checking if the door is unlocked, the window is open, and a ladder is leaning against the house.
My team is already swamped with alerts. Won’t this approach just create more noise? Actually, the goal is the exact opposite. A good exposure management program is designed to cut through the noise, not add to it. Instead of giving you another long list of problems, it adds context from threat intelligence and business criticality to your existing data. This helps you see which of those thousands of alerts represent a genuine, immediate danger to your business. It helps your team stop chasing every “critical” CVSS score and focus their energy on the handful of exposures that attackers are most likely to exploit.
Do I have to replace my existing vulnerability scanner to adopt exposure management? No, you shouldn’t have to rip and replace your current tools. A strong exposure management platform is designed to integrate with your existing security stack. It acts as a central hub, pulling in data from your vulnerability scanners, cloud security tools, and other sources. It then enriches that data with additional context to give you a single, unified view of your risk. This allows you to get more value from the investments you’ve already made while filling in the visibility gaps between them.
How is using Breach and Attack Simulation (BAS) different from our annual penetration test? Think of it as the difference between an annual physical and wearing a fitness tracker every day. A penetration test is a valuable, point-in-time assessment that provides a deep, manual analysis of your defenses. Breach and Attack Simulation, on the other hand, is a continuous and automated process. It constantly runs safe, simulated attacks against your security controls to give you a real-time feedback loop on their effectiveness. Both are useful, but BAS provides the ongoing validation needed to keep up with a constantly changing environment.
What’s the most important first step my team can take to start this shift? The best place to start is with visibility. You can’t protect what you can’t see. Begin by focusing on continuous attack surface discovery to get a complete inventory of all your internet-facing assets, including forgotten servers or shadow IT. This foundational step gives you the map you need to understand your true digital footprint. Once you know what you have, you can begin the work of prioritizing which exposures on those assets pose the greatest risk.