Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
If your security stack feels like a cluttered garage full of single-purpose tools, you’re not alone. You have one tool for endpoints, another for the network, and a few more for the cloud—none of which communicate effectively. This patchwork approach creates dangerous blind spots and buries your team in a mountain of disconnected alerts. It’s an inefficient, reactive way to manage security. An enterprise security platform offers a way out of this chaos. It brings your security functions together under one roof, providing a single source of truth and a unified view of your entire environment. This guide will explain what these platforms are, why point solutions no longer work, and what to look for in a solution that can truly centralize your defenses.
Think of an enterprise security platform as your central command center for cybersecurity. It’s a unified approach to protecting your company’s computers, data, and applications from online threats. Instead of juggling a dozen different tools that don’t talk to each other, a platform brings everything together under one roof. The main goal is to give you a complete and connected view of your security posture, helping you spot and stop risks at every level of your organization.
In the past, you might have bought a separate tool for firewalls, another for endpoint protection, and yet another for vulnerability scanning. A modern security platform integrates these functions and more. It helps you manage a constantly expanding attack surface that now includes everything from on-premise servers to cloud services and remote employee devices. By consolidating your security stack, you can move from a reactive, tool-focused mindset to a proactive, strategic one. This shift allows your team to focus on genuine threats instead of getting bogged down by managing multiple, disconnected systems.
If your security strategy feels like a game of whack-a-mole, you’re probably relying on point solutions. These standalone tools are designed to solve one specific problem, but they often operate in isolation. This creates information silos, leaving your team without the unified visibility needed to connect the dots during an attack. As your company adopts new technologies and your digital footprint grows, these visibility gaps become dangerous blind spots.
Many organizations lack the threat intelligence to identify and prioritize threats effectively. Point solutions worsen this problem by creating more alerts than your team can handle, without providing the context to know which ones matter. Juggling multiple dashboards and workflows is inefficient, drains resources, and ultimately makes it easier for attackers to slip through the cracks.
A modern security platform isn’t just one piece of software; it’s an integrated suite of essential tools working together. While features vary, most comprehensive platforms are built around a few core components. A good platform can bring together several important security tools to help teams find and stop threats more effectively.
Key components often include:
Adopting a centralized security platform is more than just a technical upgrade; it’s a smart business decision. A unified, cloud-based platform provides scalable and centralized management, giving your business the flexibility to grow without compromising on security. Instead of purchasing, implementing, and maintaining multiple products, you invest in a single, cohesive system. This consolidation simplifies vendor management and often leads to a lower total cost of ownership.
By bringing your security tools together, you also improve your team’s efficiency. Automation handles the routine tasks, freeing up your analysts to focus on high-impact investigations. This helps you increase ROI and get more value from your security investments. A centralized platform gives you a single source of truth for your security data, making it easier to demonstrate compliance, report on risk to leadership, and build a more resilient, future-proof security program.
When you’re shopping for an enterprise security platform, the sheer number of options can feel overwhelming. Every vendor promises the world, but the reality is that not all platforms are built the same. To cut through the noise, you need to focus on the core capabilities that will actually make your security team’s life easier and your organization safer. A truly effective platform isn’t just another tool—it’s a central hub that brings clarity to your security operations.
Think of it as moving from a cluttered toolbox full of single-purpose gadgets to a sleek, all-in-one multi-tool. Instead of juggling a dozen different point solutions that don’t talk to each other, a modern enterprise platform unifies your defenses. This gives you a single source of truth, automates tedious manual work, and helps you spot threats you might otherwise miss. As you evaluate your options, look for platforms that deliver on a few key fronts: comprehensive visibility, intelligent automation, and proactive threat detection. These are the features that separate the nice-to-haves from the must-haves and form the foundation of a strong, resilient security posture.
Having all your security data in one place is a game-changer for effective security management. That’s the core job of a Security Information and Event Management (SIEM) solution. It pulls in logs and event data from across your entire network—from servers and firewalls to applications and endpoints—and puts it all into a single, searchable dashboard. This centralized view makes it infinitely easier to connect the dots and spot suspicious activity that would be invisible otherwise. A robust SIEM solution provides a complete platform that helps your team find, investigate, and stop cyber threats by bringing several important security tools together. Without it, you’re stuck manually piecing together clues from dozens of different sources, which is slow, inefficient, and prone to error.
Let’s be honest: your security team is busy. They don’t have time to manually investigate every single alert that comes in. This is where Security Orchestration, Automation, and Response (SOAR) capabilities become essential. SOAR platforms automate the repetitive, time-consuming tasks that eat up your team’s day, like enriching alerts with threat intelligence, quarantining a suspicious endpoint, or blocking a malicious IP address. By creating automated playbooks for common incidents, you can streamline security tasks and responses, allowing your organization to react to threats in minutes instead of hours. This not only reduces your time to resolution but also frees up your analysts to focus on the complex, high-stakes investigations that truly require their expertise.
Some of the most dangerous threats are the ones that come from within, whether it’s a malicious insider or a compromised user account. User and Entity Behavior Analytics (UEBA) is designed to catch these threats by learning the normal patterns of behavior for every user and device on your network. It then flags any activity that deviates from that baseline. For example, it can spot when an employee suddenly logs in from a different country or a server starts accessing files it never has before. This capability is critical for identifying unusual user and system behaviors that might indicate a security threat. It’s a must-have for enhancing your detection of insider threats and compromised accounts before they can do serious damage.
Your organization’s attack surface isn’t confined to the office anymore. It extends to every laptop, mobile device, and cloud server your business relies on. That’s why a modern security platform must provide integrated protection across both endpoints and cloud environments. Juggling separate tools for each is a recipe for visibility gaps and operational headaches. An enterprise cyber risk and security platform helps businesses find, measure, and eliminate threats by consolidating multiple security tools into a single system. This approach not only simplifies data management by giving you one place to see everything but also strengthens your overall security posture by ensuring consistent policies and protection everywhere.
Cybercriminals are constantly evolving their tactics, which means traditional, signature-based security tools can’t keep up. They’re great at catching known threats, but they’re blind to new and emerging attacks. This is where artificial intelligence comes in. AI-powered threat detection is becoming a non-negotiable feature in enterprise security. Platforms that use advanced AI can learn about new attack patterns in real time, enabling them to identify and respond to emerging threats more effectively than methods that rely on static rules. This proactive approach allows you to stay ahead of attackers by spotting novel malware, sophisticated phishing campaigns, and other advanced threats before they can execute their mission.
Choosing the right enterprise security platform can feel overwhelming with so many options on the market. Each one comes with its own strengths, focusing on different areas like endpoint protection, log management, or proactive exposure management. To help you sort through the noise, we’re breaking down six of the top platforms. We’ll look at what makes each one unique so you can find the best fit for your security program and business goals.
Hive Pro’s Uni5 Xposure Platform is built to shift your security program from a reactive to a proactive stance. It’s a Continuous Threat Exposure Management (CTEM) platform that gives you a unified view of your entire attack surface, from on-prem to the cloud. Instead of just listing vulnerabilities, it helps you focus on the ones that pose an actual threat to your business. Using threat intelligence from its in-house HiveForce Labs, the platform prioritizes risks based on real-world attacker activity. It also includes Breach and Attack Simulation (BAS) to continuously validate your security controls, helping you find and fix gaps before they can be exploited. This end-to-end approach helps you confidently reduce your exposure.
Splunk is a household name in the security world, and its Enterprise Security (ES) platform is a powerful Security Information and Event Management (SIEM) solution. Its core strength lies in collecting, aggregating, and analyzing massive amounts of machine data from across your entire IT infrastructure. This allows security teams to get a centralized view of their environment, detect malicious activity, and streamline incident investigations. By bringing together various security tools and data sources, Splunk ES helps organizations find and respond to threats more effectively. It’s a solid choice for teams that need deep visibility and robust analytics to manage security events at scale and speed up their response times.
Palo Alto Networks offers Cortex, a platform designed to stop sophisticated attacks with a focus on automation. As an Extended Detection and Response (XDR) solution, Cortex goes beyond the endpoint by integrating data from your network, cloud, and third-party sources. This comprehensive data set fuels its AI and machine learning engines, which work to uncover stealthy threats and automate complex investigation workflows. The goal is to reduce the manual effort required from security analysts, allowing them to focus on more strategic tasks. For organizations looking to consolidate security operations and leverage automation to handle a high volume of alerts, Cortex provides a powerful, data-driven approach to threat detection and response.
IBM Security QRadar is another heavyweight in the SIEM space, known for its intelligent security analytics. The QRadar platform excels at collecting and correlating vast amounts of event data from across an organization’s network to identify high-priority threats. It uses behavioral analytics and threat intelligence to detect anomalies that might indicate an advanced attack, helping teams uncover threats that might otherwise go unnoticed. QRadar also offers a suite of integrated tools for risk management, vulnerability scanning, and incident forensics. This makes it a comprehensive solution for mature security teams that need deep analytical capabilities to understand and respond to complex threats across their hybrid cloud environments.
Designed specifically for small and medium-sized businesses, Microsoft Defender for Business brings enterprise-grade endpoint security to organizations with up to 300 employees. It’s a cost-effective solution that simplifies security without sacrificing power. The platform includes key features like threat and vulnerability management, attack surface reduction, and next-generation antivirus. It also provides endpoint detection and response (EDR) capabilities to help detect and investigate advanced threats. Because it integrates seamlessly into the Microsoft 365 ecosystem, it’s an especially compelling option for businesses already invested in Microsoft’s cloud services, offering a streamlined way to protect their devices from ransomware and other malware.
The CrowdStrike Falcon Platform is a leader in the cloud-native endpoint protection space. Its standout feature is its single, lightweight agent that provides a wide range of security functions without slowing down endpoints. The platform combines next-generation antivirus, endpoint detection and response (EDR), and even offers a 24/7 managed threat hunting service. By leveraging artificial intelligence and one of the world’s most advanced threat intelligence engines, Falcon focuses on stopping breaches before they can cause damage. It’s a top choice for organizations of all sizes that want a modern, cloud-first approach to endpoint security that is both highly effective and easy to manage.
Choosing an enterprise security platform is a big commitment. It’s not just about ticking off feature boxes; it’s about finding a partner in your security strategy. The right platform should feel like an extension of your team, making everyone’s job easier while strengthening your defenses. As you evaluate your options, it’s easy to get lost in technical specs and impressive demos. But the best fit for your organization comes down to a few practical considerations.
Think about how a new platform will slot into your existing workflows, your team’s current skill set, and your company’s future growth plans. You’re looking for a solution that simplifies complexity, not one that adds another layer of it. The goal is to gain a clear, unified view of your security posture and empower your team to act decisively. A platform might have the most advanced features on the market, but if it’s a nightmare to implement or requires constant hand-holding, it will quickly become more of a liability than an asset. Let’s walk through the key criteria you should use to weigh your options and find a platform that truly meets your needs.
When you look at pricing, it’s tempting to focus on the upfront license fee, but that’s only one piece of the puzzle. To get the full picture, you need to calculate the total cost of ownership (TCO). This includes ongoing costs like maintenance contracts, support packages, and the time your team will spend on training and implementation. A platform that seems cheaper initially might end up costing more if it requires specialized skills to manage or constant professional services to maintain. A good way to frame this investment is to compare the TCO against the potential cost of a breach and the efficiency gains for your team.
Your business isn’t static, and your security platform shouldn’t be either. You need a solution that can grow with you, whether that means adding new users, expanding to new cloud environments, or handling a massive increase in data volume. Ask potential vendors how their platform performs under pressure and what’s involved in scaling up. Cloud-native platforms often have an edge here, as they’re built for flexibility and can adapt to changing demands without requiring a major overhaul of your infrastructure. Your platform should support your growth, not hinder it, providing a centralized way to manage security across an expanding attack surface.
A powerful platform is useless if your team finds it too complicated to use. The user interface should be intuitive, with clear dashboards and straightforward workflows that don’t require a Ph.D. to understand. A smooth implementation process, backed by solid documentation and responsive customer support, is just as important. The right tool should reduce your team’s workload and stress levels, not add to them. Look for a platform that simplifies complex data into actionable insights, allowing your team to focus on what matters most instead of getting bogged down in the tool itself.
No security tool operates in a silo. A modern enterprise security platform must be a team player, integrating smoothly with the other tools in your security stack. Check for out-of-the-box integrations with your existing SIEM, SOAR, ticketing systems, and endpoint solutions. A robust API is also essential for building custom connections and ensuring data can flow freely between systems. The goal is to create a cohesive security ecosystem that provides a unified view of your risk exposure, breaking down data silos and enabling faster, more informed decision-making across the board.
Choosing a new enterprise security platform is a huge step, but let’s be honest—the real work starts when you try to integrate it into your daily operations. Even the most powerful platform can fall flat if the implementation process isn’t handled with care. It’s easy to get tripped up by a few common, but significant, challenges that can derail your progress before you even see the benefits.
The good news is that these hurdles are not insurmountable. With a bit of foresight, you can plan for them and create a much smoother transition for your team. Most implementation issues fall into three main categories: technology gaps, people problems, and resource constraints. You might be struggling to see your entire network, facing resistance from a team that’s already stretched thin, or finding it hard to prove the platform’s value to leadership. Recognizing these potential roadblocks is the first step to clearing them and making sure your new security investment pays off.
You can’t protect what you can’t see, and in today’s sprawling digital environments, seeing everything is a real challenge. Your attack surface isn’t just what’s inside your office walls anymore; it includes cloud instances, remote employee laptops, and IoT devices. This expansion often creates significant visibility gaps, leaving you blind to potential threats. Many organizations simply lack the unified view needed to identify all their assets and the risks associated with them.
The key is to adopt a platform that provides comprehensive total attack surface management. Look for a solution that continuously discovers and maps every asset across your entire environment, from on-prem servers to multi-cloud deployments. This creates a single, reliable inventory, eliminating the blind spots that attackers love to exploit and giving your team a complete picture of your security posture.
Let’s talk about the human side of security. The cybersecurity skills gap is a persistent issue, and your team is likely already juggling multiple responsibilities. Introducing a complex new platform can feel more like a burden than a benefit if it has a steep learning curve. At the same time, you might face resistance from team members who are comfortable with their current tools, even if those tools are creating silos and inefficiencies.
To get everyone on board, focus on platforms that prioritize ease of use and automation. A tool that simplifies workflows and automates routine tasks frees up your analysts to focus on more strategic initiatives. Also, invest time in training and clear communication. Show your team how the new platform makes their jobs easier, not harder. Demonstrating quick wins can help break down resistance and encourage collaboration between security, IT, and DevOps teams.
Securing budget for a new platform often requires framing cybersecurity as a strategic investment rather than a cost center. Leadership wants to see a return on that investment, but proving the value of a security tool can be tricky, especially if you can’t measure its effectiveness. Without clear metrics, you’ll struggle to show that your security posture is actually improving.
Before you implement anything, define what success looks like. Establish clear key performance indicators (KPIs), such as your mean time to detect (MTTD) and mean time to remediate (MTTR). A strong platform will offer robust dashboards and reporting that make it easy to track these metrics. This data-driven approach helps you demonstrate tangible risk reduction and justify your budget by focusing on vulnerability and threat prioritization that directly impacts the business.
A modern enterprise security platform is more than just a collection of defensive tools; it’s an intelligence-driven operation. Threat intelligence is the critical context that transforms your security program from a reactive, alert-chasing function into a proactive, threat-hunting machine. It’s about understanding your adversaries—their motives, their tools, and their targets—so you can build a defense that anticipates their next move. Without it, you’re essentially trying to find your way in the dark. By integrating threat intelligence, you can focus your resources, prioritize your actions, and make smarter, faster decisions to protect your organization.
For too long, security teams have been stuck in a reactive loop, responding to alerts after an incident has already occurred. This approach is no longer sustainable as digital transformation expands the attack surface. A proactive stance means using intelligence to understand threats before they hit your network. Instead of waiting for a vulnerability to be exploited, you can use proactive threat advisories to learn which threat actors are targeting your industry and what techniques they’re using. This allows you to harden your defenses, patch relevant systems, and train your team on the specific threats you’re most likely to face, effectively getting ahead of the attack cycle.
If you’ve ever stared at a vulnerability scan report with thousands of “critical” findings, you know that patching everything is impossible. Limited budgets and resources mean you have to make tough choices. Threat intelligence helps you cut through the noise and focus on what actually matters. It answers the crucial question: “Of these thousands of vulnerabilities, which ones are attackers actually using right now?” By correlating vulnerability data with active threat campaigns, you can prioritize vulnerabilities that pose a clear and present danger to your organization. This ensures your team’s effort is spent on mitigating the most significant risks, not just the ones with the highest CVSS score.
A CVSS score is a theoretical measure of severity, but it doesn’t reflect real-world risk. A vulnerability with a 9.8 score might be difficult to exploit, while one with a 7.5 could have readily available exploit code being used by ransomware gangs. This is where threat intelligence provides essential context. By enriching vulnerability data with real-world data on exploitability, threat actor activity, and malware associations, you can make much more accurate decisions. This data-driven approach allows you to move beyond static scores and prioritize based on the actual, observable threat landscape, ensuring your remediation efforts have the greatest possible impact on your security posture.
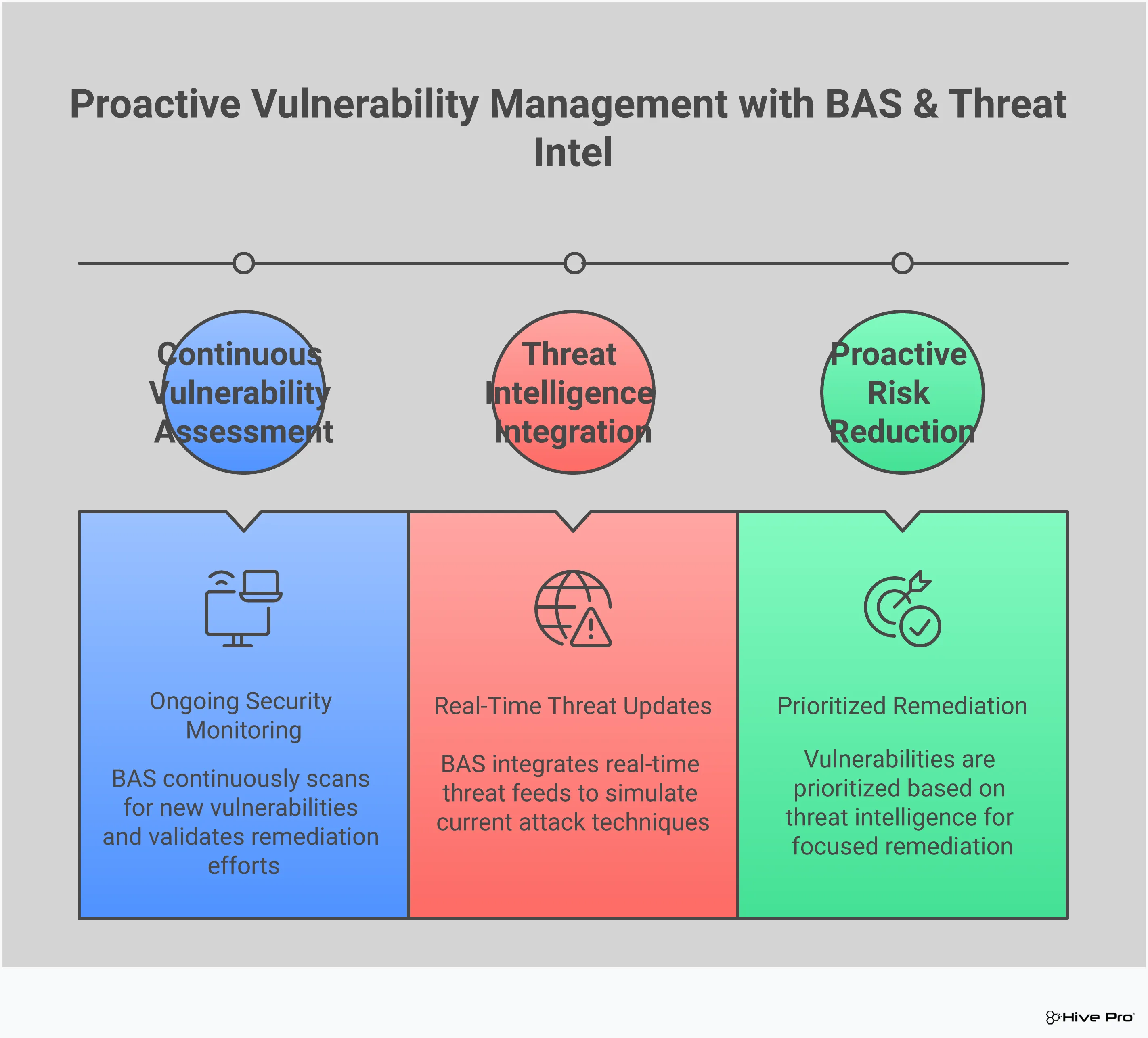
Many security teams operate in silos, with different tools generating different data streams that never intersect. To get a complete picture of your risk, you need to combine external threat intelligence with your own internal security data. External feeds tell you about global campaigns, new malware strains, and emerging threat actors. Internal data from your logs, endpoints, and network traffic tells you what’s happening inside your environment. A platform that enables continuous threat exposure management fuses these two views. This allows you to see if a global threat is targeting your specific assets, turning abstract intelligence into actionable security insights for your team.
Think of all the security tools you have in place. Firewalls, endpoint detection, email filters—the list goes on. But how do you know they’re actually working? Not just turned on, but configured correctly and ready to stop a real attack? That’s where Breach and Attack Simulation (BAS) comes in. Instead of waiting for an incident to test your defenses, BAS platforms let you safely and continuously simulate real-world attack techniques inside your own environment. It’s like having a dedicated red team on call 24/7, constantly checking for weaknesses and giving you a clear picture of your security posture. This shifts your strategy from hoping your defenses hold up to knowing exactly where they stand. By running these controlled attacks, you can see precisely how your security controls respond, identify where your blind spots are, and get the evidence you need to fix them—all without impacting your production systems. It’s about moving from a reactive stance, where you’re always one step behind, to a proactive one where you’re actively hunting for and closing gaps. This continuous feedback loop helps you optimize your security investments, train your team, and build a more resilient defense against the threats you’re most likely to face.
Setting up security controls is one thing; ensuring they remain effective is another challenge entirely. Configurations can drift, new assets can come online without proper protection, and attackers constantly find new ways to bypass defenses. BAS tools provide the continuous validation needed to keep up. By running automated, safe simulations of the latest threats, you can verify that your security stack is performing as expected. This process of adversarial exposure validation helps you confirm that your firewalls are blocking malicious traffic and your EDR is catching suspicious behavior, turning your security program into a fine-tuned, evidence-based operation.
The best time to find a vulnerability is before an attacker does. BAS allows you to adopt a proactive mindset by systematically testing your environment from an adversary’s perspective. These platforms run simulations based on frameworks like MITRE ATT&CK to mimic the exact tactics, techniques, and procedures (TTPs) used by threat actors. This approach helps you uncover hidden attack paths, misconfigurations, and other security gaps that might otherwise go unnoticed until it’s too late. It’s essentially a fire drill for your digital infrastructure, letting you find and fix the weak points in a controlled manner, long before they can be exploited in a real breach.
Gut feelings don’t hold up in the boardroom. To make informed decisions and justify security investments, you need hard data. BAS platforms deliver exactly that, providing clear, actionable metrics on your security performance. Instead of just a pass/fail result, you get detailed reports showing which attacks were blocked, which succeeded, and why. This data-driven approach allows you to measure the effectiveness of your security posture over time, prioritize remediation efforts based on real risk, and demonstrate the value of your security program to leadership. It replaces guesswork with concrete evidence, helping you focus your resources where they’ll have the greatest impact.
A solid incident response (IR) plan is critical, but it’s only as good as your team’s ability to execute it under pressure. BAS provides a perfect training ground for your security team. You can use attack simulations to trigger alerts and walk your team through their response playbooks in a realistic but controlled environment. This helps identify gaps in your processes, improve communication, and reduce response times. Regular drills ensure that when a real incident occurs, your team isn’t scrambling to figure out what to do. They’ll have the muscle memory and confidence to respond effectively, minimizing damage and accelerating recovery.
The world of enterprise security doesn’t stand still, and neither do the platforms designed to protect it. As organizations embrace new technologies and attackers refine their methods, security platforms are evolving from siloed tools into intelligent, integrated systems. The future isn’t just about building higher walls; it’s about gaining smarter visibility, acting faster, and adopting a more proactive mindset. Four key trends are shaping the next generation of enterprise security, pushing us toward a more resilient and adaptive way of managing risk. We’re seeing a move away from reactive, alert-driven security toward proactive strategies that anticipate threats. This involves breaking down the data silos that have long plagued security teams and using automation to handle the noise so experts can focus on what matters. These shifts are redefining what it means to be secure, moving the goalposts from simple prevention to continuous validation and exposure management. Understanding these trends is key to choosing a platform that won’t just solve today’s problems, but will also grow with you to meet tomorrow’s challenges.
The old “trust but verify” model of network security is officially a thing of the past. The future is Zero Trust, a security framework built on the principle of “never trust, always verify.” This approach assumes that threats can exist both outside and inside the network, so it requires strict identity verification for every person and device trying to access resources. Implementing a Zero Trust strategy isn’t about buying a single product; it’s a fundamental shift in how you approach security. Modern enterprise platforms are being built to support this model, enabling things like microsegmentation to isolate workloads and enforce granular access policies, ensuring that even if one area is compromised, the breach is contained.
For years, security teams have been stuck in a reactive cycle of patching known vulnerabilities. Continuous Threat Exposure Management (CTEM) flips that script. It’s a proactive approach that helps you see your organization through an attacker’s eyes. Instead of just scanning for vulnerabilities, a CTEM program helps you continuously discover your entire attack surface, prioritize exposures based on real-world threats, and validate your defenses. This shift is happening because organizations are struggling with siloed tools, a lack of threat intelligence, and an attack surface that grows every day. Platforms that unify these functions are becoming essential for getting ahead of threats instead of just reacting to them.
As businesses move more operations to the cloud, security tools built for on-premise environments just can’t keep up. The future is in cloud-native security solutions that offer scalable, centralized management without sacrificing performance. Alongside this shift, Extended Detection and Response (XDR) is gaining ground. XDR breaks down the silos between security tools by collecting and correlating data from endpoints, cloud workloads, email, and networks. This gives security teams a unified view of an attack chain, allowing them to trace a threat’s path and respond more effectively. The next generation of enterprise platforms will have XDR capabilities built-in, providing deeper visibility across hybrid environments.
Security teams are drowning in data and alerts. There’s simply no way for humans to manually analyze every potential threat. This is where artificial intelligence and automation come in. AI is becoming critical for identifying subtle patterns and anomalies that signal a sophisticated attack, while automation handles the repetitive, time-consuming tasks that burn out analysts. By using AI in cybersecurity, platforms can automatically triage alerts, orchestrate incident response actions, and provide clear metrics on security effectiveness. This allows your team to focus their expertise on the most critical threats, making your entire security operation more efficient and effective.
You’ve seen the top contenders, but how do you cut through the marketing noise and figure out which platform will actually work for your team? It’s not just about the feature list. A truly effective platform should make your security operations smoother, smarter, and more proactive. When you’re doing demos and comparing options, focus on these four key areas to gauge a platform’s real-world performance and its potential impact on your security posture.
A platform’s real power comes from how well its features work together. Juggling a dozen different point solutions creates visibility gaps and slows down your response time. Look for a platform that consolidates essential tools into a single interface. This centralized management approach simplifies everything from threat detection to incident response. Automation is the other half of the equation. An effective platform should automate routine tasks, like correlating alerts and enriching data, so your team can stop chasing ghosts and focus on investigating and resolving genuine threats. The goal is to find a solution that acts as a true force multiplier for your team.
You can’t protect what you can’t see. A modern security platform must provide a complete and continuous view of your entire digital footprint—across on-premises servers, cloud environments, and all connected devices. This comprehensive visibility is the foundation of effective risk management. Without it, you’re making decisions with incomplete information. The right platform will help you discover your full attack surface and understand how different assets are interconnected. This allows you to move beyond simply managing vulnerabilities and start managing your actual exposure to threats, focusing your resources where they’ll have the greatest impact.
Alert fatigue is a real problem that burns out security teams and leads to missed threats. The best platforms prioritize quality over quantity when it comes to alerts. Instead of flooding your team with low-context notifications, they use advanced analytics and risk-based alerting to surface the most critical issues. When evaluating a platform, ask about its false positive rate and how it helps you prioritize threats. A platform with high-fidelity scanning and intelligent alerting can drastically reduce noise, allowing your team to confidently focus on the alerts that truly matter and respond faster to credible threats.
Meeting industry regulations like HIPAA or GDPR is non-negotiable, and your security platform should make this easier, not harder. Look for solutions with built-in compliance reporting and dashboards that help you demonstrate due diligence to auditors. But features are only part of the story. Consider the vendor behind the platform. Do they offer robust support, clear documentation, and a partnership approach to your success? A strong vendor relationship is crucial for smooth implementation and for getting the most value out of your investment over the long term. They should help you establish the right metrics to measure your program’s effectiveness.
Choosing a new security platform can feel like a massive undertaking, but breaking it down into manageable steps makes all the difference. It’s not just about picking the one with the most features; it’s about finding the right partner for your team’s specific needs and goals. A platform should simplify your workflow, not complicate it. By focusing on a few key areas—your current capabilities, integration needs, future growth, and a clear comparison method—you can confidently select a solution that will strengthen your security posture for years to come.
Before you even look at a demo, take an honest look at your current security program. What are you doing well? Where are the gaps? Document your existing tools, your team’s skill set, and your current processes for vulnerability management and incident response. This self-assessment gives you a baseline. It helps you understand if you need a platform to fill specific gaps or one that can overhaul your entire process. Knowing where you stand helps you define your requirements clearly, so you can find a platform that meets you where you are and helps you grow.
Your new security platform shouldn’t live on an island. It needs to play well with the tools you already use every day. Think about your SIEM, SOAR, ticketing systems, and cloud environments. A platform with robust API and integration capabilities is non-negotiable because it allows you to centralize data and automate workflows across your entire stack. Without seamless integration, you’re just creating more data silos and manual work for your team. Look for platforms that offer pre-built connectors for popular tools, as this can drastically simplify the implementation process and give you a unified view of your security posture from day one.
The security platform you choose today needs to be able to handle the challenges of tomorrow. Your organization is going to grow, your attack surface will expand, and attackers will find new ways to get in. Can the platform scale to accommodate more assets, users, and data without a drop in performance? Look for a vendor that demonstrates a commitment to innovation and is actively researching emerging threats. A platform that can adapt to your evolving needs will provide long-term value, saving you the headache of another migration in just a few years.
When you start comparing platforms, demos can be dazzling but also misleading. To make an objective choice, create a vendor scorecard. This is a simple document where you list your must-have criteria and rate each vendor against them. Include categories like security coverage, ease of use, integration capabilities, and the quality of customer support. Don’t forget to factor in the total cost of ownership (TCO), not just the sticker price. Using a vendor evaluation framework helps you cut through the marketing noise and focus on what truly matters for your team, ensuring your final decision is based on data, not just a gut feeling.
We already have a lot of security tools. Won’t adding a platform just create more work for my team? That’s a fair question, but the goal of a true platform is actually the opposite—it’s about simplification. Instead of your team logging into multiple, disconnected tools to piece together information, a platform brings everything into a single command center. This consolidation breaks down the information silos that cause so much manual work and helps automate the process of connecting the dots, freeing up your team to focus on genuine threats rather than just managing software.
How does a platform actually help reduce alert fatigue instead of just adding more alerts? A smart platform doesn’t just generate more noise; it adds context. By pulling in data from across your entire environment and enriching it with up-to-date threat intelligence, it helps you distinguish a real threat from low-level background activity. This means your team sees fewer, higher-quality alerts that are prioritized based on actual risk to your business, allowing them to focus their energy on the incidents that truly matter.
What’s the difference between traditional vulnerability management and the Continuous Threat Exposure Management (CTEM) approach you mentioned? Traditional vulnerability management often leaves you with a massive list of potential issues based on theoretical scores, forcing you to guess what to fix first. CTEM is a more strategic and proactive approach. It helps you see your organization from an attacker’s perspective by continuously mapping your attack surface, prioritizing the vulnerabilities that are actively being exploited in the wild, and validating that your security controls are working as expected. This helps you focus on reducing your real-world exposure.
Is Breach and Attack Simulation (BAS) really necessary if we already do regular vulnerability scanning? Yes, it’s a crucial next step. Vulnerability scanning tells you where your theoretical weaknesses are, but BAS tells you if those weaknesses can actually be exploited in your specific environment. It safely simulates real attack techniques to test if your security controls—like your firewall or endpoint protection—are configured correctly and would actually stop an intruder. It’s the difference between knowing you have a weak lock and knowing if someone can actually pick it.
What’s the most important first step to take when considering a move to a security platform? The best first step is to perform an honest assessment of your current security program. Before you start looking at vendors, map out the tools you currently use, identify your biggest visibility gaps, and understand your team’s daily workflow. This internal audit gives you a clear picture of your actual needs, which will help you create a scorecard to evaluate platforms based on what will solve your specific problems, not just on a flashy demo.