Comprehensive Threat Exposure Management Platform
Your organization’s assets are everywhere: on-premise servers, multi-cloud environments, remote endpoints, and countless applications. Trying to secure this sprawling digital footprint with siloed tools gives you a fragmented, incomplete picture of your risk. You might have one tool for cloud misconfigurations and another for network vulnerabilities, but no single source of truth. A powerful cybersecurity assessment tool unifies this view. By consolidating data from across your entire attack surface into a single platform, it gives you the clarity needed to see how different risks connect, helping you make smarter, more holistic decisions about where to focus your remediation efforts.
Think of a cybersecurity assessment tool as your digital detective. At its core, it’s a piece of software designed to help your organization identify its vulnerabilities, threats, and risks. Instead of manually searching for weaknesses across your entire network, these tools automate the process, giving you a clear picture of your security posture. They scan your systems, applications, and networks to find gaps that attackers could exploit.
The goal isn’t just to find problems but to understand them in context. A powerful assessment tool provides a unified view of cyber risks in one place, helping you move from simply managing vulnerabilities to proactively reducing your overall exposure. It’s about getting ahead of threats before they can cause damage.
The best cybersecurity assessment tools operate on a simple but effective cycle: check, fix, and maintain. First, they continuously scan and assess your company’s security controls and digital assets to find existing weaknesses. This gives you a real-time inventory of your vulnerabilities across your entire attack surface.
Next, they help you deal with those threats. This isn’t just a long list of problems; modern tools help you prioritize which risks to tackle first based on their potential impact. Finally, by providing clear documentation and evidence of your security posture, these tools make it easier to meet compliance requirements and even get better cyber insurance rates. It’s a continuous loop that keeps your defenses sharp.
A one-and-done security check just doesn’t cut it anymore. The threat landscape is constantly evolving, with new vulnerabilities and attack methods appearing all the time. That’s why regular cybersecurity assessments are essential for protecting your business. An assessment tool automates this process, making continuous monitoring feasible.
Without one, you’re essentially flying blind, unaware of the gaps in your defenses. These tools provide the visibility you need to manage your total attack surface, from on-premise servers to cloud assets and remote endpoints. They turn security from a reactive guessing game into a proactive, data-driven strategy, ensuring you can adapt as new threats emerge.
Implementing a cybersecurity assessment tool is a direct investment in your organization’s resilience. By using the right tool, you can better protect sensitive information, maintain customer trust, and avoid the massive financial and reputational costs of a data breach. It’s about shifting from crisis management to proactive risk reduction.
The return on investment becomes clear when you consider the cost of inaction. Fixing problems early prevents expensive attacks, operational downtime, and potential regulatory fines. By focusing your team’s efforts on the most critical threats, you optimize your security resources, ensuring that your time and budget are spent protecting the assets that matter most to your business.
Think of cybersecurity assessment tools as your security team’s specialized toolkit. Just as a carpenter needs more than just a hammer, your team needs a variety of tools to build a strong defense. Each type of tool is designed to inspect a different part of your digital environment, from your sprawling network and custom applications to your cloud infrastructure. They work together to help you find weak spots, identify potential threats, and understand your overall risk profile.
The goal is to move from a reactive stance—fixing things after they break—to a proactive one where you can find and fix vulnerabilities before an attacker exploits them. Using a combination of these tools gives you a comprehensive view of your entire attack surface, making it easier to prioritize what needs fixing first. This is essential for meeting compliance requirements like SOC2, getting cyber insurance, and clearly communicating your security efforts to company leadership. Let’s look at the main categories you’ll encounter.
Vulnerability scanners are the foundation of any solid security program. These tools automatically scan your systems, applications, and networks for known security weaknesses. Think of them as a security checklist for your digital assets, flagging everything from outdated software and missing patches to common misconfigurations. They help you find the low-hanging fruit that attackers often target first. By running regular scans, you can maintain a continuous inventory of your vulnerabilities and get a clear picture of your overall risk. This information is crucial for showing auditors and executives that you are actively managing your security posture.
While vulnerability scanners look for known flaws, network security tools watch what’s happening on your network in real time. These tools monitor the flow of data in and out of your organization, looking for suspicious activity that could signal an attack. This category includes firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems. They are your first line of defense, helping you spot and block threats before they can cause damage. By analyzing network traffic patterns, these tools help you strengthen your security controls and react faster when a potential incident occurs, making your entire environment more resilient.
Your applications are often the front door for attackers, which is why Application Security Testing (AST) is so important. These tools are designed to find security flaws directly within your software, whether it’s custom-built or off-the-shelf. Some tools analyze source code before it’s compiled (SAST), while others test the application while it’s running (DAST). A key part of AST is penetration testing, which is essentially a controlled “ethical hack” where security pros simulate a real attack to see how your application’s defenses hold up. Integrating AST into your development process helps you catch and fix security bugs early, saving time and reducing risk.
As more organizations move to the cloud, securing those environments has become a top priority. Cloud security assessment tools are specifically designed to handle the unique challenges of platforms like AWS, Azure, and Google Cloud. With so many data breaches originating from misconfigured cloud assets, these tools are essential for keeping your information safe. They continuously scan your cloud infrastructure for security risks like public-facing storage buckets, overly permissive access rights, and compliance violations. A good tool gives you a single, unified view of risks across your entire attack surface, from on-premise servers to multi-cloud deployments.
Inconsistent security settings across your devices and servers can create dangerous gaps for attackers to slip through. Configuration management tools help you avoid this by enforcing a secure, standardized baseline for all your systems. These tools automate the process of setting up and maintaining servers, workstations, and other network devices according to your security policies. They ensure that every new asset is deployed correctly and that existing ones don’t drift from their secure state over time. This not only strengthens your security but also simplifies compliance by providing a clear audit trail of your system configurations.
Choosing the right cybersecurity assessment tool can feel overwhelming, but it boils down to finding a solution that gives you clarity and control. The best tools don’t just spit out data; they provide actionable insights that fit into your existing workflow. As you evaluate your options, look for a platform that moves you from a reactive stance to a proactive one. The goal is to find and fix your most critical exposures before an attacker can exploit them. Focus on features that automate tedious work, provide clear context, and help you prioritize your team’s efforts where they’ll have the most impact. A modern security program needs a tool that can see everything, from your cloud environments to your on-premise infrastructure, and make sense of it all.
This means looking beyond basic vulnerability scanning. You need a comprehensive platform that unifies your view of cyber risk and helps you answer the most important questions: What are our most critical assets? Which vulnerabilities are actually exploitable? And what should we fix first? The right tool empowers your team by cutting through the noise of endless alerts and highlighting the genuine threats that require immediate attention. By investing in a solution with the right features, you’re not just buying software; you’re building a more resilient and efficient security operation. A unified exposure management platform can transform your approach, helping you move from guessing what to fix to knowing with confidence.
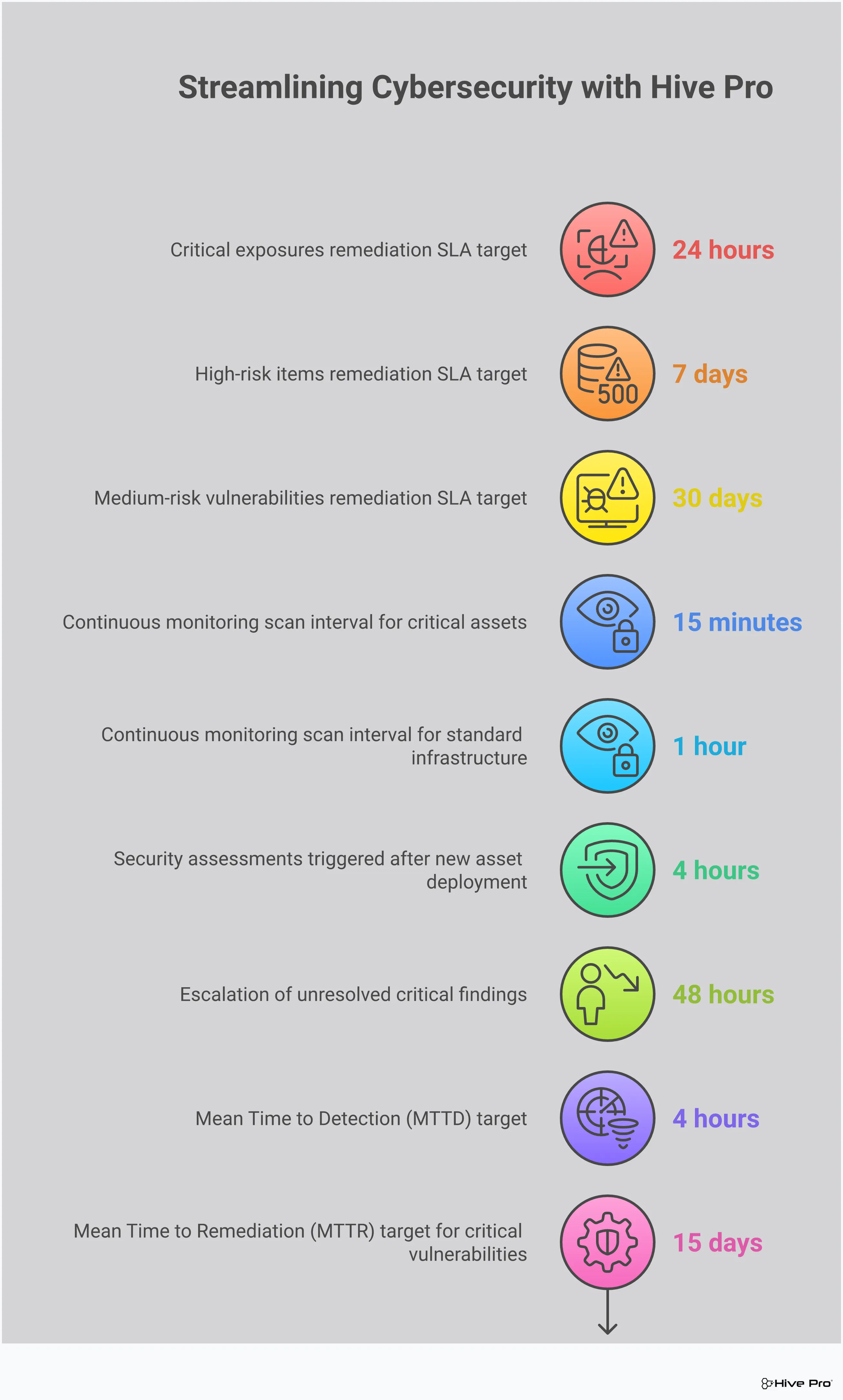
Your attack surface is constantly changing, and manual assessments just can’t keep up. That’s why automated, continuous scanning is a must-have feature. A good tool will constantly monitor your entire environment—from on-premise servers to cloud assets and web applications—to identify new and emerging vulnerabilities in real time. This proactive approach helps you find and fix security gaps before they can be exploited by attackers. By automating the discovery process, you free up your team to focus on strategic remediation instead of getting bogged down in manual checks. This is the foundation of a modern total attack surface management program that provides complete visibility.
Raw data is useless without context. Look for a tool that offers customizable, in-depth reporting and intuitive dashboards. You should be able to easily visualize your security posture, track remediation progress, and drill down into specific vulnerabilities. Great tools allow you to create different reports for different audiences—a high-level executive summary for the CISO and a detailed technical report for the security operations team. A platform that presents all this information in a single, clear interface is essential for making informed decisions quickly and communicating risk effectively across the organization. This clarity helps you demonstrate the value of your security efforts to leadership.
A new security tool should be a team player, not another silo. Seamless integration with your existing tech stack is critical for a smooth workflow and a holistic view of your security posture. Your assessment tool should connect easily with your SIEM, SOAR, ticketing systems (like Jira or ServiceNow), and other security solutions. This ensures that vulnerability data flows where it needs to, alerts are managed efficiently, and remediation tasks are assigned and tracked automatically. When your tools work together, your team can operate more efficiently, break down data silos, and respond to threats much faster.
Meeting regulatory and industry standards is a major driver for cybersecurity assessments. A top-tier tool will help you streamline this process by mapping identified vulnerabilities directly to specific compliance frameworks like NIST, ISO 27001, SOC2, or GDPR. This feature makes it much easier to demonstrate due diligence to auditors, stakeholders, and even cyber insurance providers. Instead of manually cross-referencing spreadsheets, you can generate compliance reports with a few clicks. This saves your team countless hours of administrative work and ensures you can consistently maintain and prove a strong compliance posture.
With thousands of potential vulnerabilities, you need a way to focus on what truly matters. Generic CVSS scores aren’t enough because they lack business context and real-world threat data. Look for a tool that provides accurate risk scoring based on more than just severity. An advanced solution will incorporate real-time threat intelligence, asset criticality, and exploitability data to help you with vulnerability and threat prioritization. This allows your team to address the exposures that pose the greatest actual risk to your organization first, ensuring your limited resources are used as effectively as possible.
With so many assessment tools on the market, finding the right one can feel overwhelming. The best choice for your organization will depend on your specific needs, existing tech stack, and overall security goals. Some tools excel at vulnerability scanning, while others offer a more holistic view of your threat exposure. To help you get started, I’ve broken down five leading solutions that security teams rely on to strengthen their defenses and stay ahead of threats. Each one brings a different approach to the table, so think about which features align most closely with your program’s maturity and objectives.
The Hive Pro Uni5 Xposure Platform is designed to move security programs from a reactive to a proactive stance. It operates as a comprehensive Continuous Threat Exposure Management (CTEM) solution, giving you a single, unified view of your cyber risks. Instead of just identifying vulnerabilities, it continuously scans your entire attack surface—from on-premise to cloud environments—to find potential exposures. What really sets it apart is the integration of threat intelligence from its in-house HiveForce Labs, which helps you prioritize the threats that pose an imminent risk to your business. This focus on proactive exposure reduction helps teams concentrate their efforts on what matters most.
Tenable is a well-known name in the vulnerability management space, and for good reason. Its platform is built to handle the modern attack surface, including IT, cloud, and OT environments. According to SentinelOne, “Tenable Vulnerability Management continuously scans for weak spots in your IT systems and helps you decide which ones to fix first.” This is crucial for teams that are often flooded with alerts. By providing clear risk-based prioritization, Tenable helps you cut through the noise and focus remediation efforts on the vulnerabilities that attackers are most likely to exploit, making your response efforts more efficient and effective.
Qualys VMDR (Vulnerability Management, Detection, and Response) offers an all-in-one, cloud-based solution. It streamlines the entire security assessment lifecycle into a single application, which can simplify workflows for your team. The platform “is a cloud-based tool that constantly scans for weak spots, helps update software, and keeps track of all your devices,” as noted by cybersecurity experts. This integrated approach means you can discover assets, detect vulnerabilities, prioritize threats, and confirm remediation without having to switch between different tools. Its cloud-native architecture also makes it highly scalable for growing organizations.
Rapid7’s InsightVM is another powerful tool focused on providing real-time visibility into your risk landscape. It goes beyond simple scanning by collecting data from across your network and correlating it with threat intelligence to give you a live view of your security posture. As SentinelOne highlights, “Rapid7 InsightVM continuously monitors for weak spots and assesses risks in real-time, helping you prioritize and track fixes.” The platform includes features like remediation project tracking and easy-to-understand dashboards, which help security teams collaborate with IT and DevOps to close security gaps faster.
While often recognized for its endpoint protection, the CrowdStrike Falcon Platform also offers robust assessment capabilities, particularly through its threat intelligence offerings. It’s designed to help you think like an attacker. The platform’s “CrowdStrike Falcon Intelligence Premium provides detailed information about threats and helps understand attackers to prevent future incidents.” This focus on adversary tactics and motivations gives you the context needed to not only fix current vulnerabilities but also to anticipate and defend against future attacks. It’s a great option for mature security teams looking to build a truly intelligence-led defense strategy.
Picking the right cybersecurity assessment tool is a great first step, but how you introduce it into your workflow is what truly determines its success. A thoughtful implementation plan ensures the tool becomes an integral part of your security program rather than just another piece of software gathering dust. It’s about moving from simply owning the technology to actively using it to reduce your organization’s exposure. A successful rollout requires a clear strategy, a well-defined deployment process, and a plan for integrating the tool into your existing security ecosystem. By taking the time to plan your approach, you can avoid common pitfalls and start seeing a return on your investment much faster.
First things first, you need a strategy. A one-time scan isn’t going to cut it in a world where new threats appear daily. Your approach to cybersecurity assessments should be continuous, creating a cycle of scanning, analyzing, and remediating. Think of it as an ongoing conversation with your security posture, not a single announcement. This means scheduling regular assessments to keep up with evolving threats and changes in your own environment. A solid strategy outlines how often you’ll run assessments, what you’ll be looking for, and how you’ll use the results to make meaningful security improvements over time.
Not all assessment tools are created equal, and the best one for you depends on your specific needs. When evaluating your options, consider factors like scalability—will it grow with your organization? Also, think about usability and automation. A tool that’s difficult to use or requires constant manual intervention will quickly become a burden. Look for a solution that offers comprehensive coverage of your assets, from on-premise servers to cloud environments. Make sure it integrates with your existing security stack and provides clear, actionable reporting that helps you prioritize what matters most.
Once you’ve selected a tool, map out a clear deployment plan. Start by setting specific goals. Are you trying to meet compliance requirements, reduce the risk of a breach, or get a better handle on your attack surface? Next, define the scope of your initial rollout. You might start with a single critical system or department before expanding across the entire organization. Assign clear roles and responsibilities so everyone knows who is in charge of configuring the tool, running scans, and acting on the findings. A phased approach helps you work out any kinks and build momentum for a successful company-wide implementation.
Let’s be real—implementing a new security tool can come with challenges. Many organizations already feel overwhelmed by the number of tools they manage, a problem often called “tool saturation.” You might also face integration issues with your existing systems, a shortage of skilled team members to manage the new platform, or a flood of false alerts that create more noise than signal. The key is to anticipate these hurdles. Before you begin, identify potential roadblocks and create a plan to address them. This could involve dedicating specific training time for your team or running a pilot program to fine-tune configurations and reduce false positives.
For an assessment tool to be truly effective, it needs to play well with others. It shouldn’t operate in a silo. Look for a tool that offers seamless integration with your existing technology, such as your SIEM, ticketing systems, and other security platforms. This creates a more unified and efficient workflow, allowing you to automate processes and reduce manual work for your team. When your assessment tool can share data and insights with your other systems, you get a more complete picture of your security posture and can respond to threats much more quickly.
Cybersecurity assessment tools give you the data, but frameworks provide the roadmap. Think of them as the strategic blueprints that help you structure your assessments, prioritize actions, and communicate risk effectively across your organization. Instead of guessing what to focus on, these established frameworks offer a systematic approach grounded in industry best practices. They provide a common language for your team and help translate technical findings into business impact, which is crucial for getting buy-in from leadership. While each framework has a different focus, they aren’t mutually exclusive. Many organizations find success by blending elements from multiple frameworks to create a security program that’s tailored to their specific needs, industry, and risk appetite.
If you’re looking for a way to align your security efforts with your business objectives, the NIST Cybersecurity Framework (CSF) is an excellent starting point. The NIST Cybersecurity Framework is a flexible framework that helps organizations manage cyber risks and connects security efforts to business goals. It’s built around five core functions: Identify, Protect, Detect, Respond, and Recover. This structure provides a high-level, strategic view of your cybersecurity risk management lifecycle. Because it focuses on continuous improvement, it allows organizations to adapt their cybersecurity strategies as threats evolve, making it a durable and widely adopted guide for businesses of all sizes.
For organizations operating on a global scale or those needing to demonstrate a formal commitment to security, ISO 27001 is the go-to standard. ISO 27001 is an international standard that outlines the requirements for an information security management system (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. Unlike more flexible frameworks, ISO 27001 is designed for certification. Achieving this certification can be a powerful way to build trust with customers and partners by formally verifying that your security practices meet a rigorous international benchmark.
When you need to know exactly where to start, the CIS Controls offer clear, actionable guidance. The Center for Internet Security (CIS) Controls are practical steps to reduce cybersecurity risks and can be used with other frameworks. What makes them so effective is their prioritized approach. The controls are broken down into Implementation Groups (IGs), offering a tiered path for organizations to follow based on their resources and risk profile. They provide a prioritized set of actions to protect organizations and improve their security posture, cutting through the noise to focus on the most critical defensive measures first.
While other frameworks focus on building your defenses, the MITRE ATT&CK framework helps you understand your enemy. The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques based on real-world observations. It’s essentially a playbook of how attackers operate, from initial access to final impact. This perspective is invaluable for proactive defense. It helps organizations understand how attackers operate and provides a structured way to assess their defenses against these techniques. Your team can use it for everything from threat intelligence enrichment and security control validation to red team exercises and threat hunting.
Choosing and implementing a cybersecurity assessment tool is a huge step, but the work doesn’t stop there. To truly strengthen your security posture, you need to build solid processes around the tool. Think of it less as a one-time purchase and more as the centerpiece of an ongoing strategy. By creating a consistent routine, empowering your team, and measuring your progress, you can turn your assessment tool from a simple scanner into a powerful engine for continuous improvement. This approach ensures you’re not just identifying risks, but actively reducing your exposure over time.
A one-and-done security scan is like locking your front door but leaving the windows wide open. The threat landscape changes daily, with new vulnerabilities and attack methods emerging all the time. That’s why cybersecurity assessments must be a regular activity, not a one-off event. By establishing a consistent schedule—whether it’s quarterly, monthly, or even weekly—you can stay ahead of potential threats. A platform that offers continuous scanning is even better, as it provides a real-time view of your attack surface. This proactive rhythm helps you move from a reactive fire-drill mentality to a state of constant readiness, making it much harder for attackers to find a foothold.
Your assessment tool is only as effective as the people who use it. Without a knowledgeable team, even the most advanced platform can produce reports that are misinterpreted or ignored. Continuous training is essential for making sure your team understands not only how to operate the tool but also how to interpret its findings within the context of your business. A well-versed team can more effectively prioritize vulnerabilities, validate findings, and coordinate remediation efforts. Investing in your team’s skills ensures you get the maximum return on your technology investment and builds a stronger, more resilient security culture from the inside out.
Effective cybersecurity requires more than just a software budget. To truly manage risk, you need to allocate the right resources, including personnel, time, and funding for remediation. An assessment tool will generate a list of vulnerabilities, but that list is useless if no one is tasked with fixing them. Make sure you have dedicated team members responsible for acting on the tool’s findings and that they have the time and authority to do so. A strong security program requires a holistic approach where tools, processes, and people work together. Proper resource allocation is the fuel that makes this entire system run efficiently.
How do you know if your security efforts are actually working? By tracking key performance metrics (KPIs). Measuring your progress is vital for demonstrating the value of your assessment program and identifying areas for improvement. Focus on actionable metrics like Mean Time to Remediate (MTTR), the number of critical vulnerabilities patched per quarter, or the overall reduction of your attack surface. These KPIs provide concrete evidence of your program’s effectiveness, which is crucial for securing future budgets and gaining executive buy-in. Dashboards and in-depth reports from your assessment tool can make tracking these metrics much simpler, turning raw data into a clear story of progress.
The ultimate goal is to create a self-reinforcing cycle of improvement. Each assessment should feed into the next, creating a loop of discovery, prioritization, remediation, and validation. Use the insights from each scan to refine your security controls and processes. Did a certain type of vulnerability reappear? Maybe a development process needs to be updated. This approach, often central to Continuous Threat Exposure Management (CTEM) programs, transforms your security practice from a static checklist into a dynamic, adaptive operation. By embracing continuous improvement, you ensure your organization remains resilient against a constantly evolving array of threats.
The world of cybersecurity doesn’t stand still, and neither do the tools we rely on. As threats become more sophisticated and frequent, our assessment strategies have to evolve right along with them. The future isn’t about working harder; it’s about working smarter with technology that can keep up. Let’s look at the key shifts that are shaping the next generation of cybersecurity assessments and what they mean for your team.
With companies facing a staggering number of cyberattacks each week, it’s impossible for security teams to manually sift through every alert. This is where artificial intelligence and machine learning are becoming indispensable. These technologies excel at analyzing massive datasets to spot patterns and anomalies that would be invisible to the human eye. Instead of drowning in noise, your team can use AI-driven insights to focus on credible threats. This allows for a more proactive stance, using advanced threat intelligence to understand and anticipate attacker behaviors before they result in a breach. It’s about turning data into decisive action.
Automation is the natural next step after leveraging AI for detection. The goal is to streamline your security workflows, cutting down the time between identifying a threat and neutralizing it. By automating routine tasks like patching, configuration updates, and initial incident response, you free up your security professionals to handle more complex, strategic challenges. This isn’t about replacing your team; it’s about empowering them. An effective exposure management platform can automate remediation guidance and integrate with your existing systems, creating a more efficient and less error-prone security process that allows your team to operate at scale.
The cybersecurity landscape is in constant motion, which means our tools must adapt. We’re seeing a clear move away from static, point-in-time assessments toward more dynamic and comprehensive solutions. For example, the FFIEC recently decided to sunset its Cybersecurity Assessment Tool, noting that newer and more complete resources are now available. This industry-wide shift reflects a demand for tools that provide a continuous, unified view of risk across the entire attack surface. The future lies in platforms that can grow with your organization, integrating new technologies and adapting to emerging threats without missing a beat.
Looking ahead, a few key trends stand out. First, cybersecurity assessment tools are no longer considered optional—they are a fundamental requirement for any organization serious about its security posture. Second, there’s a growing emphasis on proactive security. Instead of just reacting to vulnerabilities, leading organizations are focused on continuously reducing their threat exposure. This involves a strategic approach to vulnerability and threat prioritization, ensuring that your team’s limited time and resources are spent on the risks that pose the greatest danger to your business. This move from a reactive to a proactive mindset is the defining characteristic of modern cybersecurity.
What’s the real difference between vulnerability management and threat exposure management? Think of it this way: traditional vulnerability management gives you a long list of problems, like a building inspector handing you a report of every cracked tile and scuffed wall. Threat exposure management, on the other hand, tells you which of those problems could actually lead to a break-in. It connects the dots between a vulnerability, real-world threat intelligence, and your most critical assets to show you your true risk. It’s a strategic shift from just cataloging flaws to actively reducing your chances of being breached.
My team is already overwhelmed with alerts. Won’t a new tool just add to the noise? That’s a common concern, but the right assessment tool should do the exact opposite. A basic scanner might flood you with low-level alerts, but a modern platform is designed to cut through that noise. It uses context—like which vulnerabilities are actively being exploited by attackers and which assets are most critical to your business—to prioritize what needs your immediate attention. The goal isn’t to give you more alerts, but to give you fewer, more meaningful ones that guide you to the most urgent risks.
How often should we actually be running assessments? While a quarterly or monthly scan is better than nothing, the ideal approach is continuous. Your digital environment and the threat landscape change every day, so your security view should be just as dynamic. The best tools offer automated, continuous scanning that provides a real-time picture of your attack surface. This moves you away from infrequent snapshots and toward a constant state of awareness, allowing you to spot and fix new weaknesses as soon as they appear.
Can a single tool really cover our entire attack surface, from on-premise servers to our cloud environments? Yes, and that unified view is one of the most important features to look for. In the past, you might have needed separate tools for your network, your cloud infrastructure, and your applications, which created blind spots and data silos. Modern exposure management platforms are built to provide a single, comprehensive view across your entire hybrid environment. This allows you to see how risks in one area might impact another and manage your security posture from one central place.
How do I justify the cost of a comprehensive assessment tool to my leadership? Frame the conversation around business risk, not just technical features. The cost of a powerful assessment tool is a fraction of the potential cost of a data breach, which includes financial loss, reputational damage, and operational downtime. Explain that the tool provides a clear return on investment by focusing your team’s limited resources on the most critical threats, preventing expensive incidents before they happen. It also streamlines compliance reporting and provides the concrete data needed to show that the company is actively managing its cyber risk.