Comprehensive Threat Exposure Management Platform
Security teams are drowning in data but starving for insight. You have logs, network traffic, and endpoint activity pouring in from all directions, but more data doesn’t automatically equal better security. Without context, it’s just noise that leads to alert fatigue and missed threats. An effective security program needs a way to filter that noise and focus on what truly matters. A continuous threat monitoring platform is designed to do just that. It analyzes the constant stream of information from your environment in real time, enriches it with threat intelligence, and surfaces the actionable alerts that require your team’s immediate attention. This guide explains how to choose a platform that provides clarity, not just more data.
Think of continuous threat monitoring as a security system that’s always on, watching over your entire digital environment. Instead of performing periodic checks that only give you a snapshot in time, this approach provides constant vigilance across your networks, endpoints, and cloud infrastructure. It’s designed to help you spot potential threats the moment they appear, not after they’ve already caused damage.
This represents a fundamental shift from a reactive, “what happened?” mindset to a proactive, “what’s happening right now?” strategy. By maintaining this constant awareness, your security team can identify and address risks before they escalate into full-blown incidents. It’s about giving your team the real-time visibility needed to protect your organization’s critical assets around the clock. This constant oversight is a core component of a modern threat exposure management program, turning security from a periodic task into an ongoing, automated process.
So, how does this constant watch actually happen? Continuous monitoring platforms act as your digital nervous system. They pull in vast amounts of data from all corners of your network—think system logs, network traffic, user activity, and application performance. The system then analyzes this stream of information in real time, looking for anomalies or patterns that match known threats. When it spots something suspicious, it generates an alert. The best tools go a step further by adding context, telling you why an alert matters. For instance, they can highlight if a vulnerability affects a critical business system, helping your team prioritize its response and act quickly on the most significant threats.
Simply put, you need continuous monitoring because threats don’t operate on a 9-to-5 schedule. A proactive and constant watch is the only way to detect and respond to attacks before they do real harm. By identifying threats in real time, you drastically shorten the window an attacker has to operate within your network. This leads to a much faster and more effective incident response, minimizing potential damage and disruption. Beyond just fighting active threats, continuous monitoring is also essential for maintaining compliance with industry regulations, which often require proof of ongoing security checks. It gives you the visibility you need to stay secure and compliant.
Choosing a continuous threat monitoring platform isn’t just about adding another tool to your stack; it’s about finding a partner that can keep up with the evolving threat landscape. The right platform gives you clarity and control, helping your team move from a reactive stance to a proactive one. As you evaluate your options, focus on core capabilities that directly address the biggest security challenges: speed, automation, visibility, integration, and intelligence. These five pillars are the foundation of an effective monitoring strategy and should be non-negotiable features in any solution you consider.
Threats don’t wait for your weekly security scan to finish. An effective monitoring platform must provide real-time threat detection to spot malicious activity the moment it occurs. This means your security team gets immediate alerts on everything from unusual network traffic to unauthorized access attempts, allowing them to act before a minor issue becomes a major breach. Lag time is the enemy in cybersecurity; a delay of even a few minutes can be all an attacker needs. Look for a platform that offers continuous, always-on monitoring to shrink the gap between detection and response, giving your team the critical head start they need to defend your environment effectively.
Detecting a threat is only half the battle. What happens next is what truly matters. A top-tier platform moves beyond simple alerts and incorporates automated incident response to kickstart remediation. When a critical risk is identified, the system should be able to automatically create a ticket, assign it to the correct team, and even initiate containment actions like isolating a compromised endpoint. This automation reduces the manual burden on your security team, prevents critical alerts from falling through the cracks, and dramatically shortens your response time. It ensures that every alert is met with a swift, consistent, and trackable action, turning your security operations into a well-oiled machine.
You can’t protect what you can’t see. That’s why complete attack surface coverage is essential. Your attack surface includes every possible entry point for an attacker—from on-premise servers and employee laptops to cloud applications and IoT devices. Many organizations have significant blind spots, especially with the rise of shadow IT and remote work. A great platform will continuously discover and map your entire digital footprint, giving you a unified view of all your assets and their associated vulnerabilities. This comprehensive visibility, a core feature of platforms like Uni5 Xposure, is the only way to ensure there are no hidden backdoors for attackers to exploit.
Your continuous monitoring platform shouldn’t be a silo. It needs to integrate smoothly with your existing security ecosystem to be truly effective. Look for a solution with a robust API and pre-built connectors for your essential tools, including your SIEM, SOAR, and ticketing systems. This allows for a seamless flow of data, enriching alerts with context from other sources and streamlining workflows across different platforms. For example, integrating with log management tools can provide deeper insights into user activity. A platform that works well with others makes your entire security stack smarter and more efficient, breaking down data barriers and fostering better collaboration.
Not all threats are created equal. A high-quality monitoring platform uses built-in threat intelligence to help you prioritize what matters most. Instead of just flagging a vulnerability, it provides crucial context: Is this flaw being actively exploited in the wild? Is it associated with a specific ransomware group? This intelligence transforms a long list of alerts into a focused, actionable to-do list. By leveraging insights from security research teams like HiveForce Labs, your team can concentrate its efforts on patching the vulnerabilities that pose a clear and present danger to your organization, rather than wasting time on low-risk issues.
Choosing the right continuous threat monitoring platform can feel overwhelming. The market is packed with options, each with its own strengths and ideal use cases. To help you cut through the noise, I’ve reviewed six of the top platforms. Think about your team’s current size, existing toolset, and primary security goals as you read through these, from comprehensive exposure management to specialized endpoint protection. This breakdown will help you find the solution that fits your organization’s unique needs.
Hive Pro’s Uni5 Xposure platform is built for teams that want to move from a reactive to a proactive security posture. It enables you to stay ahead of threats with rich threat intelligence, revealing critical vulnerabilities, zero-days, and more to fuel your security measures. What sets it apart is its ability to provide a unified and actionable view of your entire threat exposure and risk landscape. This isn’t just about finding problems; it’s about getting clear, prioritized guidance on what to fix first. By focusing on continuous cybersecurity assurance, Hive Pro helps you transform vulnerability data into confident action, ensuring your team is always working on the most critical risks.
Splunk Enterprise Security is a powerhouse for large organizations with mature security teams. If your team is adept at sifting through massive datasets, this platform is for you. It truly excels in analyzing vast amounts of log data to provide deep, granular insights into security events. Think of it as a high-powered analytics engine for your security operations. While it might have a steeper learning curve, the payoff is a highly customizable and powerful tool for security investigation and monitoring. It’s an excellent choice for enterprises that need to correlate data from countless sources to get a comprehensive view of their security posture.
When your top priority is protecting endpoints, CrowdStrike Falcon is a leading contender. It’s particularly effective at stopping attacks on devices like laptops and servers. The platform doesn’t just rely on known signatures; it uses advanced machine learning and behavioral analysis to identify and block threats in real-time, even those it has never seen before. This makes it incredibly strong in identifying sophisticated threats that might otherwise slip through traditional defenses. For teams that need robust, next-generation antivirus and endpoint detection and response (EDR) capabilities rolled into one, CrowdStrike offers a compelling and effective solution.
Qualys Continuous Monitoring is a great fit for organizations focused on vulnerability management and compliance. If you need to keep a constant watch on your network’s perimeter and ensure you’re meeting regulatory requirements, this platform delivers. It provides continuous visibility into your security posture, helping you quickly identify and remediate weaknesses before they can be exploited. It’s especially valuable for assessing the security of your network’s edge and ensuring that no new vulnerabilities go unnoticed. For teams that need a strong, compliance-driven approach to security monitoring, Qualys provides the necessary tools and reporting to stay on top of things.
For security teams looking to streamline their workflows, Palo Alto Cortex XSOAR is designed with automation at its core. This platform shines in its ability to orchestrate actions across your entire security stack. It’s built to help you automate your response to security incidents, connecting disparate tools into a single, cohesive workflow. This significantly enhances operational efficiency by reducing manual tasks and speeding up response times. If your team spends too much time toggling between different dashboards and manually executing response playbooks, Cortex XSOAR can help you integrate your solutions and automate those critical processes.
If your organization is heavily invested in the Microsoft ecosystem, Microsoft Sentinel is a natural choice. It integrates seamlessly with services like Azure and Microsoft 365 Defender, offering robust cloud-native security. The platform leverages AI to provide intelligent threat detection, helping you find real threats quickly and reduce alert fatigue. It’s best suited for organizations that want a comprehensive security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution that works hand-in-glove with their existing Microsoft services. Its intelligent capabilities help automate responses to threats, making it a powerful tool for modern security challenges.
Adding a new tool to your security stack can feel like a big move. The last thing you want is another isolated dashboard that doesn’t communicate with the systems you already rely on. A truly effective continuous threat monitoring platform won’t create another data silo; it will act as a central hub that enriches your entire security ecosystem. The goal is to make your existing tools—from your SIEM to your ticketing systems—smarter and more effective.
When a platform integrates smoothly, it allows you to automate workflows, share data seamlessly, and get a unified view of your security posture without having to constantly switch between screens. This connectivity is what turns a collection of individual tools into a cohesive, well-oiled security machine. When evaluating platforms, don’t just look at the features in a vacuum. Think about how it will plug into your current environment. A platform like Hive Pro’s Uni5 Xposure is designed to connect with your existing infrastructure, ensuring you get more value from the investments you’ve already made and can focus on confident action instead of reactive guessing.
Think of an API (Application Programming Interface) as a universal translator that allows your different software tools to talk to each other. A platform with a robust API is essential because it lets you pull in crucial data from various sources and push out important findings to other systems. For example, a strong API allows your monitoring platform to connect directly with log management tools, gathering data about user activities and system events. This integration is key for real-time analysis and gives you a much richer context for potential threats, strengthening your overall security posture. Without solid API support, you’re stuck with manual data transfers, which are slow, error-prone, and simply not practical for modern security operations.
Your Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms are the heart of your security operations center (SOC). Your SIEM aggregates and analyzes log data, while your SOAR automates your response playbooks. Any new monitoring tool you bring in must be compatible with them. This ensures that when your monitoring platform detects a credible threat, it can automatically send an alert to your SIEM for correlation and trigger a predefined workflow in your SOAR. This approach helps streamline your risk management processes, cutting down response times from hours to minutes and building a more resilient defense against attacks.
Beyond your SIEM and SOAR, your team likely uses a whole suite of other tools to get work done, including ticketing systems, asset management databases, and other development tools. A great continuous threat exposure management platform should integrate easily with these systems. This capability is what creates a truly seamless workflow. For instance, when a critical vulnerability is identified, the platform can automatically create a ticket in Jira and assign it to the correct remediation team with all the necessary context. This removes manual steps and ensures that nothing falls through the cracks. This ability to integrate with your existing tools is crucial for improving your security framework without having to rip and replace your entire stack.
Figuring out the cost of a continuous threat monitoring platform isn’t like picking an item off a shelf with a clear price tag. The investment depends heavily on your organization’s specific needs, size, and complexity. Most providers have moved away from simple, one-size-fits-all pricing because a small startup has vastly different security requirements than a multinational financial institution.
Instead of just looking for the cheapest option, it’s better to think about the value a platform provides. A lower price might mean fewer features, less support, or a tool that doesn’t scale with your business. The goal is to find a solution that fits your budget while giving you the comprehensive coverage you need to protect your assets. Understanding the common pricing structures and the factors that influence them will help you have a more productive conversation with vendors and find the right fit for your security stack.
You’ll find that pricing for continuous threat monitoring is rarely a flat fee. Many providers now base their pricing on your specific risk profile, considering factors like your industry, the sensitivity of your data, and your overall threat exposure. This value-based approach ensures you’re paying for the level of protection you actually need.
Some common structures you might encounter include pricing per asset, per user, or tiered subscription levels that offer different feature sets. However, the trend is moving toward a more customized model. Competing solely on price can lead to a race to the bottom, so reputable vendors focus on demonstrating the value and ROI of their services. Be prepared to discuss your environment in detail to get an accurate quote.
Several key variables will shape the final price of your continuous threat monitoring solution. The complexity of your IT environment is a major one; a sprawling network with a mix of on-premise servers, cloud instances, and IoT devices will cost more to monitor than a simple, cloud-native setup. The number of endpoints or assets you need to cover is another primary driver of cost.
Beyond the technical scope, the level of service you require plays a big role. Do you need 24/7 monitoring with a dedicated security analyst, or is an automated platform with standard support sufficient? Your industry’s compliance requirements, like HIPAA or PCI DSS, can also add to the cost, as they demand more rigorous monitoring and reporting capabilities.
To get the most out of your investment, shift your focus from cost to value. A strong continuous threat monitoring platform does more than just send alerts; it helps you build a more resilient security program. By catching threats before they can cause significant damage, you avoid the massive costs associated with data breaches, downtime, and reputational harm.
Think of it as a proactive investment that pays dividends over time. An effective platform streamlines your security operations, allowing your team to focus on strategic initiatives instead of chasing down endless false positives. It protects your brand and builds trust with your customers. When you evaluate platforms, consider how they will reduce your overall risk and improve your team’s efficiency—that’s where the true value of security services lies.
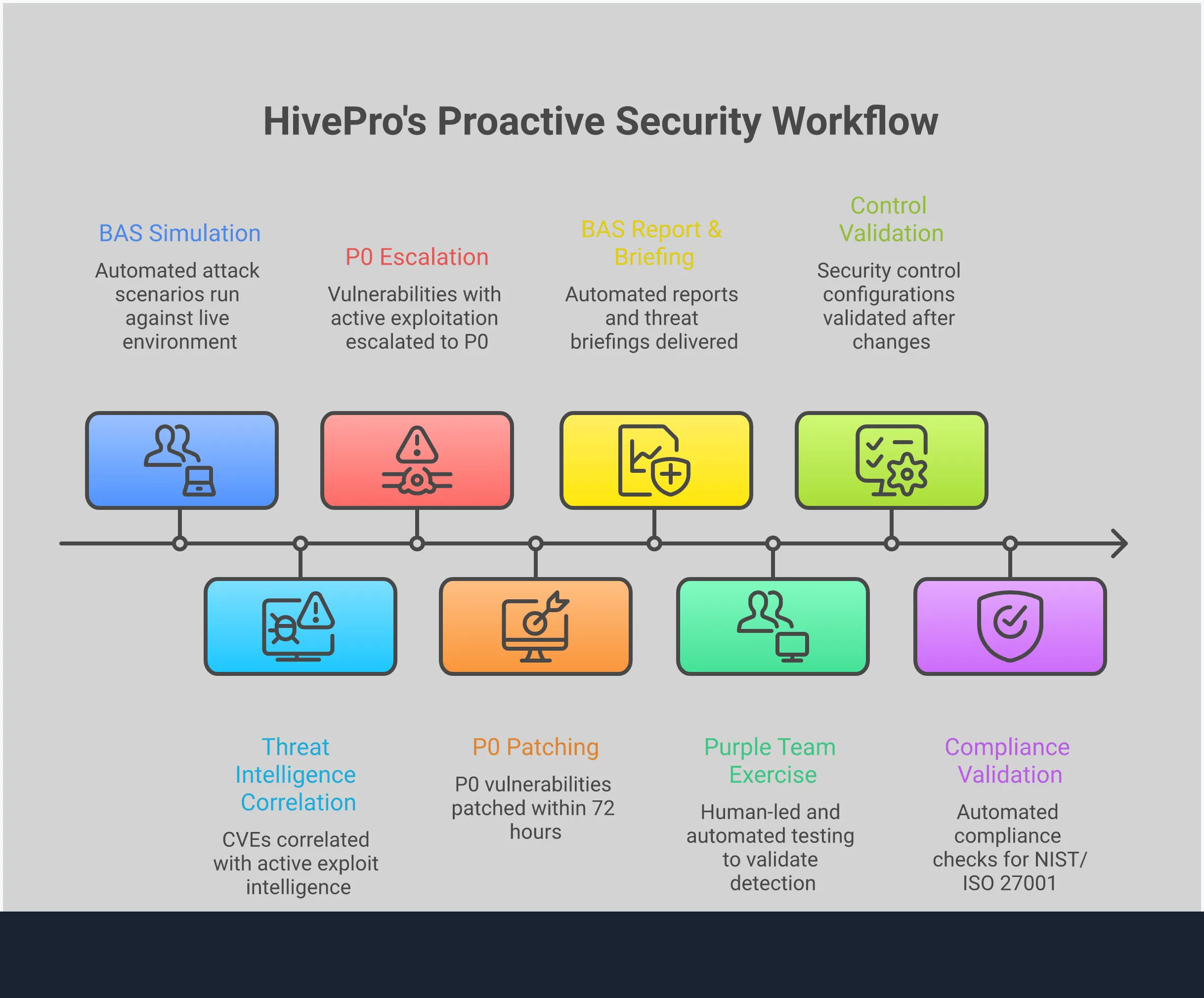
Continuous monitoring is fantastic for seeing what’s happening across your network, but how do you know if your tools are actually catching the right things? It’s easy to assume your expensive security stack is working perfectly, but assumptions can be dangerous in cybersecurity. This is where Breach and Attack Simulation (BAS) comes in. Instead of waiting for a real attack to test your defenses, BAS lets you safely and continuously simulate them on your own terms.
Think of it as a fire drill for your security operations. BAS platforms run automated, realistic attack scenarios against your live environment to see how your security controls respond. This proactive approach is a core part of a modern Threat Exposure Management program because it moves you from a passive, reactive posture to an active one. You’re no longer just watching and waiting for an alert to pop up; you’re actively pressure-testing your entire security ecosystem—from your firewalls and EDR to your SIEM and your team’s response procedures. This continuous validation ensures your monitoring isn’t just collecting logs, but is actually capable of detecting and stopping a real-world threat before it causes damage.
The biggest advantage of BAS is its ability to test your security controls in real time. By simulating a wide range of attack scenarios, from common malware infections to sophisticated multi-stage attacks, you can see exactly how your existing security measures hold up. This isn’t a theoretical tabletop exercise; it’s a practical, hands-on way to see if your configurations are correct and your tools are performing as expected. This process of Adversarial Exposure Validation helps you answer critical questions like, “Would our EDR block this specific ransomware strain?” or “Will our firewall prevent this type of data exfiltration?” before an actual attacker forces you to find out the hard way.
A silent SIEM doesn’t always mean you’re secure—it could mean your detection capabilities have failed. BAS provides a reliable way to validate that your monitoring tools are actually working. The simulations are designed to generate alerts that mimic real-world attacks, giving you a clear signal of whether your systems can identify threats as they happen. If you run a simulated phishing attack and your security tools don’t raise a flag, you know you have a blind spot. This continuous feedback loop allows you to fine-tune your detection rules, reduce false positives, and build genuine confidence that your security team has the visibility it needs to respond effectively when a real incident occurs.
Traditional security assessments like annual penetration tests are useful, but they only provide a snapshot in time. Your environment is constantly changing, and new gaps can appear overnight. By using BAS, you can continuously pinpoint gaps in your defenses that might otherwise go unnoticed. These simulations can uncover misconfigurations, policy violations, or process weaknesses that create an opening for an attacker. This proactive approach allows your team to find and address vulnerabilities before they can be exploited. It shifts your focus from simply managing a long list of potential vulnerabilities to understanding and closing the actual attack paths that threaten your organization.
Effective monitoring is about more than just collecting logs and alerts; it’s about understanding them. Without context, your security team is left sifting through a mountain of data, trying to distinguish real threats from background noise. This is where threat intelligence comes in. It provides the crucial context needed to make sense of security events, transforming your monitoring from a reactive chore into a proactive defense strategy.
By integrating up-to-date threat intelligence, you can connect the dots between seemingly unrelated alerts and see the bigger picture of an attack campaign. It helps you understand not just what is happening on your network, but why it’s happening and who might be behind it. This insight is fundamental to moving faster than your adversaries and stopping attacks before they cause real damage.
Your vulnerability scanner probably gives you a list of issues as long as your arm, each with a generic severity score. But the reality is, not all vulnerabilities pose an equal threat. Many will never be exploited. Threat intelligence cuts through the noise by showing you which vulnerabilities are being actively used by attackers in the wild. This allows you to focus your remediation efforts on the gaps that present a clear and present danger to your organization. Instead of chasing every medium-severity finding, your team can confidently address the critical exposures first. This risk-based approach, a core part of vulnerability and threat prioritization, ensures your limited resources are spent where they’ll have the greatest impact, significantly reducing your attack surface.
Threat intelligence gives you a peek inside the attacker’s playbook. It goes beyond just identifying a piece of malware or a vulnerable port; it details the tactics, techniques, and procedures (TTPs) that adversaries use to achieve their goals. When you understand how attackers conduct reconnaissance, gain initial access, and move laterally, you can better anticipate their next steps. This knowledge, often curated by dedicated research teams like HiveForce Labs, allows you to fine-tune your detection rules, create more realistic incident response drills, and build defenses that are resilient against real-world attack methods. You’re no longer just reacting to alerts—you’re actively hunting for specific malicious behaviors.
When your monitoring platform is fueled by high-fidelity threat intelligence, your security team can finally get ahead of alert fatigue. Instead of spending their days chasing down false positives, they can concentrate on investigating and mitigating credible threats. This shift has a massive impact on both efficiency and morale. A platform that provides a unified view of cyber risks helps your team see clear metrics on your security posture and directs their attention to the most pressing issues. By validating which threats are real and which are theoretical, you empower your team to work smarter, not harder, and make confident, data-driven decisions that strengthen your overall security.
Adopting a new continuous threat monitoring platform is a big step, and like any major project, it can come with a few bumps in the road. Knowing what to expect can make the transition smoother for your entire team. The goal isn’t just to install a new tool, but to integrate it into your workflow in a way that actually makes your job easier and your organization safer. Often, the most significant challenges aren’t about the technology itself, but about how it interacts with your people and existing processes. Getting this right from the start is key to seeing a real return on your investment.
From the flood of notifications that can drown out real threats to the classic tug-of-war between security and IT teams, these hurdles are familiar to many in the industry. There’s also the foundational challenge of simply knowing what assets you have and where they are. These aren’t new problems, but a modern platform should help you solve them, not add to them. By anticipating these issues, you can create a clear plan to address them head-on. Let’s walk through some of the most common implementation hurdles and talk about practical ways to clear them.
If your team feels like they’re constantly drowning in notifications, you’re not alone. Many security tools generate a high volume of alerts without enough context, which leads to alert fatigue. When your team is overwhelmed, it becomes incredibly difficult to distinguish a genuine, urgent threat from low-level noise. This is when critical incidents can slip through the cracks. A good continuous monitoring platform should be a filter, not a firehose. Look for a solution that offers intelligent vulnerability and threat prioritization to surface the most critical issues, giving your team the context they need to act decisively on the threats that truly matter.
There’s often a natural tension between security and IT operations. Security teams are driven to patch every vulnerability, while IT and DevOps teams are focused on maintaining uptime and performance. This friction can slow down remediation cycles and leave critical risks exposed for far too long. A successful implementation bridges this gap. Your platform should provide clear, actionable guidance that helps both teams agree on priorities. By focusing on the vulnerabilities that pose a real, immediate threat to your specific environment, you can direct your limited resources to where they’ll have the biggest impact, turning a contentious process into a collaborative one.
You can’t protect what you don’t know you have. For many organizations, achieving a complete and accurate inventory of all assets is a massive challenge. Fragmented systems, shadow IT, and inconsistent data formats create blind spots that attackers are quick to exploit. A continuous monitoring platform is only as good as the data it sees. That’s why comprehensive total attack surface management is non-negotiable. Before you can monitor for threats, you need a platform that can continuously discover and catalog every device, application, and cloud service, giving you a single, unified view of your entire digital footprint.
Continuous threat monitoring is a cornerstone of modern cybersecurity, but a few persistent myths can cloud its true purpose and value. Let’s clear the air on what these platforms can—and can’t—do for your security program. Understanding these distinctions is key to setting realistic expectations and getting the most out of your investment. It’s not about finding a magic bullet, but about integrating a powerful capability into your existing security stack to make your team smarter, faster, and more effective at managing risk.
One of the most common misconceptions is that you can simply deploy a continuous monitoring platform, switch it on, and let it run on autopilot. The reality is that an effective program is never a passive tool. It requires a solid framework and ongoing human engagement to deliver real value. Your team needs to configure the platform, fine-tune alerts to reduce noise, and interpret the data it provides. Think of it less like a smoke detector that you install and forget, and more like a command center that requires skilled operators to establish security and respond to incoming intelligence.
No single tool or strategy can make your organization completely immune to cyber threats, and continuous monitoring is no exception. Its primary function isn’t to create an impenetrable fortress but to drastically shorten the time it takes to spot and react to potential attacks. The goal is to quickly identify and respond to security events, giving your team the visibility needed to contain a threat before it causes significant damage. It’s about shifting from a reactive stance to a proactive one by reducing risk and improving your overall security posture, not eliminating risk entirely.
It’s easy to assume that all continuous threat monitoring platforms offer the same core functionality, but that’s far from the truth. The market is filled with tools that vary widely in their capabilities, from the breadth of their attack surface coverage to the quality of their threat intelligence. Some platforms simply aggregate data, while more advanced solutions provide a unified and actionable view of your threat exposure. When evaluating options, look closely at how a platform integrates with your existing tools, whether it helps prioritize alerts, and if it provides the context your team needs to take confident action.
Picking a continuous threat monitoring platform isn’t just about comparing feature lists. It’s about finding a solution that fits seamlessly into your existing security ecosystem and addresses your organization’s unique challenges. With so many options on the market, it’s easy to get distracted by flashy dashboards and long lists of capabilities. The key is to step back and follow a structured approach to find the platform that will truly work for your team.
Think of this process as a strategic initiative, not just a procurement task. The right platform should feel like an extension of your team, automating routine tasks and providing the clarity needed to make smart, fast decisions. It needs to align with your security philosophy, your operational workflows, and your long-term goals. By focusing on your specific needs first, you can cut through the marketing noise and identify a tool that provides real value. We’ll walk through three key steps: assessing your current posture, aligning features with your needs, and planning for implementation.
Before you even look at a demo, you need a crystal-clear picture of your own environment. Effective monitoring starts with a deep understanding of your organization’s risk landscape. What are your most critical assets? Where are your known blind spots? What compliance requirements are you bound by? Answering these questions will give you a baseline to measure potential platforms against. You need to map your entire attack surface to understand what you need to protect. This internal audit helps you create a concrete list of requirements, turning a vague search for a “good platform” into a targeted hunt for the right platform for your specific security gaps and goals.
Once you know what you need to protect, you can start evaluating which platform has the right tools for the job. Instead of getting swayed by every feature, focus on the capabilities that address the specific needs you just identified. Do you need automated data collection and real-time alerts to meet compliance standards? Are you looking for a continuous feedback loop that helps your team adapt to new threats? Create a checklist of “must-have” versus “nice-to-have” features. This ensures you prioritize core functionality, like comprehensive threat intelligence and seamless integrations, over secondary features that may not be relevant to your daily operations.
A powerful platform is only effective if your team can actually use it. Consider how a new tool will integrate with your existing security stack. Does it have a robust API? Will it connect easily with your SIEM and SOAR solutions? A platform that creates a unified view of cyber risks is far more valuable than one that operates in a silo and adds to your team’s workload. Think about the future, too. Your organization will grow, and your security needs will evolve. Choose a platform that can scale with you, handling more assets, data, and users without a drop in performance or a major overhaul.
How is continuous monitoring different from our annual penetration tests? That’s a great question because it gets to the heart of a major shift in security strategy. Think of a penetration test as a snapshot in time. It’s incredibly valuable for finding vulnerabilities at that specific moment, but your environment and the threat landscape change the very next day. Continuous monitoring, on the other hand, is like a live video feed. It provides an always-on, dynamic view of your security posture, helping you spot new weaknesses and active threats as they emerge, not just once a year.
My team is already overwhelmed with alerts. Won’t this just add more noise? I completely understand this concern—it’s one of the biggest challenges in security operations. The goal of a modern monitoring platform isn’t to create more alerts, but to provide better ones. A strong platform uses high-quality threat intelligence to filter out the noise and prioritize what actually matters. Instead of flagging every single potential vulnerability, it highlights the ones that are actively being exploited by attackers, so your team can focus its energy on clear and present dangers.
We already have a SIEM. Why do we need a separate continuous monitoring platform? While a SIEM is essential for collecting and analyzing log data, a continuous threat exposure management platform serves a different, more proactive purpose. It focuses on giving you a unified view of your entire attack surface, prioritizing vulnerabilities based on real-world threats, and validating that your security controls are working as expected. The two systems work best together; the monitoring platform provides crucial context that makes the data in your SIEM more meaningful and actionable.
Our biggest challenge is just knowing what assets we have. Should we fix that before considering a monitoring platform? You’ve hit on a foundational issue for so many organizations. The good news is that you don’t need a perfect asset inventory to get started. In fact, a top-tier platform should be part of the solution. Look for a platform with built-in attack surface management capabilities. It will continuously discover and map all of your assets—from servers to cloud applications—giving you the visibility you need to protect them effectively.
How can I justify the investment in a new monitoring platform to my leadership? When talking to leadership, it’s best to frame the conversation around business risk and operational efficiency. A continuous monitoring platform is a proactive investment that helps prevent the massive costs associated with a data breach, including downtime, regulatory fines, and damage to your reputation. It also makes your security team more efficient by automating routine tasks and focusing their efforts on the most critical threats, which is a much better use of their time and expertise.