Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Trying to explain security priorities to your board using CVSS scores is a tough sell. A long list of technical flaws doesn’t translate to business impact, making it difficult to justify budgets and get buy-in for critical initiatives. Security leaders need a better way to frame the conversation around what truly matters: business risk. This is precisely what a Continuous Threat Exposure Management (CTEM) program is designed to do. It provides the context needed to connect a specific vulnerability to a potential attack path and, ultimately, to the critical assets it threatens. Adopting a ctem framework transforms security from a technical cost center into a strategic business enabler.
Let’s cut through the noise. Continuous Threat Exposure Management, or CTEM, is a strategic framework for managing your organization’s security risks. Think of it as a shift from a defensive, wait-and-see approach to a proactive, always-on security mindset. Instead of just reacting to threats as they pop up, a CTEM program helps you continuously find, prioritize, and fix the security gaps that attackers are most likely to exploit. It’s about understanding your entire attack surface—from your cloud environments to your on-premise servers—and seeing it through the eyes of an adversary.
This isn’t just another name for vulnerability management. CTEM is a more holistic process that connects technical vulnerabilities to real-world business impact. It helps you answer the critical questions: Which of these thousands of alerts actually matter? What are the most likely paths an attacker could take to reach our most critical assets? By focusing on these exploitable exposure pathways, you can direct your team’s limited time and resources to the fixes that will make the biggest difference in reducing your overall risk. It’s a smarter, more efficient way to build a resilient security posture.
For years, many security teams have been stuck in a reactive cycle: a new critical vulnerability is announced, and everyone scrambles to patch it. CTEM helps you break free from this constant fire drill. It’s designed to move your security program from a reactive stance to a proactive one by helping you find and address risks before they can be exploited. By continuously monitoring your environment and validating your security controls, you can take the initiative in protecting your organization’s most important assets. This approach allows you to anticipate attacker moves and close security gaps before they become full-blown incidents.
At its heart, CTEM is built on a few key principles. First, it provides a complete, unified picture of your organization’s total attack surface. Given how complex modern IT environments are, having this comprehensive visibility is essential. Second, CTEM aligns security efforts with business goals by focusing on exploitable attack paths that threaten your critical systems and data. Instead of treating all vulnerabilities equally, it uses threat intelligence and business context to prioritize the exposures that pose the greatest risk to your operations, helping you make more strategic security decisions.
A Continuous Threat Exposure Management (CTEM) program isn’t a one-and-done project; it’s a cyclical framework that helps your security program mature. It moves you from a reactive cycle of patching and praying to a proactive rhythm of identifying, prioritizing, and validating your most critical risks. Think of it as a continuous loop that aligns your security efforts with your business objectives. Each stage builds on the last, creating a clear, repeatable process for reducing your threat exposure. Let’s break down the five core stages that make this framework so effective.
You can’t protect what you don’t know you have. The first step is to define the boundaries of your security efforts by scoping your attack surface. This means working with business leaders to identify the assets and systems that are most critical to your operations. A great place to start is with your external attack surface—anything connected to the internet that an attacker could potentially target. This includes web applications, cloud infrastructure, and APIs. By clearly defining the scope, you ensure your team focuses its limited time and resources on the parts of your digital environment that matter most, rather than trying to boil the ocean.
Once you’ve defined your scope, the next stage is discovery. This is where you map out all the assets within your defined boundaries and identify their potential weaknesses. This process goes far beyond simply scanning for common vulnerabilities and exposures (CVEs). A true CTEM approach looks for a wider range of security issues, including system misconfigurations, weak credentials, and other security flaws that automated scanners might miss. The goal is to create a comprehensive inventory of your assets and their associated exposures, giving you a complete picture of your potential risk.
With a list of vulnerabilities in hand, it’s easy to feel overwhelmed. Stage three is all about cutting through the noise by prioritizing exposures based on business risk, not just technical severity scores. A high CVSS score doesn’t automatically mean a vulnerability is your biggest problem. Instead, you should ask more pointed questions: Are attackers actively exploiting this flaw in the wild? How critical is the affected asset to our business? What security controls do we already have in place? This is where vulnerability and threat prioritization becomes essential, helping you focus on the threats that pose a genuine and immediate danger to your organization.
Prioritization tells you where to focus, but validation confirms the actual risk. In this stage, you test whether the high-priority exposures you’ve identified are truly exploitable in your specific environment. This is often done using techniques like Breach and Attack Simulation (BAS), which runs safe, simulated attacks to see if your security controls hold up. This adversarial exposure validation helps you answer critical questions: Can an attacker actually move from this vulnerability to a critical asset? Do our detection and response tools generate the right alerts? This step provides concrete proof of risk, making it much easier to get buy-in from other teams for remediation.
The final stage is all about action. Armed with a prioritized and validated list of exposures, you can mobilize the right teams to fix them. CTEM is a team sport, and effective remediation often requires collaboration between security, IT operations, and DevOps. Instead of just sending a report over the fence, a CTEM platform helps streamline this process by providing clear guidance and context. It ensures everyone understands the risk and their role in fixing it. Once remediation is complete, the cycle begins again, allowing you to continuously measure your progress and adapt to new threats as they emerge.
Adopting a Continuous Threat Exposure Management (CTEM) program is more than just a shift in tooling; it’s a fundamental change in how you approach cybersecurity. By moving from a reactive, checklist-based mindset to a proactive, business-aligned strategy, you can unlock some serious advantages. A well-run CTEM program doesn’t just find more vulnerabilities—it provides the context you need to strengthen your defenses, use your resources wisely, and protect what matters most. Let’s look at the key benefits you can expect when you put CTEM into practice.
Traditional vulnerability scanning gives you a snapshot in time, but your attack surface is constantly changing. CTEM provides a continuous, live feed of your entire environment, from your cloud infrastructure to your web applications. This constant monitoring means you can spot weak spots and potential threats as they emerge, not weeks or months later during a scheduled scan. With a complete and up-to-date view of your total attack surface, your team can connect the dots between seemingly isolated issues, understand potential attack paths, and respond to threats with greater speed and accuracy. It’s about seeing the full picture, all the time.
Are you tired of playing defense? A CTEM framework helps you get ahead of attackers by shifting your security posture from reactive to proactive. Instead of just patching vulnerabilities as they’re discovered, you can anticipate how an adversary might operate and validate your defenses against those tactics. By continuously testing your security controls and identifying the most likely paths an attacker would take, you can prioritize fixes that disrupt those paths. This approach allows you to take the initiative, systematically hardening your environment and making it a much more difficult target before an attack happens.
For most security teams, the biggest challenge isn’t finding vulnerabilities—it’s figuring out which ones to fix first. With thousands of alerts and limited resources, it’s easy to feel overwhelmed. CTEM cuts through the noise by adding business context to your technical findings. It helps you understand which assets are critical to your operations and which vulnerabilities pose a genuine threat to them. This level of vulnerability and threat prioritization means your team can stop chasing down low-risk issues and focus their time and energy on the exposures that truly matter, ensuring your efforts have the greatest possible impact on reducing risk.
CTEM empowers security leaders to have more meaningful conversations with executives and the board. Instead of presenting a long list of technical flaws, you can frame security discussions around business risk. By connecting vulnerabilities to the critical assets they threaten, you can clearly articulate the potential impact of an attack in terms of revenue, reputation, and operations. This approach helps justify security investments and ensures that your cybersecurity strategy directly supports the organization’s broader goals. It transforms security from a cost center into a strategic business enabler, building trust and alignment across the company.
Traditional vulnerability management walked so CTEM could run. It’s not about throwing out the old playbook but upgrading it for today’s complex environments. For years, security teams have been stuck in a reactive cycle of scan-and-patch, trying to keep up with an endless list of vulnerabilities. It’s a volume game that’s hard to win, often feeling like you’re just checking boxes for compliance rather than making a real impact on security.
CTEM shifts the entire mindset from simply managing vulnerabilities to actively reducing threat exposure. It’s a strategic, continuous, and business-focused approach that helps you get ahead of attackers. The old way was about creating a list of problems; the new way is about creating a plan of action that protects what matters most. CTEM connects the dots between a technical flaw, a potential attack path, and the business asset at the end of that path. This context is everything. It transforms your security program from a cost center focused on patching to a strategic function that directly protects business value. It’s the difference between having a map of all the potholes in the city versus having a clear route that avoids the ones on your way to your most important destination.
Traditional vulnerability management programs often leave you with a mountain of CVEs, each with a technical severity score. While a CVSS score of 9.8 is certainly alarming, it lacks business context. Is that critical vulnerability on a test server with no sensitive data, or is it on the server that processes all your customer payments? Without that context, teams can spend valuable time patching low-impact issues while a more significant threat flies under the radar. CTEM flips the script by focusing on business risk first. It helps you understand which vulnerabilities create exploitable attack paths to your most critical assets. This approach allows for a much smarter vulnerability and threat prioritization, ensuring your team’s efforts are directed where they can make the biggest difference in protecting the business.
If you only check for problems once a quarter or once a month, you’re giving attackers a pretty wide window of opportunity. Traditional vulnerability management often relies on these periodic scans. The problem is, your attack surface isn’t static. New assets spin up in the cloud, developers push new code, and new threats emerge daily. A snapshot in time quickly becomes outdated, leaving you blind to new exposures that appear between scans. CTEM replaces this outdated model with continuous monitoring. By constantly scanning your entire environment, you get a real-time feed of your security posture. This allows you to maintain total attack surface management and spot new weaknesses the moment they appear, dramatically shortening the time an attacker has to exploit them.
Your attack surface is likely much bigger and more complex than it was a few years ago. It’s not just servers in a data center anymore; it’s a mix of on-premise infrastructure, multiple cloud environments, SaaS applications, and IoT devices. Traditional vulnerability management tools were not built for this reality and often struggle to see the full picture, creating dangerous blind spots. CTEM is designed to provide a unified view of risk across this entire hybrid landscape. It helps you discover and assess all your assets, wherever they are. By consolidating this information, a CTEM platform gives you a single source of truth for your organization’s exposure, helping you operationalize your security program from discovery and prioritization all the way through to validation and remediation.
A CTEM program without threat intelligence is like a map without a compass. You can see the terrain—all your assets and vulnerabilities—but you have no direction. You’re left with a massive list of potential issues, with little insight into which ones pose a genuine, immediate threat. This is where many vulnerability management programs get stuck, drowning in data but starved for wisdom.
Threat intelligence provides that crucial context. It transforms your CTEM strategy from a theoretical exercise into a real-world defense plan. Instead of just asking, “What are our weaknesses?” you can start asking, “Which of our weaknesses are attackers actively targeting right now?” This shift is fundamental. It allows you to see your organization through an attacker’s eyes, understanding which vulnerabilities are not just technically severe but are also being weaponized in the wild. By integrating up-to-the-minute data on attacker tactics and trending threats from research teams like HiveForce Labs, you can cut through the noise and focus your team’s efforts where they will have the greatest impact.
Your security team has a finite amount of time and resources. You can’t fix every single vulnerability at once, so you have to make tough choices. Threat intelligence makes those choices much clearer. It enriches vulnerability data with real-world context, showing you which common vulnerabilities and exposures (CVEs) are part of active attack campaigns. This allows you to move beyond relying solely on CVSS scores, which only measure potential severity, not actual risk. With this insight, you can create a vulnerability and threat prioritization queue that addresses the most dangerous exposures first, ensuring your most critical assets are protected from the threats that matter right now.
Threat actors are constantly evolving their methods. What worked for them last month might be replaced by a new tactic tomorrow. Threat intelligence gives you a continuous, high-level view of this shifting landscape. You gain insight into which industries are being targeted, what types of malware are trending, and the specific tactics, techniques, and procedures (TTPs) attackers are using. This knowledge allows you to be more proactive. Instead of waiting for an attack to happen, you can anticipate an adversary’s likely moves and adjust your defenses accordingly. Reading regular threat advisories helps your team stay ahead of emerging threats and make more informed strategic decisions.
There’s a big difference between a vulnerability that is theoretically exploitable and one that is actively being used in attacks. Many high-severity vulnerabilities are never weaponized because they are too complex or impractical for attackers to exploit at scale. Threat intelligence helps you filter out this noise. It highlights the specific, exploitable attack paths that adversaries are using to compromise critical assets. This focus is a core principle of a modern threat exposure management platform. By concentrating on the vulnerabilities that are proven weapons in an attacker’s arsenal, you can direct your remediation efforts with precision and confidence, fixing the problems that present a clear and present danger to your business.
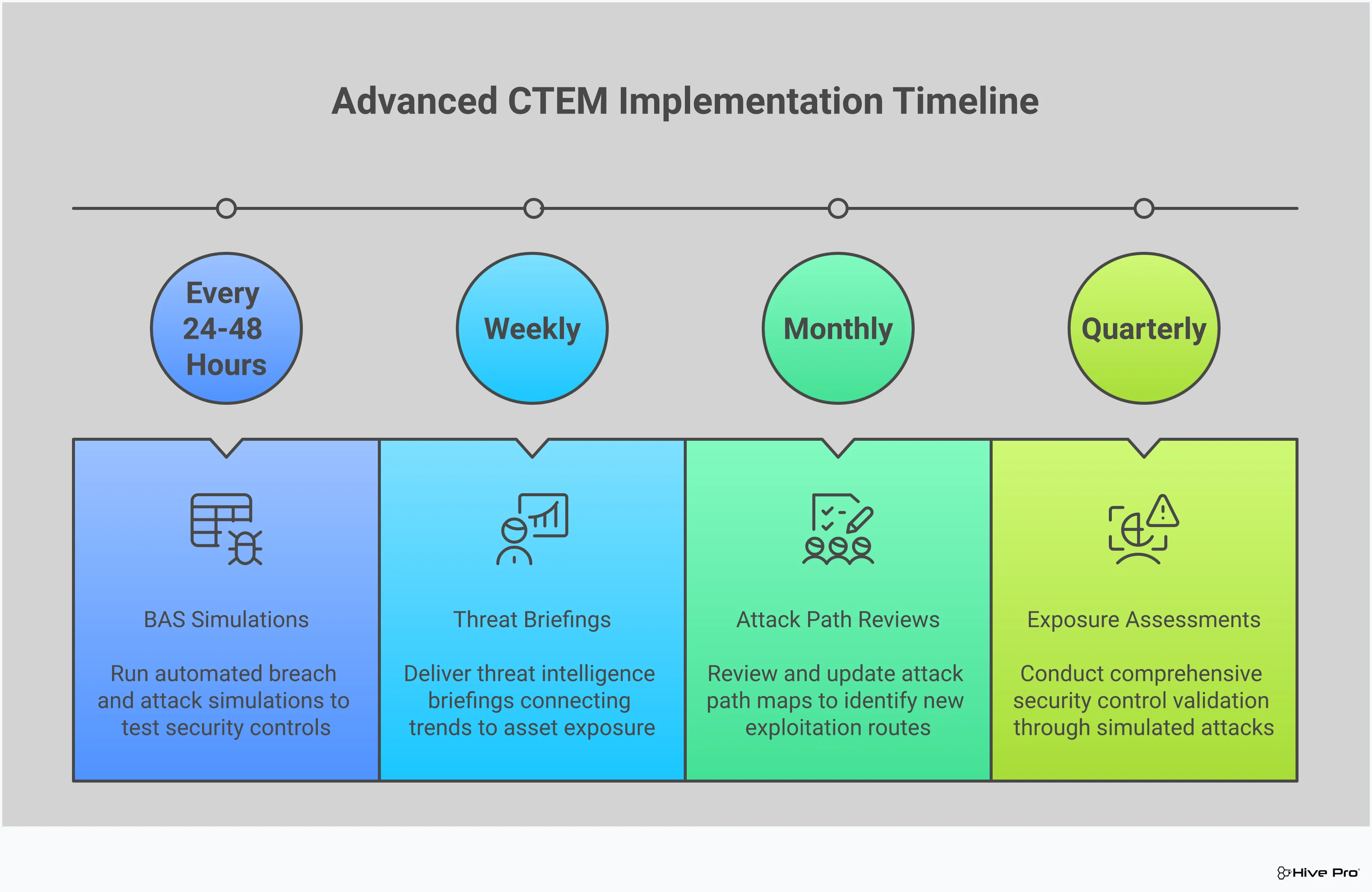
After you’ve identified your assets and prioritized your vulnerabilities, you might feel like the hardest work is done. But there’s a critical question that remains: do your security controls actually work? It’s one thing to have a firewall, an EDR solution, and security policies in place. It’s another to know for certain that they’ll stand up to a real-world attack. This is where Breach and Attack Simulation (BAS) comes in, acting as the validation stage of the CTEM framework.
Think of BAS as a controlled sparring match for your security infrastructure. It uses automation to safely simulate the tactics, techniques, and procedures (TTPs) that attackers use every day, from ransomware to phishing. Instead of waiting for a real incident to find the gaps in your defenses, you can proactively test them in a safe environment. This process of adversarial exposure validation is essential for moving beyond theoretical security and into proven, practical defense. By running these simulations, you get a clear, evidence-based picture of where your controls are strong and, more importantly, where they might fail when it matters most.
Your security stack is made up of many different tools, each with its own job. But are they configured correctly? Are they communicating with each other? BAS helps you answer these questions by putting your defenses to the test. It runs simulated attacks against your environment to see if your security tools detect and block the threats as expected.
This is like a fire drill for your security posture. It’s a safe, controlled way to find out if your smoke detectors are working and if your team knows the escape routes. A BAS platform can reveal misconfigurations, policy gaps, or tools that aren’t performing as promised, giving you the data you need to fine-tune your defenses before an actual emergency.
Attackers rarely rely on a single vulnerability. Instead, they chain together multiple weaknesses to create an “attack path” from the network perimeter to your most critical assets. A minor flaw on a public-facing web server might seem low-risk on its own, but it could be the first step an attacker takes to move laterally and eventually access sensitive data.
BAS helps you see your organization through an attacker’s eyes. By simulating multi-stage attacks, it identifies and validates these potential attack paths across your entire attack surface. This allows you to understand how different vulnerabilities connect and to prioritize the fixes that will disrupt the most likely routes an attacker would take, effectively shutting them down before they can even get started.
One of the biggest challenges in cybersecurity is proving that your efforts are making a difference. CTEM is all about the continuous reduction of threat exposure, and BAS provides the perfect way to measure your progress. By running simulations before and after your remediation activities, you can generate concrete evidence that your fixes have worked.
This creates a powerful feedback loop. You can run a simulation, identify a weakness, apply a patch or change a configuration, and then run the same simulation again to confirm the gap is closed. This data is invaluable for demonstrating ROI and communicating security posture improvements to leadership. You’re no longer just reporting on the number of vulnerabilities patched; you’re proving that you’ve made the organization measurably more secure.
Adopting a CTEM program is a powerful move, but let’s be real—it’s not as simple as flipping a switch. Like any significant strategic shift, the path to a successful implementation has its share of hurdles. Many organizations find that their existing tools, processes, and even team structures aren’t quite ready for the continuous, proactive approach that CTEM demands.
The good news is that these challenges are well-understood and completely surmountable with the right strategy and tools. The goal isn’t to find a perfect, problem-free starting point, but to anticipate these roadblocks and plan for them. From wrestling with a disjointed tech stack to managing the sheer volume of data, understanding these common issues is the first step toward building a resilient and effective threat exposure management program. Let’s walk through the four main challenges you’re likely to encounter and how to think about solving them.
Most security teams are working with a diverse collection of tools, from vulnerability scanners and asset management systems to cloud security platforms and endpoint detection solutions. The problem? They rarely speak the same language. Trying to manually piece together data from these disparate sources is time-consuming and often leaves you with an incomplete picture of your true exposure. A CTEM program relies on a continuous feed of data from across your entire environment. Without a way to centralize and correlate this information, you’ll be stuck in data silos, unable to see the full attack path. The key is to find a platform that can serve as a central hub, integrating with your existing tools to provide a single, unified view of your total attack surface.
It’s a familiar story for any security professional: you’re drowning in alerts. You have thousands of vulnerabilities across your network, and every scanner is screaming that the sky is falling. This constant noise leads to alert fatigue, where your team becomes desensitized to warnings and struggles to identify the threats that truly matter. An effective CTEM program cuts through this noise. Instead of just adding more findings to the pile, it uses threat intelligence and business context to surface the critical few vulnerabilities that pose a genuine risk. By focusing on threats that are actively exploited in the wild and tied to your most critical assets, you can move from a state of overwhelming overload to one of focused, effective vulnerability and threat prioritization.
Let’s face it: cybersecurity talent is scarce, and teams are often stretched thin. The idea of implementing and managing another complex security program can feel daunting, especially if you don’t have a large team of dedicated analysts. Many organizations worry they lack the in-house expertise to run a CTEM program effectively. This is where the right technology can bridge the gap. A modern CTEM platform should be designed to automate the heavy lifting—correlating data, analyzing attack paths, and prioritizing risks—so your team doesn’t have to. By providing clear, actionable remediation guidance, the platform empowers your existing team to operate more efficiently, reducing the need for highly specialized skills and making proactive security achievable for organizations of any size.
Implementing CTEM is more than a technology project; it’s a cultural shift. It requires moving from a reactive, ticket-based mindset to a proactive and continuous security rhythm. This change impacts how different teams work together. Security, IT operations, and development teams can no longer operate in silos. Instead, they must collaborate with a shared understanding of risk and a collective responsibility for reducing exposure. This requires clear communication, executive buy-in, and a willingness to adapt old processes. Building a strong security culture where everyone sees themselves as part of the solution is fundamental to making your CTEM program a long-term success.
Adopting a CTEM program is more than just buying a new tool; it’s about shifting your security mindset from reactive to proactive. A successful strategy requires the right technology, a clear plan, and a way to measure your progress. Let’s walk through how to build a CTEM strategy that not only works but also demonstrates real value to your organization.
Your CTEM platform is the engine of your program, so choosing the right one is critical. Look for a solution that gives you a complete picture of your entire attack surface—from on-prem servers to cloud services and everything in between. It should go beyond just flagging CVEs and identify a wide range of weaknesses, including misconfigurations and identity issues. The real power of a modern CTEM platform is its ability to connect these individual weaknesses to show you potential attack paths. This context helps you see your environment through an attacker’s eyes, moving you from a long list of vulnerabilities to a clear, prioritized set of risks.
You don’t have to overhaul your entire security program overnight. The best way to implement CTEM is with a phased approach built around its five core stages. Start by scoping what’s most important to protect, like your critical business applications. From there, use your platform to discover all associated assets and their exposures. The next step is to prioritize these threats based on which ones pose the most immediate danger. Then, validate your findings and test your defenses. Finally, mobilize the right teams with clear guidance to fix the problems. By breaking it down, you can show early wins and build momentum for your program.
To prove your CTEM program is working, you need to track the right metrics. Move past vanity metrics like the total number of vulnerabilities patched. Instead, focus on KPIs that reflect actual risk reduction. Start measuring the time it takes to remediate exposures that are actively being exploited or the reduction in attack paths to your critical assets. You can also track your security control effectiveness over time. These KPIs provide the data-driven insights you need to make smarter security decisions, justify investments, and clearly communicate the value of your work to leadership. It’s how you show you’re not just busy—you’re making the business safer.
How is CTEM really different from the vulnerability management I’m already doing? Think of it as an evolution. Traditional vulnerability management gives you a long list of technical problems, often prioritized by a generic severity score. CTEM takes that information and adds critical context. It focuses on how those vulnerabilities connect to create attack paths that lead to your most important business assets. Instead of just asking “What’s broken?”, you start asking “What’s broken that an attacker could actually use to hurt the business?” It’s a strategic shift from managing a list of flaws to actively reducing your organization’s most significant exposures.
My team is already swamped with alerts. Won’t this just add to the noise? Actually, it’s designed to do the exact opposite. A proper CTEM program is the best way to cut through the noise of endless alerts. By integrating threat intelligence and understanding what attackers are targeting in the real world, it helps you filter out the low-risk issues. It elevates the handful of vulnerabilities that pose a genuine and immediate threat to your critical systems. This allows your team to stop chasing thousands of alerts and focus their limited time and energy on fixing the problems that truly matter.
Where’s the best place to start if I want to implement a CTEM program? You don’t need to boil the ocean. The most effective way to begin is to start small and focused. Choose one critical business service or application—something essential to your operations. Then, walk that single service through the five stages of the CTEM framework. Scope its attack surface, discover its assets and exposures, prioritize the risks, validate them, and mobilize remediation. This creates a manageable pilot project that helps you refine your process and demonstrate clear wins before you roll it out more broadly.
How does Breach and Attack Simulation (BAS) fit into this process? Breach and Attack Simulation is the validation phase of the CTEM cycle. After you’ve prioritized a list of potential exposures, BAS provides the reality check. It safely runs simulated attacks to confirm if a vulnerability is truly exploitable in your specific environment and whether your existing security controls would detect or block the attempt. This provides concrete proof of risk, which makes it much easier to get buy-in for remediation, and it helps you confirm that your defenses are working as intended.
How can I show that a CTEM program is actually working? Success is measured by risk reduction, not just activity. Move away from tracking metrics like the total number of patches applied. Instead, focus on key performance indicators that demonstrate a stronger security posture. You can measure the reduction in the number of viable attack paths to your critical assets or track the decrease in time it takes to fix vulnerabilities that are known to be actively exploited. These are the kinds of results that clearly communicate the business value of your security efforts to leadership.