Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Attackers don’t think in terms of CVE scores. They look for the path of least resistance, whether it’s a forgotten server, a misconfigured cloud bucket, or an exposed API. While your team is busy prioritizing a long list of software flaws, a real threat could be exploiting a simple oversight that a traditional scanner would miss. To build a truly resilient defense, you need to adopt the same holistic view. Exposure management is the framework for doing just that. It’s a continuous process of identifying, validating, and fixing every potential entry point across your entire digital footprint. This article breaks down the core exposure management cybersecurity best practices you need to stop guessing and start seeing your security posture with the clarity of an adversary.
Think of exposure management as a continuous cycle for finding, checking, and fixing security risks across your entire digital footprint. It’s a broader approach than traditional vulnerability management, which often focuses solely on software flaws. An “exposure” can be anything an attacker might exploit—not just a CVE, but also a misconfigured cloud service, an exposed API, or even a forgotten server that’s still connected to your network. The goal is to see your organization through an attacker’s eyes, identifying every potential entry point before they do.
This process isn’t a one-and-done scan. It’s an ongoing strategy that involves constantly mapping your assets, identifying weaknesses, and validating your security controls. By understanding your complete digital environment, you can get a clear picture of where your true risks lie. This comprehensive view is the foundation of a strong security posture, helping you move beyond simply patching vulnerabilities. Instead, you begin to manage your entire Total Attack Surface with a proactive mindset, ensuring that every asset is accounted for and secured against potential threats. This shift allows security teams to work more efficiently, focusing their efforts on the issues that pose the greatest danger to the business.
For years, many security teams have been stuck in a reactive loop. You run a scan, get a massive list of vulnerabilities, and then scramble to patch the most critical ones based on generic scores. This approach often feels like a game of whack-a-mole, leaving teams overwhelmed and guessing which threats are real. It’s a model that simply can’t keep up with today’s rapidly changing IT environments and sophisticated attackers.
Exposure management changes the game by focusing on what attackers are likely to do next. Instead of just reacting to a long list of potential problems, it helps you prioritize fixes based on real-world threat intelligence and business context. It’s about moving from a long list of ‘what-ifs’ to a short, actionable list of ‘fix this now,’ which is the core of effective vulnerability and threat prioritization. By quickly addressing the most significant exposures, you can prevent attacks before they happen, protecting critical data and keeping operations running smoothly.
Building an effective exposure management strategy isn’t about finding a single magic bullet. It’s about creating a strong, continuous cycle that keeps you ahead of threats. Think of it as a four-part framework that works together to transform your security posture from reactive to proactive. By consistently discovering your assets, assessing their risks, monitoring for threats, and remediating vulnerabilities, you create a resilient defense system. Let’s break down what each of these core elements looks like in practice.
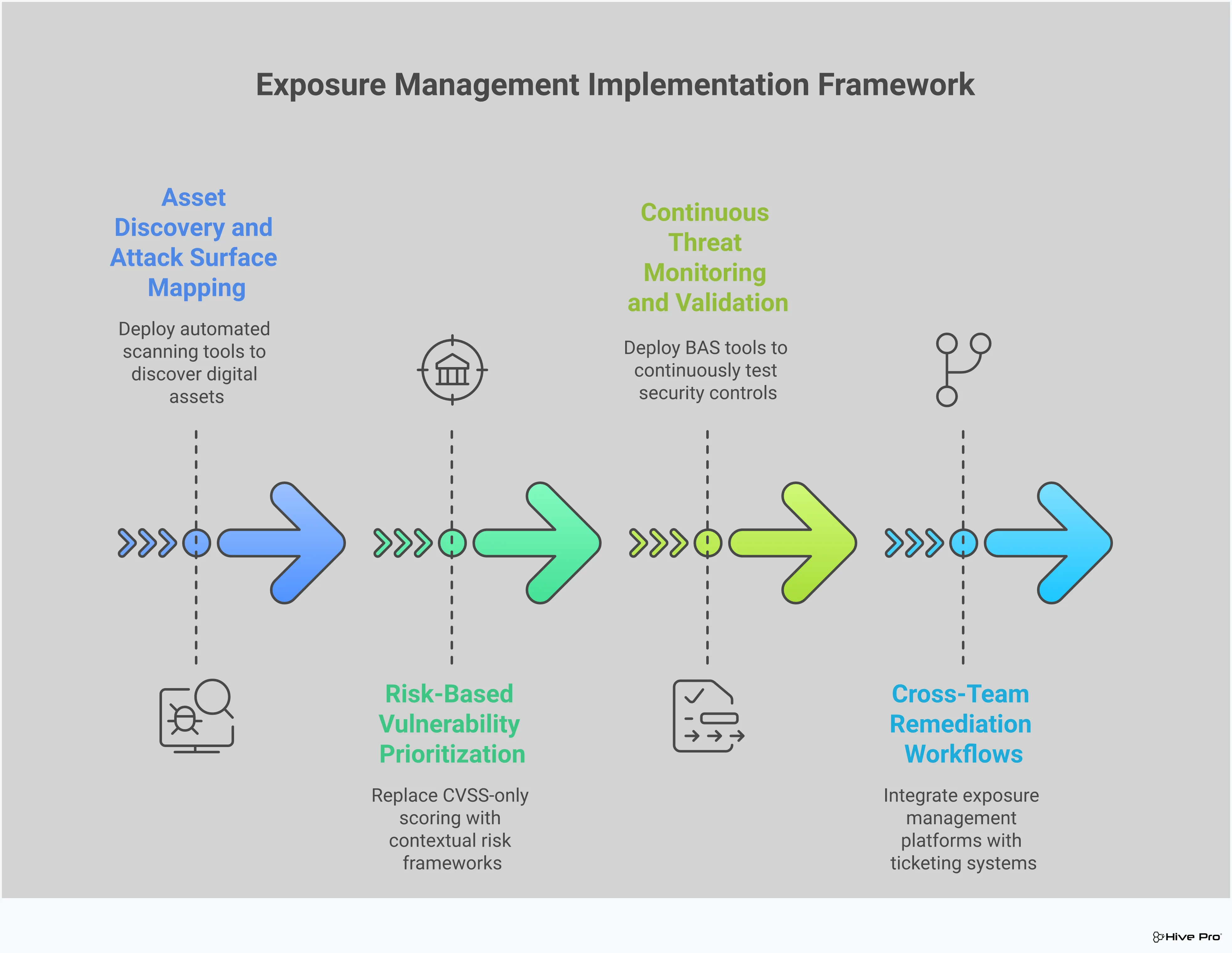
You can’t protect what you don’t know you have. The first step is to create a comprehensive inventory of every digital asset connected to your organization. This includes everything from websites and applications to IoT devices and cloud storage solutions. This complete map of your total attack surface is the foundation of your entire strategy. Without a clear and continuously updated picture of your assets, blind spots are inevitable, leaving you open to unexpected threats. This isn’t a one-time task but an ongoing process of discovery as your environment evolves.
Once you have your asset inventory, the next question is: “So what?” Not all vulnerabilities are created equal. This step involves evaluating the likelihood of an exposure being exploited and understanding the potential business impact if it is. The goal is to move beyond a massive, unmanageable list of CVEs and focus on what truly matters. By prioritizing which risks need immediate attention, you can direct your team’s valuable time and resources to the threats that pose the greatest danger to your organization, ensuring you’re tackling the most critical issues first.
The threat landscape is always changing, which means your security posture needs to be just as dynamic. Continuous monitoring is about keeping a constant watch on your systems for new vulnerabilities and active threats. This requires security tools that provide real-time protection and detection, allowing your team to respond the moment a threat emerges. Staying informed with up-to-date threat advisories is crucial for understanding the tactics attackers are using right now. This proactive vigilance ensures you’re not caught off guard by the latest exploit or malware campaign.
Identifying and prioritizing threats is only half the battle—you have to close the gaps. Remediation is where you take action to mitigate the risks you’ve uncovered. This isn’t just about patching. It can involve a range of proactive measures, such as updating software, reconfiguring firewalls, adjusting access controls, or closing unnecessary connections. The key is to have a clear plan for execution that integrates with your IT and DevOps workflows. An end-to-end exposure management platform can guide this process, turning insights into concrete actions that measurably reduce your organization’s exposure.
You can’t protect what you don’t know you have. The first step in any solid exposure management program is to get a complete and accurate picture of your digital attack surface. This means identifying every asset connected to your network—from servers and endpoints to cloud instances and IoT devices. Once you have a full inventory, you can begin to assess where your most significant exposures lie. A multi-faceted approach that combines automation with human expertise is the most effective way to get this done.
Relying on manual spreadsheets to track assets is a recipe for disaster. Your digital footprint is constantly changing, and automated tools are essential for keeping up. These tools provide continuous attack surface management by scanning your entire environment to discover both known and shadow IT assets. By implementing regular, automated vulnerability scans, you can maintain an up-to-date inventory and ensure security protocols are consistently applied. This continuous discovery process is foundational to exposure management, helping you spot new devices, open ports, and misconfigurations before an attacker does. It’s the best way to establish a comprehensive baseline of your digital presence.
While automation is powerful, it can’t catch everything. Complex, custom-built applications and unique infrastructure setups often require a human touch. Manual assessments, like penetration testing and security code reviews, allow skilled security professionals to dig deeper and identify vulnerabilities that automated scanners might miss, such as flaws in business logic. This is where your team’s expertise really shines. A hybrid strategy is key: use automated scanning for broad, continuous coverage, and deploy your team for targeted manual assessments on your most critical or complex assets. This combination ensures you cover both the breadth and depth of your attack surface.
Identifying existing vulnerabilities is crucial, but what if you could anticipate them before they even exist? That’s the goal of threat modeling. It’s a proactive, structured process where your team thinks like an attacker to map out potential threats, attack vectors, and security weaknesses during the design and development phase. By building a security mindset directly into your development lifecycle, you can design more resilient systems from the start. Threat modeling helps you prioritize security controls and focus your defensive efforts on the most likely and impactful attack scenarios, shifting your posture from reactive to genuinely proactive.
If your security team feels like they’re drowning in alerts, you’re not alone. Traditional vulnerability management often leaves teams with a mountain of findings and not enough time or resources to fix them all. The old way of prioritizing—relying solely on technical severity scores like CVSS—simply doesn’t work anymore. A “critical” vulnerability on an isolated test server is far less urgent than a “medium” one on your customer database. Without context, you risk wasting valuable time on low-impact issues while a real threat slips through the cracks.
Effective prioritization means shifting your focus from a simple checklist of vulnerabilities to a strategic, risk-based approach. It’s about understanding which threats pose a genuine danger to your specific business operations. This requires a more holistic view that combines three key elements: the business context of an asset, the likelihood of a vulnerability being exploited, and real-world intelligence about what attackers are doing right now. By adopting this mindset, you can cut through the noise and direct your team’s efforts toward the fixes that matter most. A modern vulnerability and threat prioritization strategy helps you move from being constantly reactive to proactively reducing your most significant exposures.
A risk-based framework is your guide for making smarter, context-aware decisions. Instead of treating all vulnerabilities equally, this approach helps you focus your resources on the issues that pose the greatest danger to your business. It prioritizes risks based on how likely they are to be attacked and how much damage they could cause to your operations. This means you start by identifying your most critical assets—the systems and data that are essential to your company’s success. By connecting vulnerabilities directly to these assets, you can clearly see which flaws need immediate attention. This method helps you answer the most important question: “What is the actual risk to our business?”
Once you have a risk-based framework, the next step is to evaluate each vulnerability based on two key factors: its exploitability and its potential business impact. Ask yourself: How likely is it that an attacker will exploit this weakness? And if they do, what are the consequences? This approach helps you allocate resources more effectively by focusing on the most significant threats. For example, a vulnerability that is difficult to exploit and affects a non-critical system is a much lower priority than an easily exploitable flaw in your payment processing application. Considering the impact helps you move beyond technical scores to understand the true business risk of each exposure.
Threat intelligence adds a crucial layer of real-world context to your prioritization process. It helps you understand which vulnerabilities are being actively exploited by attackers and which threats are targeting your industry. You can gather information about threats from various sources to identify trends and specific attack patterns that could affect your organization. This insight allows you to focus on vulnerabilities that pose an imminent threat, rather than a theoretical one. By integrating intelligence from sources like HiveForce Labs, you can gain a clear understanding of the current threat landscape and prioritize the vulnerabilities that attackers are using today.
Having a solid strategy is one thing, but executing it requires the right toolkit. The good news is that there are powerful solutions designed to automate and streamline exposure management. These tools help you move from manual, time-consuming processes to a more dynamic and proactive security posture. They handle the heavy lifting of discovery, analysis, and validation, giving your team the clarity needed to focus on the most critical risks. Let’s look at three essential categories of tools that form the backbone of a modern exposure management program.
Think of a CTEM platform as your central command center for cybersecurity. It integrates various security functions into a single, continuous cycle: discovery, prioritization, validation, and remediation. Instead of juggling disparate tools, a CTEM platform provides a unified view of your entire attack surface and the threats targeting it. This approach makes security a shared responsibility, not just an IT problem. As XM Cyber notes, “CTEM is not just merely some technical security/IT ‘thing’ – it’s everybody’s thing.” By consolidating data and workflows, these platforms help you see the bigger picture and make smarter, risk-informed decisions without getting lost in the noise.
Vulnerability scanners are the workhorses of any security program. They systematically scan your networks, systems, and applications to find known weaknesses, misconfigurations, and other security flaws. These tools are fundamental for identifying potential entry points before attackers do. Modern solutions go beyond simple scanning by offering robust vulnerability and threat prioritization. They help you understand which flaws pose a genuine threat to your business. By continuously monitoring for vulnerabilities, these tools also play a key role in ensuring you meet compliance requirements for regulations like GDPR, HIPAA, and PCI-DSS, making them an indispensable part of your security stack.
How do you know if your security controls will hold up against a real attack? That’s where Breach and Attack Simulation (BAS) comes in. These tools safely simulate attacker tactics, techniques, and procedures (TTPs) to test your defenses in a controlled way. While some security teams might see BAS as just another form of vulnerability management, it serves a distinct purpose: validation. A BAS tool provides adversarial exposure validation by showing you exactly where your defenses are strong and where they might fail. This allows you to move beyond theoretical risk assessments and get practical, evidence-based insights into your security posture.
Exposure management isn’t a “set it and forget it” project; it’s a dynamic, ongoing cycle. Your digital environment is constantly changing, with new assets coming online, software being updated, and configurations being tweaked. Continuous monitoring is the engine that powers a proactive security strategy, ensuring you always have a current and accurate picture of your exposure. Instead of relying on periodic snapshots that quickly become outdated, this approach gives you a live feed of your security posture. Implementing a robust continuous monitoring program involves combining real-time threat detection with smart automation and regular, structured security checks to keep your defenses sharp. This allows your team to move from putting out fires to preventing them in the first place.
In a world of ever-expanding digital footprints, waiting for a weekly or monthly scan to tell you something is wrong is no longer an option. Your attack surface is growing every day, and you need to see changes as they happen. Continuous monitoring tools are essential for providing this real-time visibility. They constantly scan your entire environment—from on-premise servers to cloud instances and connected devices—to identify new assets, unauthorized changes, and emerging threats. This allows you to manage your total attack surface proactively. By detecting anomalies the moment they occur, your security team can investigate and respond immediately, drastically reducing the window of opportunity for an attacker.
Manually sifting through security data is an impossible task. The sheer volume of information generated by monitoring tools can quickly lead to alert fatigue, where critical warnings get lost in the noise. This is where automation becomes your best friend. A modern exposure management platform uses technology to automatically discover assets, monitor for risks, and help you prioritize threats based on their potential impact. You can set up intelligent alerts that are contextual and actionable, ensuring your team only focuses on what truly matters. You can also create automated workflows that assign remediation tasks to the right people or even trigger defensive actions, streamlining your response process and freeing up your team for more strategic work.
While real-time monitoring is critical, it should be complemented by scheduled, in-depth security assessments. These checks validate that your security controls are working as intended and help you identify any systemic weaknesses. This includes activities like regular vulnerability scans, penetration testing, and using tools for adversarial exposure validation to simulate real-world attack scenarios. These planned checks provide a structured way to measure your security posture over time. They also reinforce the importance of security across the organization, contributing to a resilient cybersecurity framework and helping to build a strong, security-aware culture from the ground up.
Putting a strong exposure management program in place is a game-changer, but it’s not always a straight path. Many teams run into similar roadblocks, from getting buried in data to managing complex cloud setups. The good news is that these challenges are well-understood, and with the right approach and tools, you can overcome them. Let’s walk through some of the most common hurdles and discuss practical ways to solve them, turning potential frustrations into strengths for your security posture. By anticipating these issues, you can build a more resilient and effective program from the start.
Modern security tools generate a massive amount of data. While this information is valuable, managing it can be overwhelming without a good way to sort through the noise. When your team is flooded with endless alerts, it leads to fatigue, and critical threats can easily be missed. The key isn’t to gather less data, but to get smarter about how you process it.
The solution is to shift from simple scanning to intelligent vulnerability and threat prioritization. A strong exposure management platform helps you cut through the clutter by correlating asset information with real-world threat intelligence. It automatically identifies which vulnerabilities pose an immediate danger to your most critical assets, allowing your team to focus its energy where it counts.
Today’s IT environments are rarely simple. Most organizations operate with a mix of on-premises servers, private clouds, and multiple public cloud providers. This complexity makes it incredibly difficult to maintain a clear and complete picture of your attack surface. It’s hard to protect what you can’t see, and blind spots are where attackers thrive.
To solve this, you need a solution that provides complete visibility across your total attack surface. An effective platform unifies data from all your different environments into a single, comprehensive view. This allows you to discover and inventory assets no matter where they reside. By finding and fixing exposure gaps early, you can stop potential attackers before they have a chance to cause harm, even in the most complicated hybrid infrastructures.
Cybersecurity isn’t just a job for the security team. When IT, security, and development teams work in silos, communication breaks down, and remediation efforts stall. Security might identify a critical vulnerability, but if they can’t effectively communicate the risk and the required fix to the IT team that owns the asset, the exposure remains.
Exposure management is truly everybody’s thing. The best way to bridge these gaps is with a unified platform that serves as a single source of truth for all teams. When everyone is working from the same data, it’s easier to align on priorities and coordinate action. The right CTEM platform provides tailored dashboards and workflows for different roles, giving each team the context they need to collaborate effectively and fix issues faster.
Effective exposure management isn’t just about having the right tools; it’s about getting the right people to work together. When security, IT, and development teams operate in silos, it creates dangerous visibility gaps, slows down response times, and leaves the door open for attackers who thrive on this disconnect. Building a collaborative environment breaks down these barriers, turning a fragmented defense into a unified front. The goal is to create a system where every team understands its role in the security lifecycle, from discovery to remediation, and feels a sense of shared ownership. A platform that provides a unified view of cyber risks is the foundation for this collaboration, giving everyone a shared source of truth to work from. When teams are aligned around the same data and priorities, they can move faster, communicate more clearly, and ultimately reduce risk more effectively. This shift from isolated functions to an integrated security partnership is essential for building a resilient security posture that can stand up to modern threats. It transforms security from a bottleneck into a shared responsibility woven into the fabric of your operations.
True collaboration starts with a shared understanding of what you’re trying to protect and why. It’s not enough for the security team to have its own set of goals; these objectives must be integrated across the entire organization. To make this happen, leaders from different departments need to agree on the organization’s risk appetite and what a positive security culture looks like. As ISACA notes, “various executives across the enterprise must be aware of the organization’s risk appetite and have the right attitude toward cybersecurity.” Establish a cross-functional committee with members from IT, security, and business units to define these shared goals. This ensures that security isn’t seen as a blocker but as a business enabler that everyone is invested in.
Clear and consistent communication is the glue that holds a collaborative security strategy together. Instead of sending emails into a void or dropping reports in a shared drive, embed security communications into the workflows your teams already use. Integrating security alerts and remediation tickets directly into platforms like Jira, Slack, or Microsoft Teams makes security information visible and actionable. This approach “encourages vigilance and proactive behavior among employees” by making security a natural part of their daily tasks. When a critical vulnerability is found, the right developer should get an automatic notification in the tool they live in all day, complete with the context needed to fix it.
Identifying a vulnerability is only half the battle; fixing it requires seamless coordination between security and IT operations. A well-defined process for handoffs is critical. Once your security team uses a threat prioritization framework to identify what needs fixing first, there should be a clear, agreed-upon workflow for assigning the remediation task to the correct IT or DevOps team. Establishing Service Level Agreements (SLAs) for different severity levels can also ensure timely patching. This shared ownership model reinforces the idea that everyone plays a part in security. As one expert puts it, a strong culture “ensures that employees at all levels understand their role in protecting the organization and actively work to prevent security incidents.”
Your exposure management tools and processes are critical, but they don’t operate in a vacuum. The most resilient security postures are supported by a strong, security-aware culture where every employee understands their role in protecting the organization. Building this culture transforms your team from a potential vulnerability into your first line of defense, making security a collective effort rather than a siloed function. It’s about embedding security into the very fabric of your company’s daily operations and turning abstract policies into ingrained habits.
Forget the once-a-year, check-the-box training session. Effective security awareness is a continuous effort. Implement an ongoing program that includes regular phishing simulations, bite-sized training modules, and clear communications about emerging threats. Your training should be tailored to different roles—what your developers need to know about secure coding is different from what your finance team needs to know about invoice scams. The goal is to build a lasting cybersecurity culture that aligns with your company’s mission, where secure practices become second nature for everyone. This consistent reinforcement is far more effective than a single, overwhelming data dump.
People are central to any security strategy. Instead of creating a culture of fear around making mistakes, foster an environment where employees feel safe reporting potential incidents. If someone clicks on a suspicious link, you want them to report it immediately, not hide it for fear of blame. This approach speeds up your response time significantly. By providing ongoing support and accessible resources, you can address human vulnerabilities and reduce risk. Effective cyber security training for employees equips them to confidently protect sensitive data and support your security objectives.
Security isn’t just a job for the IT department; it’s a responsibility shared by every single person in the organization. To make this a reality, integrate security principles into everyday workflows and team goals. Leadership must champion this effort, consistently communicating that security is a top priority. When executives lead by example, it sets a powerful precedent. A well-established culture ensures that employees at all levels understand their role in preventing incidents. This collective ownership is fundamental to enhancing your organization’s cybersecurity culture and building a truly resilient defense.
An exposure management program is only as good as the results it delivers. But how do you know if your efforts are actually reducing risk? You can’t just rely on a gut feeling. Measuring your program’s success is essential for demonstrating its value, securing ongoing support, and continuously refining your strategy. By tracking the right metrics, you can move from simply managing vulnerabilities to making a measurable impact on your organization’s security posture.
This process involves more than just counting patched vulnerabilities. It’s about understanding your risk reduction over time and communicating that progress to key stakeholders. When you can clearly show how your work protects the business, you build trust and get the resources you need to keep improving. Let’s walk through how to define your metrics, evaluate your approach, and report on your wins.
You can’t hit a target you can’t see. The first step is to define what success looks like for your exposure management program. This means setting clear key performance indicators (KPIs) that connect directly to your security goals. Start with foundational metrics like Mean Time to Detect (MTTD) and Mean Time to Remediate (MTTR) for critical vulnerabilities. These are great for tracking operational efficiency.
From there, you can add metrics that show a broader impact. Consider tracking the reduction in critical exposures over time, the percentage of your attack surface that is actively monitored, or the number of security incidents tied to known but unpatched vulnerabilities. Identifying and measuring the right key metrics is the best way to get a clear picture of your program’s effectiveness and overall security readiness.
Exposure management isn’t a one-and-done project; it’s a continuous cycle. Your attack surface is always changing, and so are the threats targeting it. That’s why it’s so important to regularly review your performance against your KPIs and use that data to make your program better. Set a schedule—maybe quarterly—to sit down with your team and analyze the trends. Are your remediation times getting shorter? Are you discovering and securing new assets faster?
This evaluation process helps you spot what’s working and where you need to adjust. Perhaps a certain type of vulnerability is taking too long to fix, pointing to a bottleneck in your workflow. Or maybe your vulnerability prioritization criteria need tweaking to better reflect real-world threats. Fostering a culture of continuous improvement ensures your security practices evolve and stay effective.
Measuring your success is only half the battle; you also have to communicate it effectively. Reporting your progress to stakeholders—from the C-suite to your IT counterparts—is crucial for getting buy-in and demonstrating the value of your work. The key is to tailor your message to your audience. Executives want to see the big picture: how your efforts are reducing business risk and protecting the bottom line. Your technical teams, on the other hand, will need more granular data to guide their day-to-day work.
Use dashboards and clear visualizations to translate complex data into an easy-to-understand story. Instead of just listing the number of vulnerabilities patched, frame your results in terms of impact. For example, “This quarter, we reduced our exposure to active ransomware campaigns by 60%.” This kind of reporting doesn’t just justify your budget; it turns data into a powerful tool for driving improvement across the organization.
How is exposure management really different from the vulnerability management we already do? Think of it as a shift in perspective. Traditional vulnerability management often focuses on a list of known software flaws, or CVEs, and their technical severity scores. Exposure management takes a much broader view, looking at your organization through an attacker’s eyes. It considers any potential weakness an attacker could exploit—not just a CVE, but also a misconfigured cloud service, an exposed database, or a forgotten server. It’s less about a technical checklist and more about understanding the real-world risk to your business.
My team is already drowning in alerts. How does exposure management help with that instead of making it worse? This is a common concern, but a good exposure management program actually reduces noise, it doesn’t add to it. Instead of just giving you a longer list of potential problems, it provides the context to focus on what truly matters. By combining data about your critical assets with real-world threat intelligence, it helps you prioritize the handful of exposures that pose an immediate and significant danger. It turns that overwhelming flood of alerts into a short, manageable, and actionable to-do list.
This sounds great in theory, but what’s the first practical step to get started? The most important first step is to get a complete and accurate picture of your attack surface. You can’t protect what you don’t know you have. Before you can prioritize or remediate anything, you need a comprehensive inventory of all your digital assets, including servers, cloud instances, applications, and devices. Using an automated discovery tool to create this foundational map is the best way to begin, as it gives you the visibility needed to build the rest of your strategy.
How does this approach handle the complexity of hybrid and multi-cloud environments? Managing security across different environments is a huge challenge, and it’s exactly where exposure management shines. The key is to use a platform that unifies visibility across all your systems—on-premises, private cloud, and public cloud providers like AWS or Azure. Instead of trying to piece together data from separate, siloed tools, you get a single, comprehensive view of your entire attack surface. This allows you to spot and fix gaps that might otherwise be missed between environments.
How can I convince other teams, like IT and DevOps, to get on board with this? The best way to build collaboration is to create a shared sense of ownership. Frame the conversation around reducing business risk, not just checking off security tasks. A unified exposure management platform helps by providing a single source of truth that all teams can work from. When IT and DevOps can see the same risk-based priorities as the security team, it’s much easier to agree on what needs to be fixed first. It stops being a “security problem” and becomes a shared goal of protecting the organization.