 Hive Force Labs: Critical Threats Affecting You This Week - 5 Minute Audio Intelligence Report
Hive Force Labs: Critical Threats Affecting You This Week - 5 Minute Audio Intelligence Report Play Count: Loading...
Play Count: Loading... Hive Force Labs: Critical Threats Affecting You This Week - 5 Minute Audio Intelligence Report
Hive Force Labs: Critical Threats Affecting You This Week - 5 Minute Audio Intelligence Report Play Count: Loading...
Play Count: Loading...For a detailed threat digest, download the PDF file here
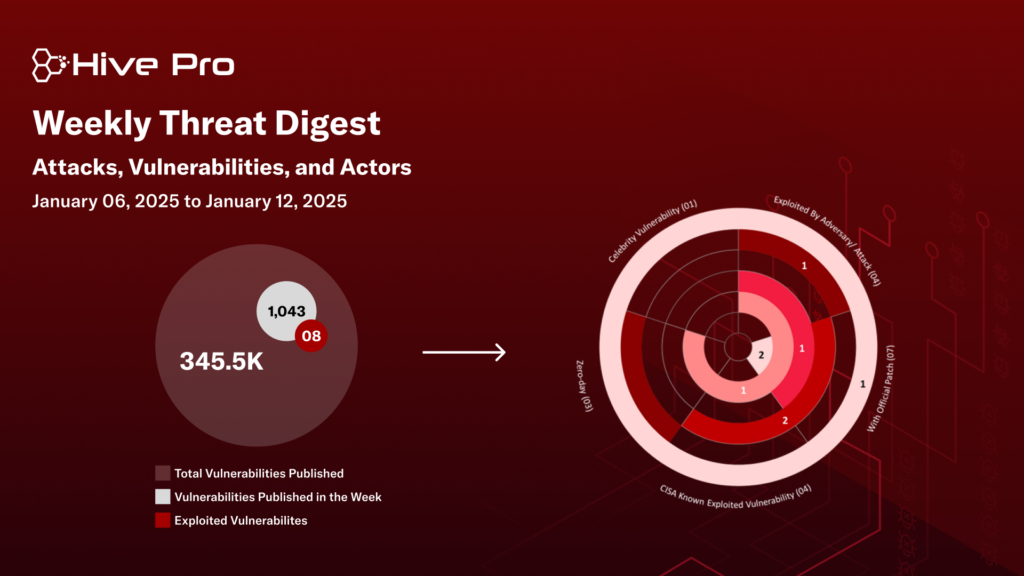
HiveForce Labs recently made several significant discoveries in the realm of cybersecurity threats. In the past week alone, ten attacks were executed, eight vulnerabilities were uncovered, and one active adversaries was identified, underscoring the persistent danger of cyberattacks.
HiveForce Labs has uncovered a significant security threat in which threat actors are exploiting CVE-2021-26855 in Microsoft Exchange Server to deploy the EAGERBEE backdoor, specifically targeting government organizations and internet service providers (ISPs) in the Middle East. Recent investigations revealed the use of a sophisticated service injector, designed to stealthily embed the backdoor into active system services, thereby improving its persistence and evasion capabilities. In addition, previously undocumented plugins are deployed after the backdoor installation, further complicating the detection and mitigation of the attack.
In parallel, critical vulnerabilities in Mitel MiCollab, including CVE-2024-41713, CVE-2024-55550, and CVE-2024-35286, have been identified, exposing organizations to significant risks. These vulnerabilities could allow unauthorized access, jeopardizing the confidentiality, integrity, and availability of affected systems. CVE-2024-41713 and CVE-2024-35286 can also be chained together, enabling more sophisticated attacks that could lead to system compromise, data theft, and disruption of enterprise operations. Additionally, the Gayfemboy botnet, an advanced Mirai variant exploiting a 0-day vulnerability in Four-Faith industrial routers, has been identified. With over 15,000 active nodes, this botnet has conducted massive DDoS attacks, peaking at 100GB of traffic, posing a growing and immediate risk to global users.
Subscribe to receive our weekly threat digests and newsletters directly in your inbox.