Comprehensive Threat Exposure Management Platform
Hive Pro recognized in Gartner® Magic Quadrant™ for Exposure Assessment Platform, 2025 Watch platform in action
Hive Pro is the industry’s only platform that implements Gartner’s defined CTEM framework end to end from Scoping, Discovery, Prioritization, Validation and Mobilization in one single platform.
Exposure Assessment and Breach & Attack Simulation in One platform- no more siloed operations.
Define the scope for exposure management for your assets and attack surfaces and strategically align it with business relevance from the outset
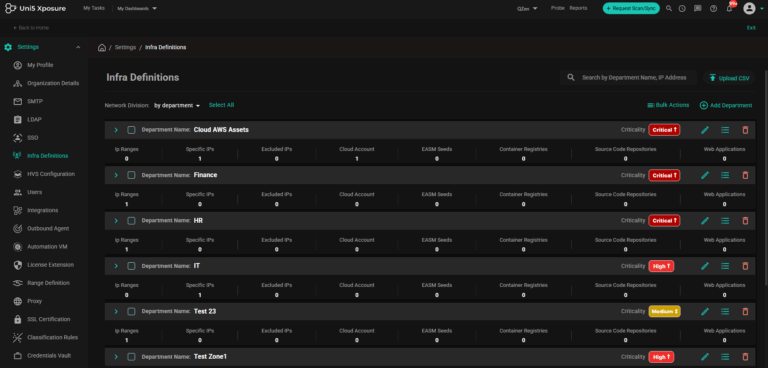
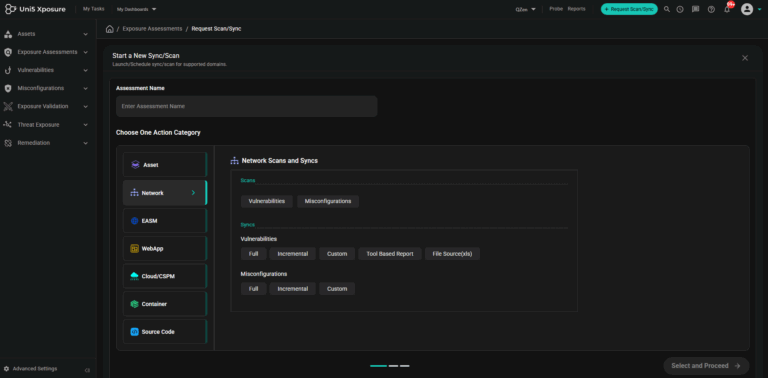
Discover assets, vulnerabilities, misconfigurations from code to cloud without logging onto multiple individual platforms. With Hive Pro platform, scans can be orchestrated across Qualys, Tenable, Rapid7, BurpSuite, etc and the results are ingested, de-duplicated, normalised and correlated automatically.
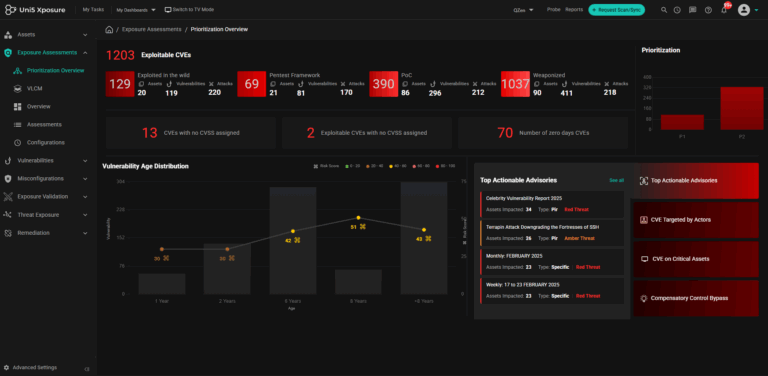
Prioritize the Top 3% of the vulnerabilities that represent imminent risk to your enterprise. Prioritize and Fix vulnerabilities that proactively stop attacks.
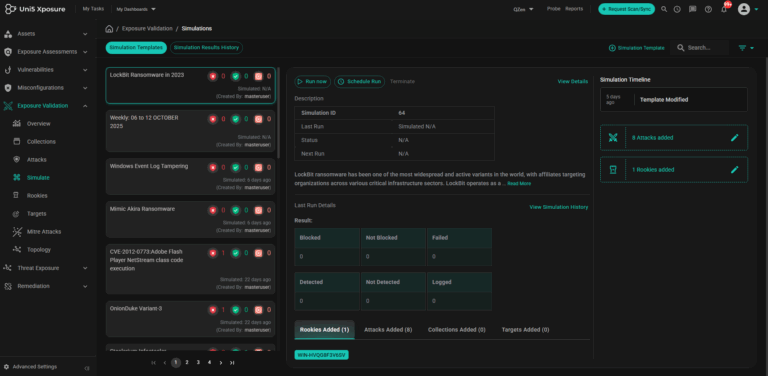
Don’t just speculate but validate the risk. Validate and further prioritise vulnerabilities through safe, real-world simulation of attack scenarios. Measure the effectiveness of existing security controls and assesses the reachability of attackers to your crown jewels, providing a definitive, actionable real risk score.
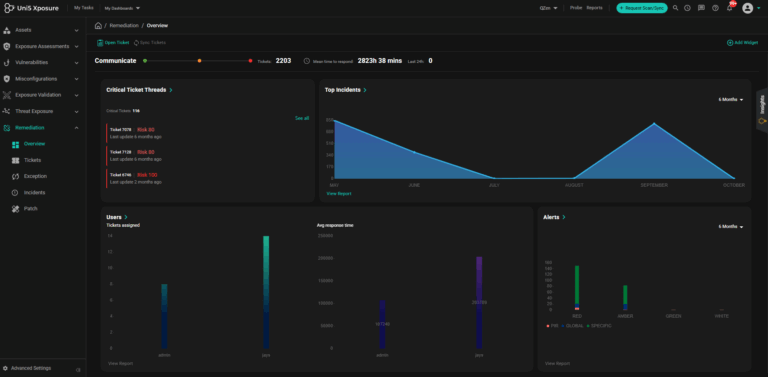
Auto-assign , reconcile tickets and track SLAs for remediation with your existing ITSM tools, send request for patching on patch management tools and push IOCs to Detection Platforms.

Define the scope for exposure management for your assets and attack surfaces and strategically align it with business relevance from the outset

Discover assets, vulnerabilities, misconfigurations from code to cloud without logging onto multiple individual platforms. With Hive Pro platform, scans can be orchestrated across Qualys, Tenable, Rapid7, BurpSuite, etc and the results are ingested, de-duplicated, normalised and correlated automatically.

Prioritize the Top 3% of the vulnerabilities that represent imminent risk to your enterprise. Prioritize and Fix vulnerabilities that proactively stop attacks.

Don’t just speculate but validate the risk. Validate and further prioritise vulnerabilities through safe, real-world simulation of attack scenarios. Measure the effectiveness of existing security controls and assesses the reachability of attackers to your crown jewels, providing a definitive, actionable real risk score.

Auto-assign , reconcile tickets and track SLAs for remediation with your existing ITSM tools, send request for patching on patch management tools and push IOCs to Detection Platforms.

Multiple scanners Tenable, Qualys, Rapid7, BurpSuite lead to operational complexity and a broken view of risks.
Fixing all High and Critical Vulnerabilities CVEs based on CVSS score alone is impractical and overwhelms the system.
Only compliance focused, no improvement in security posture. Security controls and attack path aren’t evaluated.
Fixing all high and critical vulnerabilities is time and resource consuming and lacks tangible security benefits.

Consolidate findings from multiple scanners in one platform. See and evaluate risk across the attack surface in one view.
Easy and dynamic prioritization of vulnerabilities based on risk and exposure.
Remediating vulnerabilities to fix the exposures and risks to increase cyber resilience against attacks. Security controls are validated and improved.
Fix less, secure more with low efforts yield maximum ROI and higher efficacy.


